WiFi Aggregation and Offload — Basic Secure SSID with Distributed RADIUS Proxy
This chapter provides information about WiFi Aggregation and Offload — Basic Secure SSID with Distributed RADIUS Proxy.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 13.0.R3.
WiFi Aggregation and Offload functionality has been supported in SR OS 10.0.R3, and later. This includes a RADIUS proxy server and support for soft-GRE tunnels.
Overview
WLAN-GW subscribers can be implemented using Enhanced Subscriber Management (ESM) on the CPM in order to benefit from the extensive ESM features available on the SR OS nodes. Many different WiFi Offload configurations are possible, with two versatile categories being open and secure SSID.
Starting from SR OS Release 12.0.R4, distributed RADIUS-proxy functionality (DRP) has been added to the MS-ISA. This feature allows running a high-performance proxy over multiple MS-ISA cards instead of being limited to a single CPM, greatly increasing scalability.
This chapter can be used as a starting point for operators who wish to configure a secure SSID scenario using DRP and ESM. In a secure SSID scenario, the Access Point (AP) uses 802.1x and Extensible Authentication Protocol (EAP) to authenticate the UE. The EAP method used is transparent to the WLAN-GW. In this chapter, PEAP/EAP-MSCHAPv2 is used to associate with the SSID by entering a user name and password, but other methods such as EAP-Subscriber Identity Module (EAP-SIM) can also be used without any configuration change on the WLAN-GW.
IP address assignment and Internet connectivity can be achieved by using various methods on the SR OS node. In this scenario, the RADIUS server provides the IP addresses to the User Equipment (UEs). The same IP private address is assigned to every UE and L2-aware Network Address Translation (NAT) is used to provide a public IP address on the Internet.
For a WiFi Offload solution where the service provider has a record of their users, that is, where users have login accounts, the provider may consider offering a secure SSID as a more convenient and secure alternative to an open SSID with a web portal. In a secure SSID scenario, all user traffic is encrypted between the UE and the AP, and UEs are only granted access if they authenticate successfully. This makes attacks more difficult and blocks non-paying users who only connect to test if they can get free access.
Authentication in this case requires a centralized Authentication, Authorization and Accounting (AAA) which keeps track of the user accounts. The user is granted full access immediately after connecting to the secure SSID. One drawback is that WiFi clients may need some configuring by the user before they are able to connect to the SSID using the correct EAP method. In the case of EAP-SIM, users do not need to know their user name and password because authentication is done based on credentials contained in the SIM card, but the SSID configuration may need to be preloaded by the operator on the mobile device or provided to the user ahead of time. For other EAP methods such as PEAP/EAP-MSCHAPv2, users need to supply the correct user name and password, without the help of a portal or any instructions to guide them.
An operator offering Internet access to a large number of users while only a limited number of public IP addresses are available will likely use Network Address Translation (NAT) in order to conserve public IP addresses. NAT typically maps a few public IP addresses and ports to a large number of inside (private) IP addresses and ports. The WLAN-GW supports several NAT configurations including L2-aware NAT, where the MAC address of the UE is also used when creating the mapping between the inside IP/port and the outside IP/port. Therefore with L2-aware NAT, the same private IP address can be assigned to all UEs because the unique MAC address for each UE allows the WLAN-GW to distinguish between each UE. This greatly simplifies IP address assignment; the RADIUS server can assign the same private IP address to all UEs and there is no DHCP server required. Using a RADIUS server for IP address assignment means DHCP proxy needs to be configured on the WLAN-GW.
The SR OS platform is flexible in terms of allowing the operator to separate the various WiFi Offload functions between different routing instances. All functions can be configured in the same routing instance, or as shown in the following configuration, the connectivity to the APs (and soft-GRE tunnels) can be provided in one Virtual Private Routed Network (VPRN), the users can be instantiated in another VPRN, and AAA access can be provided in yet another routing instance (in this example the Base router). This provides a clear separation of functions and can enhance security, by separating user traffic from authentication and management traffic.
Configuration
The WiFi offload scenario with SSID and L2-aware NAT shown in WiFi Offload Scenario with Secure SSID and L2-Aware NAT has following characteristics:
Secure SSID with EAP authentication
Local breakout to Internet, routing through the Base routing instance
Same private IP address assigned to all UEs by RADIUS
L2-aware NAT
AP access in VPRN 1000
UEs terminated in VPRN 2001
Figure 1. WiFi Offload Scenario with Secure SSID and L2-Aware NAT 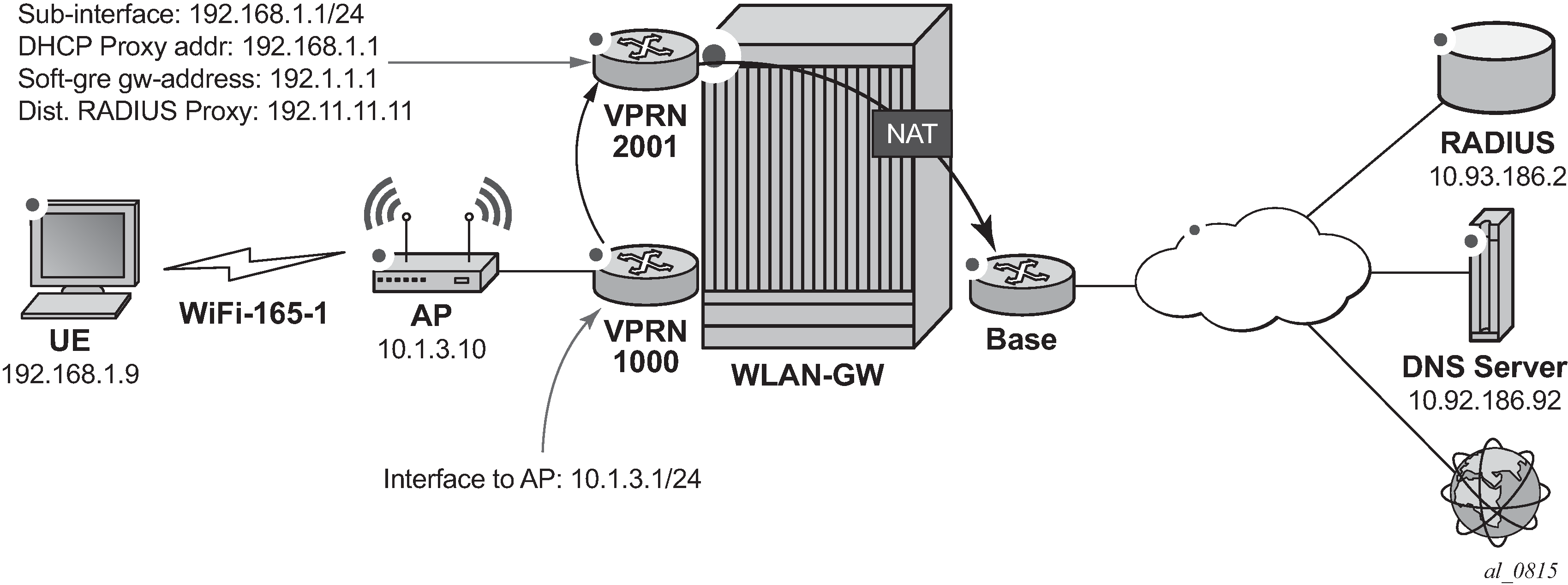
WLAN-GW
Note that configuring the uplink interface, Interior Gateway Protocol (IGP) and system configuration is outside the scope of this chapter and only partial configuration is provided.
Card and Media Dependent Adapter (MDA) configuration showing only the WLAN-IOM. An IOM card containing two MS-ISA cards provides the WLAN-GW functionality. The MDA type for the ISA cards is isa-bb, the same type that is used for NAT.
*A:WLAN-GW# /configure card 2
*A:WLAN-GW>config>card# info
----------------------------------------------
card-type iom3-xp-b
mda 1
mda-type isa-bb
no shutdown
exit
mda 2
mda-type isa-bb
no shutdown
exit
no shutdown
----------------------------------------------
The ISA configuration contains a wlan-gw-group referencing the IOM in slot 2, which hosts the two MS-ISA cards providing the WLAN-GW functions.
A:WLAN-GW# /configure isa
A:WLAN-GW>config>isa# info
----------------------------------------------
wlan-gw-group 1 create
active-iom-limit 1
iom 2
no shutdown
exit
----------------------------------------------
The AAA configuration contains an ISA RADIUS policy used for authentication requests. The source address range configures the source address of the first MS-ISA in the wlan-gw-group. The second MS-ISA card gets the next consecutive IP address and so on. All the IP addresses assigned this way to MS-ISA cards must be configured as clients on the RADIUS server. The secret here must match the secret configured on the RADIUS server.
A:WLAN-GW# /configure aaa
A:WLAN-GW>config>aaa# info
----------------------------------------------
isa-radius-policy "IRS_1" create
servers
router "Base"
source-address-range 10.10.165.1
server 1 create
authentication
ip-address 10.93.186.2
secret "7USmr6f7JkxaGnDDq1uqwEAJKGbhZr5i" hash2
no shutdown
exit
exit
exit
----------------------------------------------
The following policy shows the two routes that must be exported for this scenario to work: UE NAT outside routes (NAT is configured in the next step), to make UEs reachable on the Internet, and MS-ISA RADIUS source address routes, in order for the MS-ISAs to be reachable from the RADIUS server. This policy should be used for export in the IGP configuration (not shown).
A:WLAN-GW# /configure router policy-options
A:WLAN-GW>config>router>policy-options# info
----------------------------------------------
prefix-list "WiFi"
prefix 10.10.165.0/24 longer
prefix 10.165.0.0/16 longer
exit
policy-statement "WiFi"
entry 10
from
prefix-list "WiFi"
exit
action accept
exit
exit
exit
----------------------------------------------
The following configures L2-aware NAT by creating an outside NAT pool with a public IP address range. The private inside address used by the UE will be mapped to an outside IP address routable on the Internet. NAT port mapping parameters can be set in this configuration, controlling how many outside ports can be used by each UE. Details of NAT configuration are outside the scope of this document.
A:WLAN-GW# /configure router nat
A:WLAN-GW>config>router>nat# info
----------------------------------------------
outside
pool "WiFi-165-1" nat-group 1 type l2-aware create
address-range 10.165.1.0 10.165.1.255 create
exit
no shutdown
exit
exit
----------------------------------------------
The following configures a NAT policy under services, linking this policy with the outside NAT pool. When the NAT policy is invoked for a subscriber, this associates the subscriber with the correct outside pool.
A:WLAN-GW# /configure service nat
A:WLAN-GW>config>service>nat# info
----------------------------------------------
nat-policy "WiFi-165-1" create
pool "WiFi-165-1" router Base
exit
----------------------------------------------
The following subscriber management configuration includes an SLA profile, a subscriber identity policy, and the subscriber profile that makes use of the previously defined NAT policy. This allows subscriber traffic to be forwarded to the Internet through the Base routing instance where the outside NAT pool exists.
A dummy authentication-policy is required for the CPM to handle the DHCP Discover messages forwarded by the MS-ISA cards.
A:WLAN-GW# /configure subscriber-mgmt
A:WLAN-GW>config>subscr-mgmt# info
----------------------------------------------
authentication-policy "dummy-auth-policy" create
exit
sla-profile "SLAP_1" create
exit
sub-profile "SUBP_1" create
nat-policy "WiFi-165-1"
exit
sub-ident-policy "SIP" create
sub-profile-map
use-direct-map-as-default
exit
sla-profile-map
use-direct-map-as-default
exit
exit
----------------------------------------------
VPRN 1000 contains the interface to the AP as well as the distributed RADIUS proxy server RP_1. The RADIUS proxy wlan-gw address configures a special NAT route in VPRN 1000 that forwards RADIUS packets from the AP to the correct MS-ISA. That address is known to the AP as the RADIUS server address it uses for EAP authentication for this SSID. The secret configured here has to match the RADIUS secret configured on the AP.
The RADIUS proxy is configured to create cache entries based on attribute 31 in RADIUS access-request packets (Calling-Station-ID), which contains the MAC address of the UE. These cache entries will be stored temporarily and used to authenticate DHCP packets from the UE. The track-accounting start parameter allows mobility to be triggered for a UE upon receiving an accounting-start message. The UE’s associated tunnel will be moved to the IP address indicated by the NAS-IP-Address. The track-accounting stop parameter allows the UE session to be terminated immediately when the AP sends a RADIUS accounting-stop for the UE, when this UE disconnects from the SSID.
The default-authentication-server-policy links the RADIUS proxy with the isa-radius-policy that authenticates the UEs. If accounting is required, the accounting policy can be specified in this configuration and can be the same as or different from the isa-radius-policy. The send-accounting-response option makes the WLAN-GW acknowledge (and then discard) the RADIUS accounting messages from the AP, instead of proxying the accounting messages to the external RADIUS server.
A:WLAN-GW# /configure service vprn 1000
A:WLAN-GW>config>service>vprn# info
----------------------------------------------
route-distinguisher 65400:1000
interface "toAP3" create
address 10.1.3.1/24
sap 1/1/10 create
exit
exit
radius-proxy
server "DRP_1" purpose accounting authentication wlan-gw-group 1 create
cache
key packet-type request attribute-type 31
track-accounting start stop
no shutdown
exit
default-authentication-server-policy "IRS_1"
secret "nUeorYjgFZtuAqIwoUOLODFxF43rhSf/" hash2
send-accounting-response
wlan-gw
address 192.11.11.11
exit
no shutdown
exit
exit
no shutdown
----------------------------------------------
VPRN 2001 is used for UE termination and contains:
A subscriber interface and group interface of type wlangw (soft-gre prior to Release 12.0).
Default subscriber parameters assigned to every UE.
DHCP proxy, which allows the RADIUS-assigned IP address parameters stored in the DRP cache during authentication to be passed to the UE.
A dummy authentication policy which allows the CPM to handle the DHCP Discover passed on by the MS-ISA.
The wlan-gw node (soft-gre prior to Release 12.0), which includes:
The gw-address that is the end-point of the GRE tunnel
The routing instance where AP traffic is terminated
The ISA wlan-gw-group, which associates this WLAN-GW configuration with a set of IOMs
Mobility parameters, which allow the UE state to be kept if the UE moves between two APs broadcasting the same SSID
The authenticate-on-dhcp option required for the CPM to instantiate ESM UEs when using DRP
The L2-aware address/subnet used for L2-aware NAT. This address matches the default gateway assigned to the UEs.
A:WLAN-GW# /configure service vprn 2001 A:WLAN-GW>config>service>vprn# info ---------------------------------------------- description "WiFi-165-1 Secure SSID" route-distinguisher 65400:2001 subscriber-interface "SI1" create address 192.168.1.1/24 populate-host-routes group-interface "GI1" wlangw create sap-parameters sub-sla-mgmt def-sla-profile "SLAP_1" def-sub-profile "SUBP_1" sub-ident-policy "SIP" exit exit dhcp proxy-server emulated-server 192.168.1.1 no shutdown exit lease-populate 10000 gi-address 192.168.1.1 no shutdown exit authentication-policy "dummy-auth-policy" wlan-gw gw-address 192.1.1.1 mobility trigger data iapp exit router 1000 wlan-gw-group 1 vlan-tag-ranges range default authenticate-on-dhcp exit exit no shutdown exit exit exit nat inside l2-aware address 192.168.1.1/24 exit exit exit no shutdown ----------------------------------------------
Freeradius
This part of the user’s configuration file matches on the user name entered by the UE while connecting to this secure SSID. If the password entered is correct, RADIUS returns the IP addressing parameters configured as follows. The same IP address 192.168.1.9 is assigned to every user on this SSID, but the L2-aware NAT on the WLAN-GW can distinguish between all the UEs based on their L2 MAC address.
/etc/freeradius/users:
"user1" User-Password := "alcatel"
Alc-Subsc-ID-Str = "%{User-Name}",
Alc-Default-Router = 192.168.1.1,
Alc-Primary-Dns = 10.43.186.43,
Framed-IP-Address = 192.168.1.9,
Framed-IP-Netmask = 255.255.255.0,
In /etc/freeradius/clients.conf the secret matches the one configured in the WLAN-GW isa-radius-policy configuration. Since there are only two MS-ISA cards in the wlan-group used in this example, two clients are configured.
client 10.10.165.1 {
secret = alcatel
shortname = WLAN-GW-ISA1
}
client 10.10.165.2 {
secret = alcatel
shortname = WLAN-GW-ISA2
}
Access Points
The following must be configured on the Access Point as a minimum:
IP address 10.1.3.10/24
Default route to 10.1.3.1
Secure SSID WiFi-165-1 mapped to VLAN 10, using WPA2 with EAP/802.1x authenticating against RADIUS server 192.11.11.11, with RADIUS accounting enabled
Soft-GRE tunnel with destination 192.1.1.1, with VLAN 10 mapped to this tunnel
Show Commands
The following show commands reflect the status of the WLAN-GW after the UE has connected and obtained and IP address using DHCP.
The following output displays the connected UEs:
A:WLAN-GW# show subscriber-mgmt wlan-gw ue
===============================================================================
User Equipments
===============================================================================
MAC address : 68:7f:74:8b:3d:d7
-------------------------------------------------------------------------------
VLAN Q-tag : 10
MPLS label : (Not Specified)
Tunnel router : 1000
Tunnel remote IP address : 10.1.3.10
Tunnel local IP address : 192.1.1.1
Retail service : N/A
SSID : "WiFi-165-1"
Previous Access Point IP : (Not Specified)
IMSI : (Not Specified)
Subscriber host service : 2001
Subscriber host SAP : 2/1/nat-out-ip:2049.1
Last move time : 2015/09/15 16:20:01
-------------------------------------------------------------------------------
No. of UE: 1
===============================================================================
A:WLAN-GW# tools dump wlan-gw ue
===============================================================================
Matched 1 session on Slot #2 MDA #1
===============================================================================
UE-Mac : 68:7f:74:8b:3d:d7 UE-vlan : 10
UE IP Addr : N/A UE Timeout : N/A
DHCPv6 Timeout : N/A SLAAC Timeout : N/A
DHCPv6 IA-NA ID : N/A RA Timeout : N/A
DHCPv6 Addr : N/A
SLAAC Prefix : N/A
Description : ESM-user
Auth/CoA-time : 09/16/2015 10:47:38 Retail Service : N/A
Tunnel MDA : 2/2 Tunnel Router : 1000
MPLS label : N/A Shaper : 1
Tunnel Src IP : 10.1.3.10 Tunnel Dst IP : 192.1.1.1
Tunnel L2 Svc : N/A Tunnel L2 Vlan : N/A
Tunnel Type : GRE
Anchor SAP : 2/1/nat-out-ip:2049.2
AP-Mac : 00:0d:67:39:0b:65 AP-RSSI : Unknown
AP-SSID : "WiFi-165-1"
Last-forward : 09/16/2015 15:59:26 Last-move : 09/16/2015 10:47:38
Session Timeout : None Idle Timeout : N/A
Acct Update : None Acct Interval : N/A
Acct Session-Id : N/A
Acct Policy : N/A
NAT Policy : N/A
Redirect Policy : N/A
IP Filter : N/A
App-profile : N/A
Rx Oper PIR : N/A Rx Oper CIR : N/A
Tx Oper PIR : N/A Tx Oper CIR : N/A
Rx Frames : N/A Rx Octets : N/A
Tx Frames : N/A Tx Octets : N/A
-------------------------------------------------------------------------------
===============================================================================
No sessions on Slot #2 MDA #2 match the query
The DHCP lease information indicates that the address was assigned by RADIUS.
A:WLAN-GW# show service id 2005 dhcp lease-state
===============================================================================
DHCP lease state table, service 2001
===============================================================================
IP Address Mac Address Sap/Sdp Id Remaining Lease MC
LeaseTime Origin Stdby
-------------------------------------------------------------------------------
192.168.1.9 68:7f:74:8b:3d:d7 [2/1/nat-out-ip:20* 06d23h59m Radius
-------------------------------------------------------------------------------
Number of lease states : 1
===============================================================================
* indicates that the corresponding row element may have been truncated.
When troubleshooting DHCP issues, displaying DHCP statistics is useful.
A:WLAN-GW# show service id 2005 dhcp statistics
====================================================================
DHCP Global Statistics, service 2001
====================================================================
Rx Packets : 2
Tx Packets : 2
Rx Malformed Packets : 0
Rx Untrusted Packets : 0
Client Packets Discarded : 0
Client Packets Relayed : 0
Client Packets Snooped : 0
Client Packets Proxied (RADIUS) : 2
Client Packets Proxied (Diameter) : 0
Client Packets Proxied (User-Db) : 0
Client Packets Proxied (Lease-Split) : 0
Server Packets Discarded : 0
Server Packets Relayed : 0
Server Packets Snooped : 0
DHCP RELEASEs Spoofed : 0
DHCP FORCERENEWs Spoofed : 0
====================================================================
The following output lists the active subscribers, showing each UE SLA profile, MAC address and IP address.
A:WLAN-GW# show service active-subscribers
===============================================================================
Active Subscribers
===============================================================================
-------------------------------------------------------------------------------
Subscriber DUACBU2ZLE (SUBP_1)
-------------------------------------------------------------------------------
NAT Policy: WiFi-165-1
Outside IP: 10.165.1.0
Ports : 1024-65535
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
(1) SLA Profile Instance sap:[2/1/nat-out-ip:2049.1] - sla:SLAP_1
-------------------------------------------------------------------------------
IP Address
MAC Address PPPoE-SID Origin
--------------------------------------------------------
192.168.1.9
68:7f:74:8b:3d:d7 N/A DHCP
-------------------------------------------------------------------------------
Number of active subscribers : 1
-------------------------------------------------------------------------------
The following output displays distributed RADIUS proxy server statistics after the UE has authenticated, showing all the EAP messages exchanged between the AP and RADIUS proxy:
A:WLAN-GW# show router 1000 radius-proxy-server "DRP_1" statistics
===============================================================================
ISA RADIUS Proxy server statistics for "DRP_1"
===============================================================================
Group 1 member 1
-------------------------------------------------------------------------------
Rx packet : 12
Rx Access-Request : 11
Rx Accounting-Request : 1
Rx dropped : 0
Retransmit : 0
Wrong purpose : 0
No UE MAC to cache : 0
Client context limit reached : 0
No ISA RADIUS policy configured : 0
Invalid attribute encoding : 0
Invalid password : 0
Accounting-Request with invalid Acct-Status-Type : 0
Accounting-Request with no Acct-Status-Type : 0
Invalid accounting Authenticator : 0
Invalid Message-Authenticator : 0
Management core overload : 0
Tx Access-Accept : 1
Tx Access-Reject : 0
Tx Access-Challenge : 10
Tx Accounting-Response : 1
Tx dropped : 0
Server timeout : 0
Invalid response Authenticator : 0
Invalid Message-Authenticator : 0
Invalid attribute encoding : 0
RADIUS server send failure : 0
Group 1 member 2
-------------------------------------------------------------------------------
Rx packet : 0
Rx Access-Request : 0
Rx Accounting-Request : 0
Rx dropped : 0
Retransmit : 0
Wrong purpose : 0
No UE MAC to cache : 0
Client context limit reached : 0
No ISA RADIUS policy configured : 0
Invalid attribute encoding : 0
Invalid password : 0
Accounting-Request with invalid Acct-Status-Type : 0
Accounting-Request with no Acct-Status-Type : 0
Invalid accounting Authenticator : 0
Invalid Message-Authenticator : 0
Management core overload : 0
Tx Access-Accept : 0
Tx Access-Reject : 0
Tx Access-Challenge : 0
Tx Accounting-Response : 0
Tx dropped : 0
Server timeout : 0
Invalid response Authenticator : 0
Invalid Message-Authenticator : 0
Invalid attribute encoding : 0
RADIUS server send failure : 0
===============================================================================
The following output shows the ISA RADIUS policy statistics after the UE has connected, showing the transactions between the WLAN-GW and the RADIUS server.
A:WLAN-GW# show aaa isa-radius-policy "IRS_1"
===============================================================================
ISA RADIUS policy "IRS_1"
===============================================================================
Description : (Not Specified)
Include attributes acct : N/A
Include attributes auth : nas-ip-address
User name format : mac
User name MAC format : alu
NAS-IP-Address : system-ip
-------------------------------------------------------------------------------
RADIUS server settings
-------------------------------------------------------------------------------
Router : "Base"
Source address start : 10.10.165.1
Source address end : 10.10.165.2
Access algorithm : direct
Retry : 3
Timeout (s) : 5
Last management change : 09/15/2015 15:05:02
===============================================================================
===============================================================================
Servers for "IRS_1"
===============================================================================
Index Address Acct-port Auth-port CoA-port
-------------------------------------------------------------------------------
1 10.93.186.2 0 1812 0
===============================================================================
===============================================================================
Status for ISA RADIUS server policy "IRS_1"
===============================================================================
Server 1, group 1, member 1
-------------------------------------------------------------------------------
Purposes Up : authentication
Source IP address : 10.10.165.1
Acct Tx Requests : 0
Acct Tx Retries : 0
Acct Tx Timeouts : 0
Acct Rx Replies : 0
Auth Tx Requests : 11
Auth Tx Retries : 0
Auth Tx Timeouts : 0
Auth Rx Replies : 11
CoA Rx Requests : 0
Server 1, group 1, member 2
-------------------------------------------------------------------------------
Purposes Up : (None)
Source IP address : 10.10.165.2
Acct Tx Requests : 0
Acct Tx Retries : 0
Acct Tx Timeouts : 0
Acct Rx Replies : 0
Auth Tx Requests : 0
Auth Tx Retries : 0
Auth Tx Timeouts : 0
Auth Rx Replies : 0
CoA Rx Requests : 0
===============================================================================
Call Flow
Call Flow for Secure SSID with DSM shows the call flow for a secure SSID with DRP. The main steps are:
EAP authentication using DRP on MS-ISA placing UE authorized-only state
UE sends DHCP Discover which is forwarded by the MS-ISA to the CPM
CPM places UE in ESM-user state
Upon disconnect, the AP sends a RADIUS accounting-stop which clears the UE context on the WLAN-GW
Figure 2. Call Flow for Secure SSID with DSM 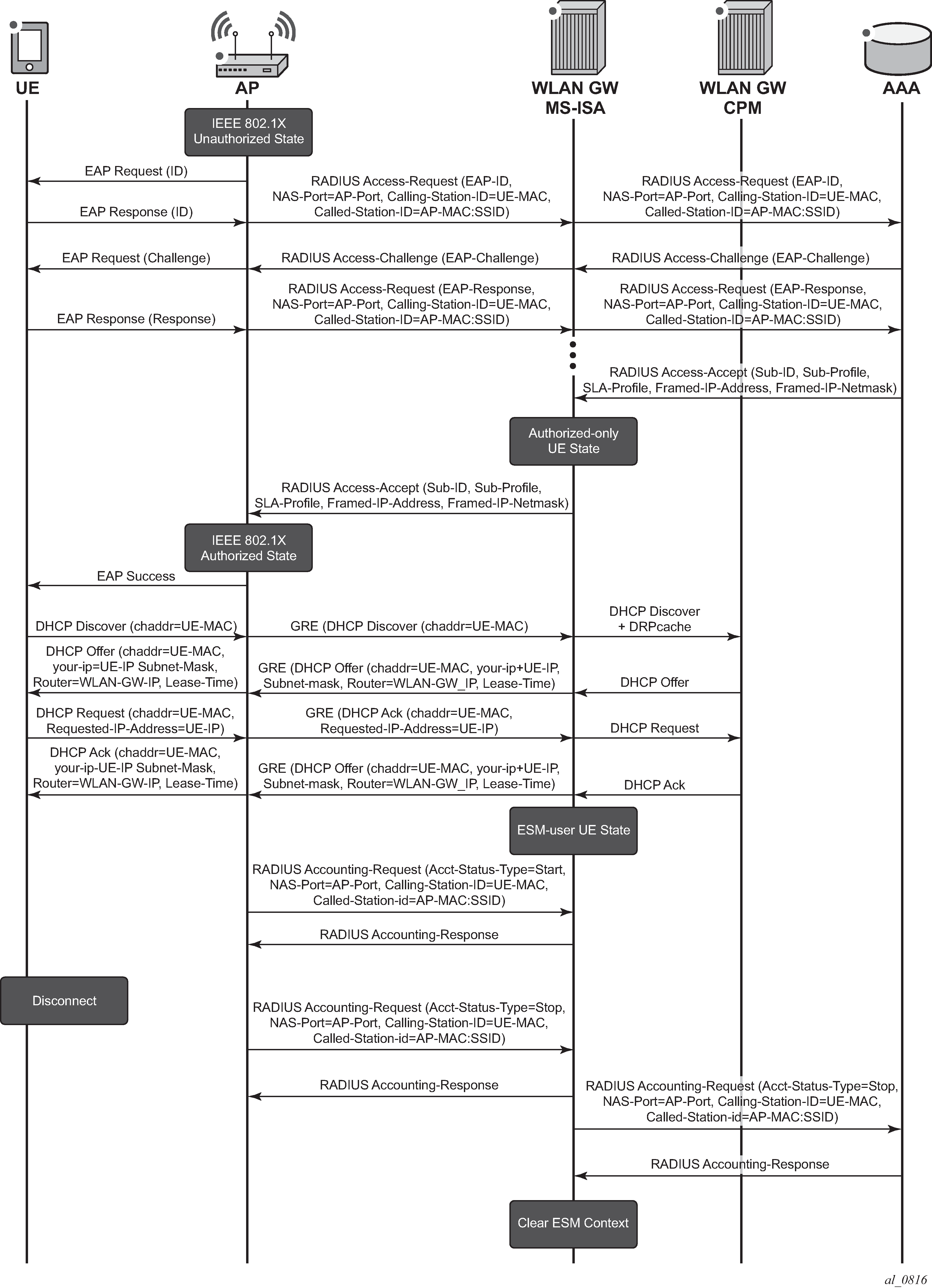
Debug
In this example, the following debug configuration is used (note that some default options are automatically added and do not need to be entered manually, e.g. mode under dhcp). For DRP, only a limited number of UEs can be debugged at a time and their MAC address have to be specified.
debug
router "2001"
ip
dhcp
detail-level medium
mode egr-ingr-and-dropped
exit
exit
exit
wlan-gw
group 1
ue 68:7f:74:8b:3d:d7 packet radius dhcp
exit
exit
exit
The following is a partial debug of a UE connecting to the SSID and authenticating with the RADIUS server. Shortly after logging in the UE disconnects from the SSID and the subscriber is removed on reception of the RADIUS accounting-stop message.
As soon as the UE attempts to connect to the secure SSID, the WLAN-GW distributed RADIUS proxy in VPRN 1000 receives the first Access-Request packet from the AP. Note that the CALLING STATION ID [31] attribute contains the MAC address of the UE, and that the AP sends the SSID name in the NAS IDENTIFIER [32] attribute.
1464 2015/09/15 16:19:52.93 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3291
Info: anchor ingressing frame
radius upstream from client
IP/UDP: from 10.1.3.10 (port 51235) to 192.11.11.11 (port 1812)
RADIUS: Access-Request (1) id 122 len 190
USER NAME [1] 5 user1
NAS IP ADDRESS [4] 4 10.1.3.10
FRAMED IP ADDRESS [8] 4 255.255.255.255
NAS IDENTIFIER [32] 10 WiFi-165-1
CALLED STATION ID [30] 28 00-0D-67-39-0B-65:WiFi-165-1
NAS PORT TYPE [61] 4 Wireless - IEEE 802.11(19)
NAS PORT [5] 4 0
CALLING STATION ID [31] 17 68-7F-74-8B-3D-D7
CONNECT INFO [77] 21 CONNECT 0Mbps 802.11b
SESSION ID [44] 17 556F2789-0000008D
FRAMED MTU [12] 4 1400
EAP MESSAGE [79] 10 0x02e2000a017573657231
MESSAGE AUTHENTICATOR [80] 16 0xbc3a66d7f9d4e02465797f2018914ed7
"
The WLAN-GW MS-ISA forwards the Access-Request to the RADIUS server in the Base router.
1465 2015/09/15 16:19:52.94 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3292
Info: anchor egressing frame
radius upstream to server
IP/UDP: from 10.10.165.1 (port 1024) to 10.93.186.2 (port 1812)
RADIUS: Access-Request (1) id 20 len 190
USER NAME [1] 5 user1
NAS IP ADDRESS [4] 4 10.1.3.10
FRAMED IP ADDRESS [8] 4 255.255.255.255
NAS IDENTIFIER [32] 10 WiFi-165-1
CALLED STATION ID [30] 28 00-0D-67-39-0B-65:WiFi-165-1
NAS PORT TYPE [61] 4 Wireless - IEEE 802.11(19)
NAS PORT [5] 4 0
CALLING STATION ID [31] 17 68-7F-74-8B-3D-D7
CONNECT INFO [77] 21 CONNECT 0Mbps 802.11b
SESSION ID [44] 17 556F2789-0000008D
FRAMED MTU [12] 4 1400
EAP MESSAGE [79] 10 0x02e2000a017573657231
MESSAGE AUTHENTICATOR [80] 16 0xbf48919833584995109b8387efc03b21
"
Many RADIUS Access-Request and Access Challenge messages are exchanged, which encapsulate the EAP authentication between the UE and the RADIUS server. At the end of the exchange, for a successful authentication, the WLAN-GW receives an Access-Accept message (for a failed authentication it would receive an Access-Reject).
1506 2015/09/15 16:20:01.69 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3333
Info: anchor ingressing frame
radius downstream from server
IP/UDP: from 10.93.186.2 (port 1812) to 10.10.165.1 (port 1024)
RADIUS: Access-Accept (2) id 25 len 203
VSA [26] 6 Alcatel(6527)
DEFAULT ROUTER [18] 4 192.168.1.1
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 10.92.186.92
FRAMED IP ADDRESS [8] 4 192.168.1.9
FRAMED IP NETMASK [9] 4 255.255.255.0
USER NAME [1] 5 user1
VSA [26] 52 Microsoft(311)
MS MPPE RECV KEY [17] 50 0xc1af6befb148f03d5bd9bb8863500dd0a1ffcf57392dcda
8db5529be6e2de52fc239d3595212ee1b181e50c064e292595db8
VSA [26] 52 Microsoft(311)
MS MPPE SEND KEY [16] 50 0xcbe708a0751bc3c9ef43bb58e2b103cca0a6373b6800279
148a0f1934176f000e1540e5078eeba9d43af5f42d4799b16a79d
EAP MESSAGE [79] 4 0x03ec0004
MESSAGE AUTHENTICATOR [80] 16 0xb3d2459f830217fd455b26e7767012c3
"
The Access-Accept contains the IP addressing parameters for the UE such as the IP address, netmask, and default gateway, as well as the subscriber ID string. The IP addressing information is used by the WLAN-GW, but the Access-Accept message is also forwarded by the RADIUS proxy to the AP to tell it that the UE authenticated successfully so it can associate with the SSID.
1507 2015/09/15 16:20:01.69 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3334
Info: anchor egressing frame
radius downstream to client
IP/UDP: from 192.11.11.11 (port 1812) to 10.1.3.10 (port 51235)
RADIUS: Access-Accept (2) id 132 len 203
VSA [26] 6 Alcatel(6527)
DEFAULT ROUTER [18] 4 192.168.1.1
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 10.92.186.92
FRAMED IP ADDRESS [8] 4 192.168.1.9
FRAMED IP NETMASK [9] 4 255.255.255.0
USER NAME [1] 5 user1
VSA [26] 52 Microsoft(311)
MS MPPE RECV KEY [17] 50 0xc1afa8a2e9f23dbe5c0d41410a8bcc7fc42406813a3bff6
a61c957fbad58b7af6de0447898603980aeebe5cc2d5db54b8ca7
VSA [26] 52 Microsoft(311)
MS MPPE SEND KEY [16] 50 0xcbe7fb9182312534ea50ecdfc8ed59874401515968ae276
7826fa664e3871d0b13e2946b01750825dbb95b3fe6ee615afa1a
EAP MESSAGE [79] 4 0x03ec0004
MESSAGE AUTHENTICATOR [80] 16 0x66b269e340328cee108dfc1d27f46fca
"
After the AP allows the UE to connect to the secure SSID, establishing L2 connectivity to the WLAN-GW across the soft-GRE tunnel, the UE can obtain an IP address through DHCP. The WLAN-GW receives a DHCP Discover from the UE on MS-ISA MDA 2/1:
1508 2015/09/15 16:20:01.83 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3335
Info: anchor ingressing frame
received upstream from tunnel
Ethernet: from 68:7f:74:8b:3d:d7 to ff:ff:ff:ff:ff:ff (ethertype: 0x0800)
IP/UDP: from 0.0.0.0 (port 68) to 255.255.255.255 (port 67)
DHCP:
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0xfb4fb37
DHCP options:
[53] Message type: Discover
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[12] Host name: VMS11
[60] Class id: MSFT 5.0
[55] Param request list: len = 12
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
43 Vendor specific
[255] End
"
The MS-ISA forwards the DHCP Discover to the CPM and it arrives on group interface GI1 in VPRN 2001.
1509 2015/09/15 16:20:01.83 EDT MINOR: DEBUG #2001 vprn2001 PIP
"PIP: DHCP
instance 6 (2001), interface index 3 (GI1),
received DHCP Boot Request on Interface GI1 (2/1/nat-out-ip:2049.1) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0xfb4fb37
DHCP options:
[53] Message type: Discover
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[12] Host name: VMS11
[60] Class id: MSFT 5.0
[55] Param request list: len = 12
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
43 Vendor specific
[255] End
"
The WLAN-GW sends a DHCP Offer to the UE with the IP address information retrieved from the RADIUS Access-Accept message.
1510 2015/09/15 16:20:01.85 EDT MINOR: DEBUG #2001 vprn2001 PIP
"PIP: DHCP
instance 6 (2001), interface index 3 (GI1),
transmitted DHCP Boot Reply to Interface GI1 (2/1/nat-out-ip:2049.1) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.9
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0xfb4fb37
DHCP options:
[53] Message type: Offer
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 604800
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: 10.92.186.92
[28] Broadcast addr: 192.168.1.255
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[12] Host name: VMS11
[255] End
"
The Offer message is sent to the MS-ISA and towards the UE (not shown). The UE then sends a DHCP Request and the WLAN-GW responds with an Ack.
1513 2015/09/15 16:20:01.86 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3337
Info: anchor ingressing frame
received upstream from tunnel
Ethernet: from 68:7f:74:8b:3d:d7 to ff:ff:ff:ff:ff:ff (ethertype: 0x0800)
IP/UDP: from 0.0.0.0 (port 68) to 255.255.255.255 (port 67)
DHCP:
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0xfb4fb37
DHCP options:
[53] Message type: Request
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[50] Requested IP addr: 192.168.1.9
[54] DHCP server addr: 192.168.1.1
[12] Host name: VMS11
[81] client FQDN: rcode1: 0, rcode2: 0, domain name = (hex) 00 56 4d 53 31
31
[60] Class id: MSFT 5.0
[55] Param request list: len = 12
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
43 Vendor specific
[255] End
"
1515 2015/09/15 16:20:01.86 EDT MINOR: DEBUG #2001 vprn2001 PIP
"PIP: DHCP
instance 6 (2001), interface index 3 (GI1),
transmitted DHCP Boot Reply to Interface GI1 (2/1/nat-out-ip:2049.1) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.9
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0xfb4fb37
DHCP options:
[53] Message type: Ack
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 604800
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: 10.92.186.92
[28] Broadcast addr: 192.168.1.255
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[12] Host name: VMS11
[81] client FQDN: rcode1: 0, rcode2: 0, domain name = (hex) 00 56 4d 53 31
31
[255] End
"
The AP sends a RADIUS accounting Start to the WLAN-GW as a result of the UE successfully associating with the SSID.
1518 2015/09/15 16:20:01.88 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3339
Info: anchor ingressing frame
radius upstream from client
IP/UDP: from 10.1.3.10 (port 51236) to 192.11.11.11 (port 1813)
RADIUS: Accounting-Request (4) id 133 len 197
SESSION ID [44] 17 556F2789-0000008D
EVENT TIMESTAMP [55] 4 1442292269
STATUS TYPE [40] 4 Start(1)
AUTHENTIC [45] 4 RADIUS(1)
USER NAME [1] 5 user1
NAS IP ADDRESS [4] 4 10.1.3.10
FRAMED IP ADDRESS [8] 4 192.168.1.9
NAS IDENTIFIER [32] 10 WiFi-165-1
CALLED STATION ID [30] 28 00-0D-67-39-0B-65:WiFi-165-1
NAS PORT TYPE [61] 4 Wireless - IEEE 802.11(19)
NAS PORT [5] 4 0
CALLING STATION ID [31] 17 68-7F-74-8B-3D-D7
CONNECT INFO [77] 21 CONNECT 0Mbps 802.11b
SESSION ID [44] 17 556F2789-0000008D
DELAY TIME [41] 4 0
"
At the end of the session, the UE disconnects from the SSID, and the AP sends a RADIUS accounting Stop to the WLAN-GW.
1520 2015/09/15 16:20:37.45 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 2/1, SeqNo 3401
Info: anchor ingressing frame
radius upstream from client
IP/UDP: from 10.1.3.10 (port 51237) to 192.11.11.11 (port 1813)
RADIUS: Accounting-Request (4) id 134 len 233
SESSION ID [44] 17 556F2789-0000008D
EVENT TIMESTAMP [55] 4 1442292304
STATUS TYPE [40] 4 Stop(2)
AUTHENTIC [45] 4 RADIUS(1)
USER NAME [1] 5 user1
NAS IP ADDRESS [4] 4 10.1.3.10
FRAMED IP ADDRESS [8] 4 192.168.1.9
NAS IDENTIFIER [32] 10 WiFi-165-1
CALLED STATION ID [30] 28 00-0D-67-39-0B-65:WiFi-165-1
NAS PORT TYPE [61] 4 Wireless - IEEE 802.11(19)
NAS PORT [5] 4 0
CALLING STATION ID [31] 17 68-7F-74-8B-3D-D7
CONNECT INFO [77] 21 CONNECT 0Mbps 802.11b
SESSION ID [44] 17 556F2789-0000008D
DELAY TIME [41] 4 0
SESSION TIME [46] 4 35
INPUT PACKETS [47] 4 57
OUTPUT PACKETS [48] 4 36
INPUT OCTETS [42] 4 5228
OUTPUT OCTETS [43] 4 5538
TERMINATE CAUSE [49] 4 User Request(1)
"
This removes the subscriber from the WLAN-GW, clears the DHCP state, and also removes the GRE tunnel if this UE is the last one on the tunnel.
Conclusion
The WLAN-GW can support many WiFi Offload architectures including secure SSID with various types of EAP authentication. WiFi Offload functions such as terminating GRE tunnels, NAT, and RADIUS server connectivity can be performed in separate routing instances if required. UE IP addresses can be assigned locally or from an external source such as RADIUS, and routing to the Internet can be performed in various ways, including NAT. Several show commands and debug options are available to help the operator monitor and troubleshoot the solution.