802.1x network access control
The 7210 SAS supports network access control of client devices (PCs, STBs, and others) on an Ethernet network in accordance with the IEEE 802.1x standard (Extensible Authentication Protocol (EAP) over a LAN network or EAPOL).
Layer 2 control protocols affect 802.1x authentication behavior differently depending on the protocol in use; see Layer 2 control protocol interaction with authentication methods for more information.
802.1x modes
The 7210 SAS supports port-based network access control for Ethernet ports only. Every Ethernet port can be configured to operate in one of three different operation modes, controlled by the port-control parameter:
force-auth
Disables 802.1x authentication and causes the port to transition to the authorized state without requiring any authentication exchange. The port transmits and receives normal traffic without requiring 802.1x-based host authentication. This is the default setting.
force-unauth
Causes the port to remain in the unauthorized state, ignoring all attempts by the hosts to authenticate. The switch cannot provide authentication services to the host through the interface.
auto
Enables 802.1x authentication. The port starts in the unauthorized state, allowing only EAPOL frames to be sent and received through the port. Both the router and the host can initiate an authentication procedure, described as follows. The port will remain in an unauthorized state (no traffic except EAPOL frames is allowed) until the first client is authenticated successfully. After this, traffic is allowed on the port for all connected hosts.
802.1x basics
The IEEE 802.1x standard defines three participants in an authentication conversation:
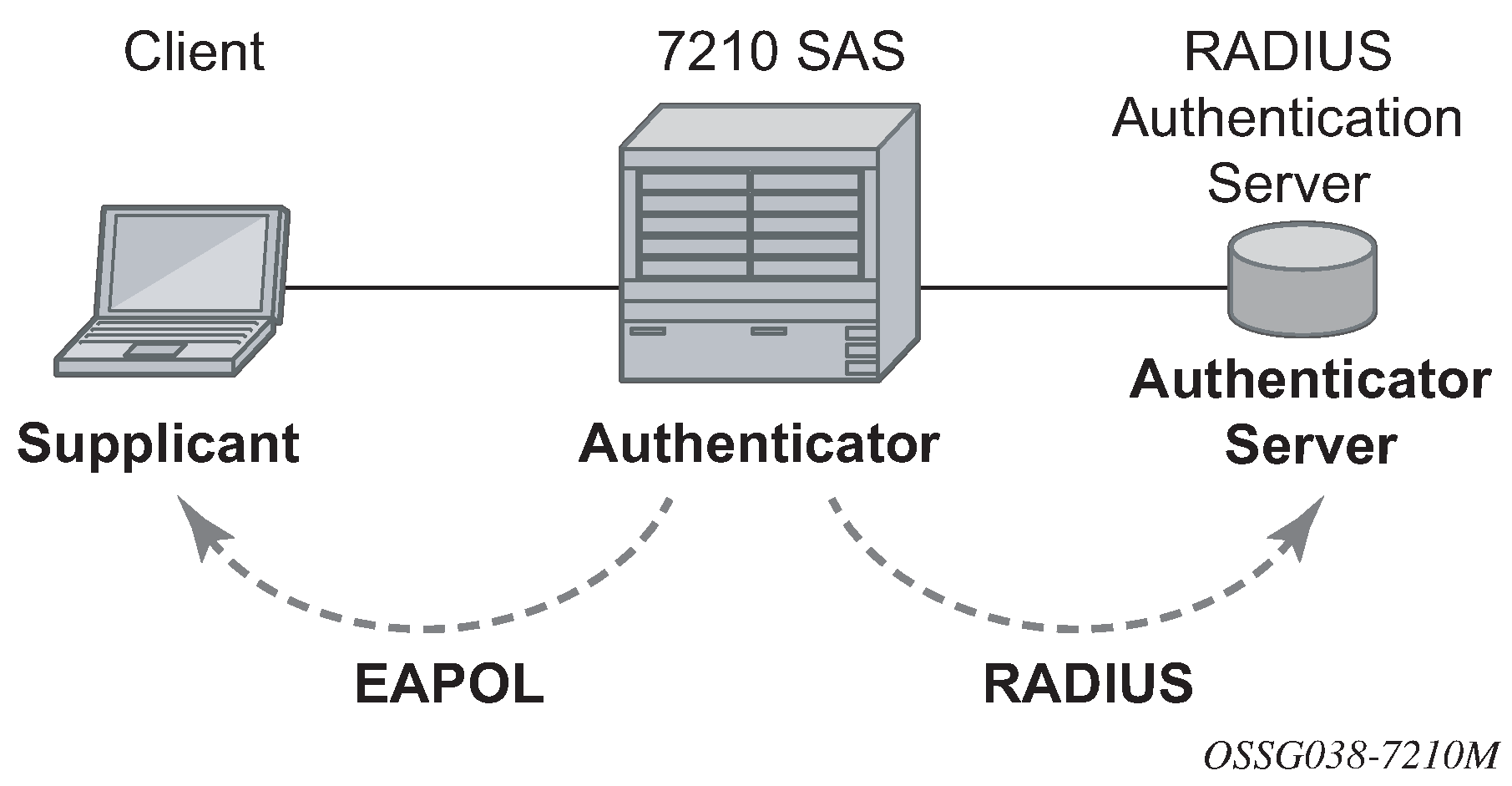
supplicant
This is the end-user device that requests access to the network.
authenticator
This participant controls access to the network. Both the supplicant and the authenticator are referred to as Port Authentication Entities (PAEs).
authentication server
This participant performs the actual processing of the user information.
The authentication exchange is carried out between the supplicant and the authentication server, the authenticator acts only as a bridge. The communication between the supplicant and the authenticator is done through the Extended Authentication Protocol (EAP) over LANs (EAPOL). On the back end, the communication between the authenticator and the authentication server is done with the RADIUS protocol. The authenticator is therefore a RADIUS client, and the authentication server a RADIUS server.
The following figure shows the 802.1x architecture.
The following figure shows the messages involved in the authentication procedure.
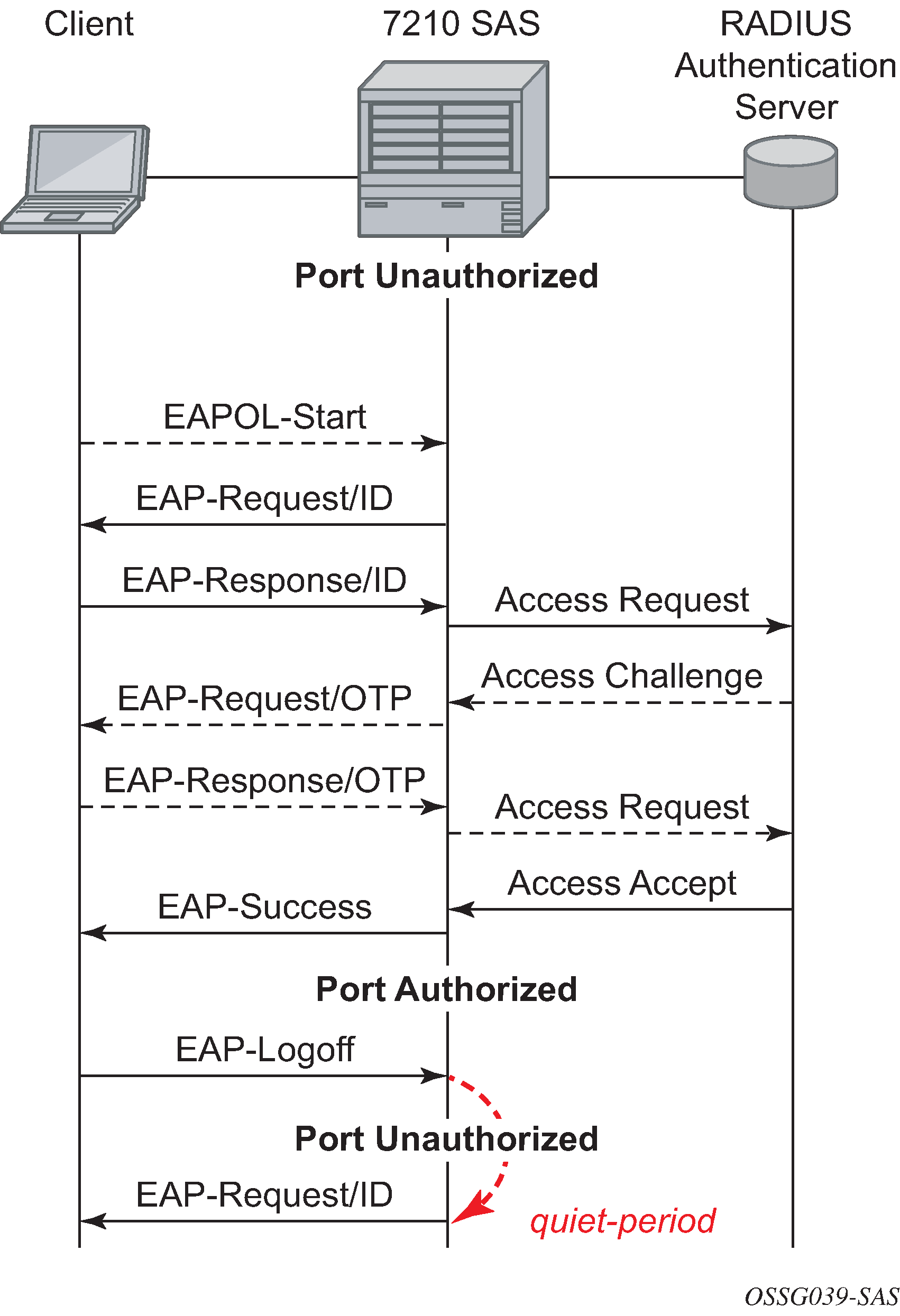
The router will initiate the procedure when the Ethernet port becomes operationally up, by sending a special PDU called EAP-Request/ID to the client. The client can also initiate the exchange by sending an EAPOL-start PDU, if it does not receive the EAP-Request/ID frame during bootup. The client responds on the EAP-Request/ID with a EAP-Response/ID frame, containing its identity (typically username + password).
After receiving the EAP-Response/ID frame, the router will encapsulate the identity information into a RADIUS AccessRequest packet, and send it off to the configured RADIUS server.
The RADIUS server checks the supplied credentials, and if approved will return an Access Accept message to the router. The router notifies the client with an EAP-Success PDU and puts the port in authorized state.
802.1x timers
The 802.1x authentication procedure is controlled by a number of configurable timers and scalars. There are two separate sets, one for the EAPOL message exchange and one for the RADIUS message exchange.
EAPOL timers:
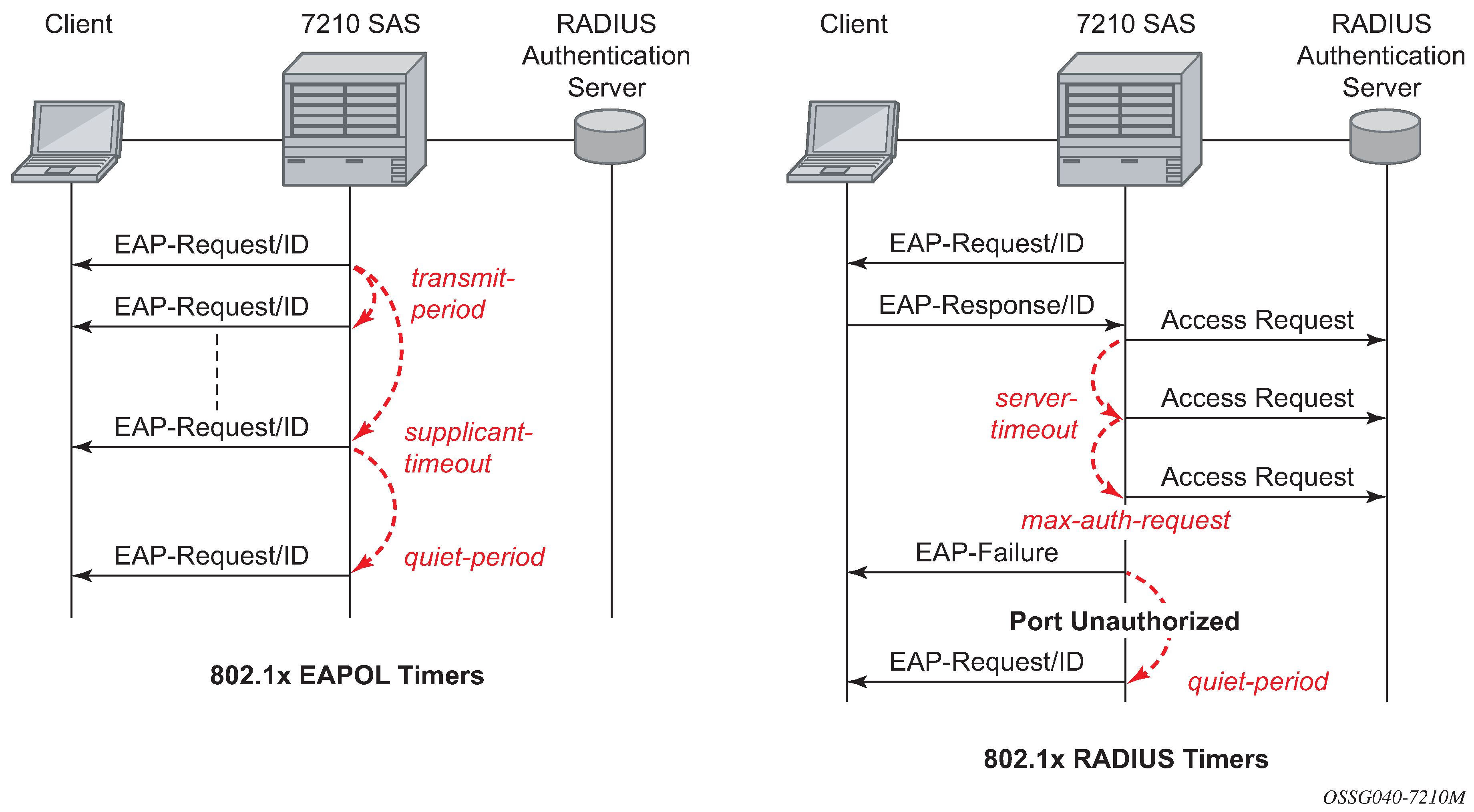
transit-period
Indicates how many seconds the Authenticator will listen for an EAP-Response/ID frame. If the timer expires, a new EAP-Request/ID frame will be sent and the timer restarted. The default value is 60. The range is 1 to 3600 seconds.
supplicant-timeout
This timer is started at the beginning of a new authentication procedure (transmission of first EAP-Request/ID frame). If the timer expires before an EAP-Response/ID frame is received, the 802.1x authentication session is considered as having failed. The default value is 30. The range is 1 to 300.
quiet-period
Indicates number of seconds between authentication sessions It is started after logout, after sending an EAP-Failure message or after expiry of the supplicant-timeout timer. The default value is 60. The range is 1 to 3600.
RADIUS timer and scaler:
max-auth-req
Indicates the maximum number of times that the router will send an authentication request to the RADIUS server before the procedure is considered as having failed. The default value is value 2. The range is 1 to 10.
server-timeout
Indicates how many seconds the authenticator will wait for a RADIUS response message. If the timer expires, the access request message is sent again, up to max-auth-req times. The default value is 60. The range is 1 to 3600 seconds.
The following figure shows sample EAPOL and RADIUS timers on the 7210 SAS.
The router can also be configured to periodically trigger the authentication procedure automatically. This is controlled by the enable re-authentication and reauth-period parameters. Reauth-period indicates the period in seconds (since the last time that the authorization state was confirmed) before a new authentication procedure is started. The range of reauth-period is 1 to 9000 seconds (the default is 3600 seconds, one hour). Note that the port stays in an authorized state during the re-authentication procedure.
802.1x configuration and limitations
Configuration of 802.1x network access control on the router consists of two parts:
generic parameters, which are configured under config>security>dot1x
port-specific parameters, which are configured under config>port>ethernet>dot1x
801.x authentication:
Provides access to the port for any device, even if only a single client has been authenticated.
Can only be used to gain access to a predefined Service Access Point (SAP). It is not possible to dynamically select a service (such as a VPLS service) depending on the 802.1x authentication information.
802.1x tunneling for Epipe service
Customers who subscribe to Epipe service considers the Epipe as a wire, and run 802.1x between their devices which are located at each end of the Epipe.
This feature only applies to port-based Epipe SAPs because 802.1x runs at port level not VLAN level. Therefore such ports must be configured as null encapsulated SAPs.
When 802.1x tunneling is enabled, the 802.1x messages received at one end of an Epipe are forwarded through the Epipe. When 802.1x tunneling is disabled (by default), 802.1x messages are dropped or processed locally according to the 802.1x configuration (shutdown or no shutdown).
Enabling 802.1x tunneling requires the 802.1x mode to be set to force-auth. Enforcement is performed on the CLI level.
MAC authentication
MAC authentication is only supported on 7210 SAS-Mxp, 7210 SAS-R6, 7210 SAS-Sx/S 1/10GE, and 7210 SAS-T.
The 7210 SAS supports the 802.1x EAP standard for authenticating Ethernet devices before they can access the network. However, if a client device does not support 802.1x EAP, MAC authentication can be used to prevent unauthorized traffic from being transmitted through the 7210 SAS.
Because MAC authentication is a fallback mechanism, the user must first enable 802.1x EAP to use MAC authentication on the 7210 SAS. To authenticate a port using MAC authentication, first configure 802.1x authentication on the 7210 SAS by enabling port-control auto, and then configure mac-auth on the 7210 SAS to enable MAC authentication.
Layer 2 control protocols affect MAC authentication behavior differently depending on the protocol in use; see Layer 2 control protocol interaction with authentication methods for more information.
MAC authentication basics
When a port becomes operationally up with MAC authentication enabled, the 7210 SAS (as the authenticator) performs the following steps:
After transmission of the first EAP-Request/ID PDU, the 7210 SAS starts the mac-auth-wait timer and begins listening on the port for EAP-Response/ID PDUs. At this point, the 7210 SAS only listens to EAPOL frames. If EAPOL frames are received, 802.1x authentication is chosen.
Note:If it is known that the attached equipment does not support EAP, you can configure no mac-auth-wait so that MAC authentication is used as soon as the port is operationally up.
If the mac-auth-wait timer expires, and no EAPOL frames have been received, the 7210 SAS begins listening on the port for any Ethernet frames.
If the 7210 SAS receives an Ethernet frame, the 7210 SAS scans the client source MAC address in the frame and transmits the MAC address to the configured RADIUS server for comparison against the MAC addresses configured in its database.
The following attributes are contained in the RADIUS message:
User-Name
This attribute specifies the source MAC address of the client device.
User-Password
This attribute specifies the source MAC address of the client device in an encrypted format.
Service-Type
This attribute specifies the type of service that the client has requested; the value is set to 10 (call-check) for MAC authentication requests.
Calling-Station-Id
This attribute specifies the source MAC address of the client device.
NAS-IP-Address
This attribute specifies the IP address of the device acting as the authenticator.
NAS-Port
This attribute specifies the physical port of the device acting as the authenticator.
Message-Authenticator
This attribute is used to authenticate and protect the integrity of Access Request messages to prevent spoofing attacks.
If the MAC address is approved by the RADIUS server, the 7210 SAS enables the port for traffic transmission by that particular MAC address, which is successfully authenticated.
If the MAC address is rejected by the RADIUS server, the 7210 SAS will not authenticate the port using either 802.1x or MAC authentication. If an Ethernet frame with the same MAC address is received, the 7210 SAS returns to step3 and reattempts approval of the MAC address.
If a port that was previously authenticated with MAC authentication receives an EAPOL-Start frame, the port will not reauthenticate using 802.1x EAPOL.
While the port is unauthenticated, the port will be down to all upper layer protocols or services.
When a MAC address is authenticated, only packets whose source MAC address matches the authenticated MAC address are forwarded when the packets are received on the port, and only packets whose destination MAC address matches the authenticated MAC address are forwarded out of the port.
Broadcast and multicast packets at ingress are sent for source MAC address authentication. Broadcast and multicast packets at egress are forwarded as normal.
Unknown destination packets at ingress are copied to the CPU and MAC authentication is attempted. Unknown destination packets at egress are dropped.
MAC authentication limitations
MAC authentication is subject to the following limitations:
If MAC authentication is configured on ports that are part of a LAG, the authenticated MAC address is forwarded in the egress direction out of any port in the LAG.
If MAC authentication is configured on a port and the port is added to or removed from a LAG, all previously authenticated MACs are reauthenticated by the system.
Caution:A small amount of traffic loss may occur while MAC reauthentication is in progress.
VLAN authentication
VLAN authentication is only supported on 7210 SAS-Mxp, 7210 SAS-R6, 7210 SAS-Sx/S 1/10GE, and 7210 SAS-T.
The 7210 SAS supports VLAN authentication, which operates similarly to 802.1x network access control but only uses VLAN-tagged EAPOL frames to trigger the authentication process on a per-VLAN basis, or uses null-tagged EAPOL frames to authenticate and authorize processing of service traffic received in the context of a Dot1q explicit null SAP. See 802.1x network access control for information about 802.1x network access control and authentication.
To authenticate a port using VLAN authentication, you must first configure 802.1x authentication on the 7210 SAS by enabling port-control auto, and then configure vlan-auth on the 7210 SAS to enable VLAN authentication and allow VLAN authentication functionality to supersede that of basic 802.1x authentication.
VLAN authentication and MAC authentication are mutually exclusive. MAC authentication cannot be configured on a port while VLAN authentication is already configured on the same port. See MAC authentication for information about MAC authentication.
Layer 2 control protocols affect VLAN authentication behavior differently depending on the protocol in use; see Layer 2 control protocol interaction with authentication methods for more information.
VLAN authentication basics
When a port becomes operationally up with VLAN authentication enabled, the 7210 SAS (as the authenticator) performs the following steps:
After transmission of the first EAP-Request/ID PDU, the 7210 SAS begins listening on the port for VLAN-tagged EAPOL Start, Request-Identity frames from the access device connected to the port. Null-tagged EAPOL frames also trigger the authentication process if a Dot1q explicit null SAP is configured.
If the 7210 SAS receives a VLAN-tagged EAPOL frame (or a null-tagged EAPOL frame if a Dot1q explicit null SAP is configured), the 7210 SAS transmits the frame to the configured RADIUS server for comparison of the VLAN against the usernames configured in its database.
The User-Name attribute is contained in the RADIUS message. This attribute specifies the username received in the EAPOL frame from the client device.
If the VLAN is approved by the RADIUS server, the 7210 SAS maps all traffic received from the VLAN to a SAP and processes it in the context of the configured service.
If the VLAN is rejected by the RADIUS server, all traffic from the VLAN is dropped. The 7210 SAS enters a quiet period, configured using the quiet-period command, and will not authenticate the port using VLAN authentication. After the quiet period expires, the 7210 SAS returns to step1.
While the port is unauthenticated, the port will be down to all upper layer protocols or services.
VLAN authentication limitations
VLAN authentication is subject to the following limitations:
VLAN authentication is only supported on Dot1q-encapsulated ports. It is not supported on NULL or QinQ-encapsulated ports.
VLAN authentication only uses the outermost VLAN tag received in the packets. Packets with more than one tag are processed only if the outermost tag matches the SAP tag.
Restrictions on processing of SAP tags also apply to VLAN authenticated frames. VLAN authentication does not change the current behavior for frames mapped to different SAPs and services.
VLAN range SAPs are not supported on a port with VLAN authentication enabled.
Dot1q default SAPs configured on a port with Dot1q encapsulation do not support VLAN authentication.
Dot1q explicit null SAPs can be configured on a port with Dot1q encapsulation, which requires authentication of null-tagged EAPOL frames.
Layer 2 control protocol interaction with authentication methods
The following table describes the interactions of Layer 2 control protocols with 802.1x authentication, MAC authentication, and VLAN authentication.
Layer 2 control protocol |
802.1x port authentication enabled |
MAC authentication enabled |
VLAN authentication enabled |
|
|---|---|---|---|---|
Dot1q explicit null SAP not configured |
Dot1q explicit null SAP configured |
|||
EFM OAM |
Allow |
Allow |
Allow |
Allow |
LLDP |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
Allow |
Allow |
LACP |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
LAG and LACP are not supported on ports with VLAN authentication enabled |
LAG and LACP are not supported on ports with VLAN authentication enabled |
CFM |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
Block if VLAN (SAP) is unauthenticated Allow only if specific VLAN is authenticated |
Block if null SAP is unauthenticated Allow if null SAP is authenticated |
xSTP (STP/RSTP/MSTP) |
Block if port is unauthenticated Allow if port is authenticated |
Block if MAC is unauthenticated Allow if MAC is authenticated |
Block if VLAN (SAP) is unauthenticated Allow if VLAN (SAP) is authenticated |
Block if null SAP is unauthenticated Allow if null SAP is authenticated |