Virtual Residential Gateway Home LAN Extension
This chapter describes the home LAN extension of the Virtual Residential Gateway.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 15.0.R6. Hardware that supports the Wireless LAN Gateway (WLAN-GW) must be used (ISA1/ISA2 cards).
Overview
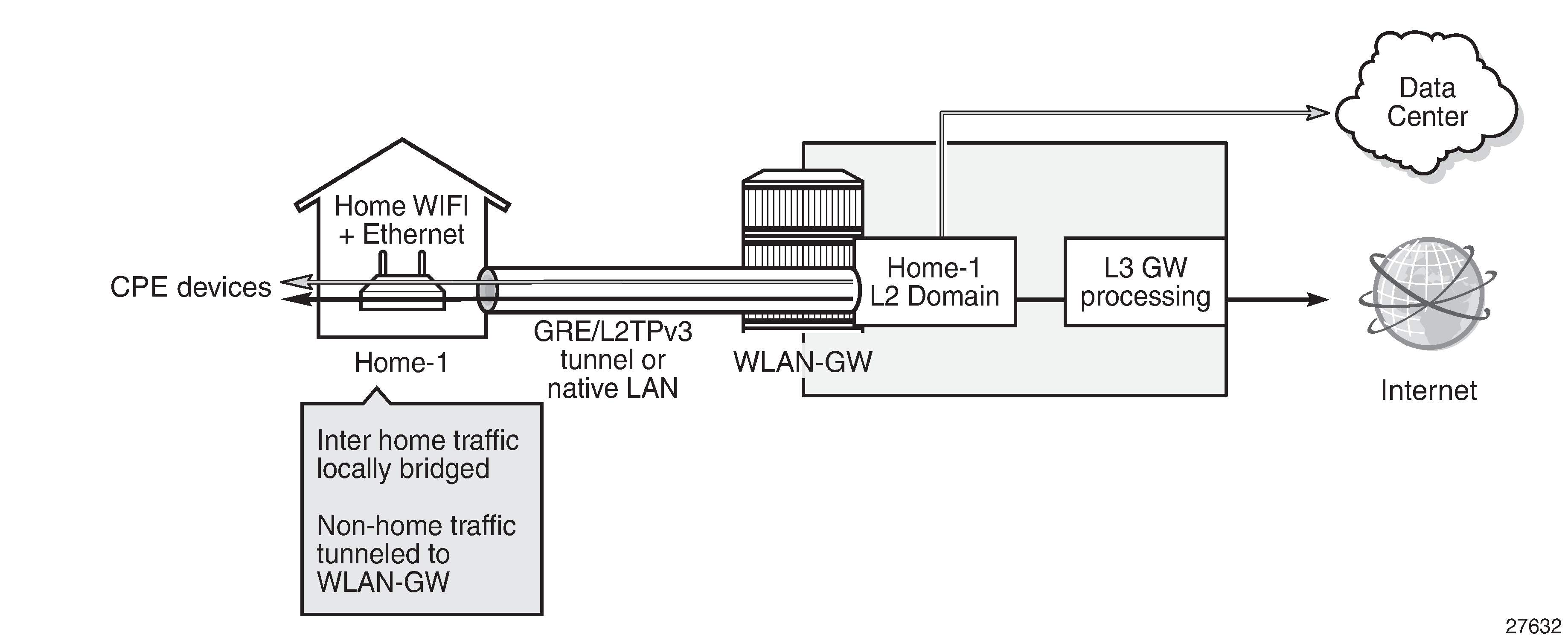
With Virtual Residential Gateway (vRGW), all L3 routing and services (DHCP server, NAT, firewall, Application Assurance (AA), and so on) are moved out of the home CPE to the service provider network.
The home CPE (known as Bridged Residential Gateway (BRG)) runs in a bridged mode and acts as an L2 switch between all connected home devices and the vRGW. Therefore, in-home traffic will be switched locally while other traffic will be sent to the vRGW.
However, there are some services/applications implemented on the cloud (for example, Data Center (DC)) that need to appear as if they are on the same home LAN and need L2 bridged access, so they need a Home LAN Extension (HLE).
Examples:
Digital Living Network Alliance (DLNA) server in the cloud for media streaming
Storage server in the cloud, discoverable via Server Message Block (SMB) protocol
HLE provides the capability to deploy new services in a DC that require L2 reachability to the home and being reachable on L2 to each individual host at home.
A unique per-home Bridge Domain (BD) is created on the WLAN-GW ISA1/ISA2. This acts as an L2 switch before any IP routing functionality is performed.
By using BGP-EVPN VPLS services, a BD is extended via a Virtual Extensible Local Area Network (VXLAN) tunnel to a virtual machine (VM) in a DC. Access from the home CPE can be a soft-GRE or an L2 Tunnel Protocol version 3 (L2TPv3) tunnel or Native VLAN terminated on the WLAN-GW group ISA via L2 Access Point (L2-AP). The HLE network side relies on MP-BGP for the control plane, whereas the data plane is based on VXLAN; see vRGW-HLE.
Bridge Domain Characteristics
The BD bridges traffic between the following connections:
access-facing connection (for example, home) - GRE/L2TPv3/L2-AP
network-facing connection (for example, DC) - VXLAN tunnel
ESM SAP-facing connection - each home has its own ESM SAP
BD Connections in the Data Plane shows the BD connections in the data plane.
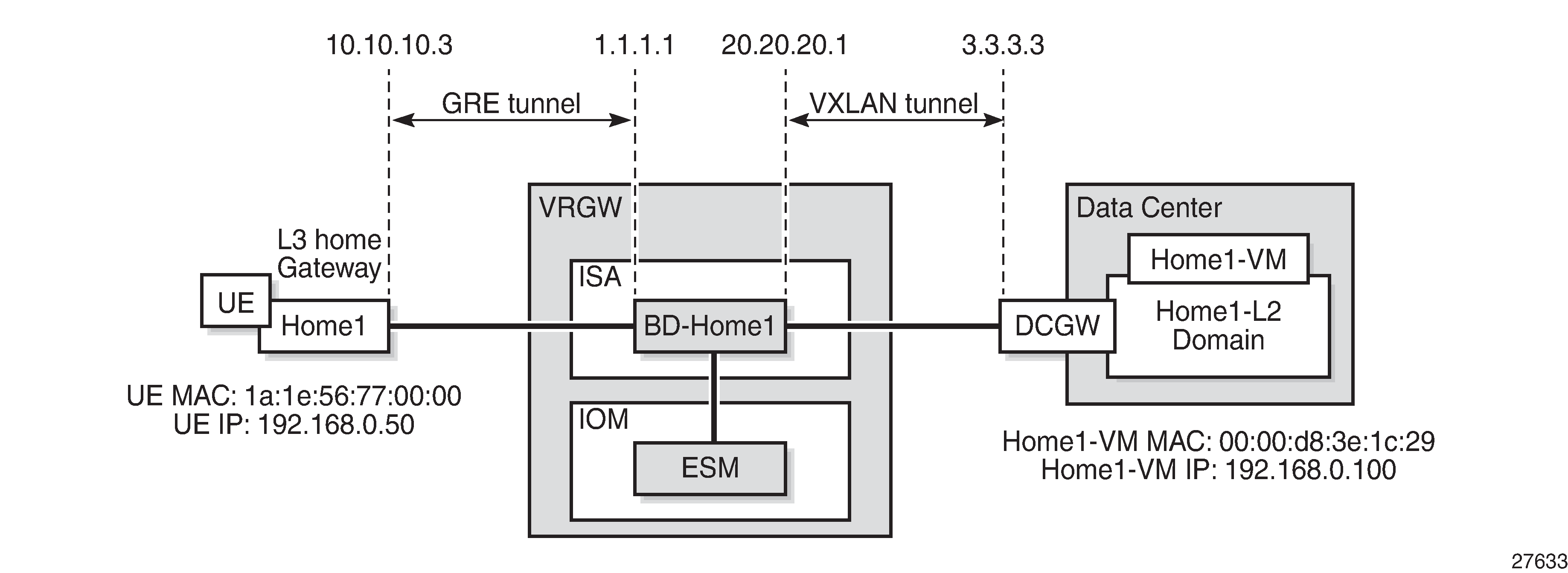
With HLE services, each home host constitutes a WLAN-GW User Equipment (UE) object and an ESM host object. Each network host (such as a VM in a DC) constitutes a WLAN-GW UE object but not an ESM host.
Each BD maintains the following tables:
MAC table: this table contains the learned MAC address by access and network connections
flood table: this table contains flood destinations for broadcast, unknown unicast, multicast (BUM) traffic; these are typically the access and network connections
IPv4 ARP table: this table contains learned ARP entries by access and network connections. The ARP and neighbor tables are populated when Assistive Address Resolution (AAR) is enabled (see the Assistive Address Resolution section for more information).
IPv6 neighbor table: this table contains learned neighbor entries by access and network connections.
Configuration
vRGW Configuration
The following prerequisite configurations are based on vRGW, in the order to be created.
WLAN-GW Group
configure wlan-gw-group <wlan-gw-group-id> [create] [redundancy <unit>]
<wlan-gw-group-id> : [1..4]
<create> : keyword
<unit> : iom|mda
configure
isa
wlan-gw-group 1 create redundancy mda
active-mda-limit 1
mda 3/1
no shutdown
exit
exit
exit
RADIUS Policies
ISA RADIUS Policy
configure
aaa
isa-radius-policy "isa-rad-pol-1" create
password nokia
servers
router "Base"
source-address-range 44.44.44.44
server 1 create
authentication
coa
ip-address 192.77.77.2
secret Nokia123
no shutdown
exit
exit
exit
exit
exit
RADIUS Server Policy
configure
router
radius-server
server "FreeRadius" address 192.77.77.2 secret Nokia123 create
accept-coa
exit
exit
exit
exit
configure
aaa
radius-server-policy "rad-serv-pol-1" create
servers
router "Base"
source-address 10.10.10.4
server 1 name "FreeRadius"
exit
exit
exit
exit
RADIUS Accounting Policy
configure
subscriber-mgmt
radius-accounting-policy "rad-acc-pol-1" create
---snip---
radius-server-policy "rad-serv-pol-1"
exit
exit
L2-Aware NAT
configure
service
vprn 333 customer 1 create
nat
inside
l2-aware
address 192.168.0.101/24
exit
exit
outside
pool "nat-pool-1" nat-group 1 type l2-aware create
port-reservation blocks 1
address-range 120.1.0.1 120.1.0.100 create
exit
no shutdown
exit
exit
exit
exit
nat
nat-policy "nat-pol-1" create
pool "nat-pool-1" router 333
exit
exit
exit
exit
Subscriber Management Parameters
configure
subscriber-mgmt
authentication-policy "auth-pol-1" create
exit
sla-profile "sla-prof-def" create
exit
sub-profile "sub-prof-def" create
nat-policy "nat-pol-1"
radius-accounting
policy "rad-acc-pol-1"
exit
exit
sub-ident-policy "sub-ident-pol-def" create
sub-profile-map
use-direct-map-as-default
exit
sla-profile-map
use-direct-map-as-default
exit
exit
exit
exit
BRG Profile
configure
subscriber-mgmt
vrgw
brg
brg-profile "brg-prof-1" create
dhcp-pool
subnet 192.168.0.1/24 start 192.168.0.50 end 192.168.0.99
exit
radius-authentication
password nokia
radius-server-policy "rad-serv-pol-1"
exit
exit
exit
exit
exit
exit
vRGW BRG Service
A service can be either an IES or a VPRN; in this example, a VPRN is shown.
*A:SR7-CMPT-vRGW# configure service vprn 333
*A:SR7-CMPT-vRGW>config>service>vprn# info
----------------------------------------------
route-distinguisher 333:333
subscriber-interface "sub-int-1" create
allow-unmatching-subnets
address 192.168.1.1/24
group-interface "grp-int-1" wlangw create
sap-parameters
sub-sla-mgmt
def-sla-profile "sla-prof-def"
def-sub-id use-auto-id
def-sub-profile "sub-prof-def"
sub-ident-policy "sub-ident-pol-def"
exit
exit
dhcp
proxy-server
emulated-server 192.168.1.1
no shutdown
exit
trusted
lease-populate 1000
gi-address 192.168.1.1
no shutdown
exit
authentication-policy "auth-pol-1"
wlan-gw
gw-address 1.1.1.1
learn-ap-mac
router "Base"
wlan-gw-group 1
l2-access-points
l2-ap 4/2/1 create
encap-type dot1q
no shutdown
exit
exit
vlan-tag-ranges
range default
authentication
authentication-policy "isa-rad-pol-1"
exit
authenticate-on-dhcp
vrgw
brg
default-brg-profile "brg-prof-1"
no shutdown
exit
exit
exit
exit
no shutdown
exit
exit
exit
nat
---snip---
exit
no shutdown
----------------------------------------------
BGP Configuration
Because HLE is based on BGP-EVPN, the operator needs to configure BGP with address family EVPN and define the corresponding neighbors, where a neighbor can, for example, be a Nuage Virtualized Service Controller (VSC) in a DC, a DC Gateway (DCGW), or a Route Reflector (RR) to avoid full mesh iBGP between iBGP speakers.
configure
router
bgp
min-route-advertisement 1
rapid-withdrawal
rapid-update evpn
group "EVPN"
family vpn-ipv4 evpn
type internal
neighbor 10.10.10.3
exit
exit
no shutdown
exit
exit
exit
HLE RADIUS Attributes and User Configuration
Each BD has a unique ID, which is an integer returned by the RADIUS server as the mandatory attribute [241.26.6527.9] Alc-Bridge-Id during BRG and device authentication. The returned value must be equal on both authentication levels.
The Alc-Bridge-Id is the ID of the per-subscriber BD on the ISA. It is different from the Alc-BRG-ID, which is the ID of the BRG.
Optional attributes can be returned by the RADIUS server during BRG authentication, which are used for BGP-EVPN VPLS to extend the BD to the remote network in the DC:
HLE BGP-EVPN route target (RT): [241.26.6527.14] Alc-RT, which defines which BD the route belongs to. If not returned, the system defines the RT as "target:<configured_lanext_as>:<Alc-Bridge-Id>". Configuring LANEXT AS will be covered in the VXLAN/EVPN Parameters section later in this chapter.
HLE BGP-EVPN route distinguisher (RD): [241.26.6527.15] Alc-RD; if not returned, the system defines the RD as "<configured_lanext_as>:<Alc-Bridge-Id>"
HLE BGP-EVPN VXLAN VNI: [241.26.6527.10] Alc-Vxlan-VNI (VXLAN Virtual Network Identifier), which is encoded in the MPLS label field in the EVPN routes, and is used to demux the VXLAN packet into the correct BD. If not returned, the system automatically assigns a VNI.
Examples for user entries on RADIUS server (FreeRadius) follow:
Device (Host) authentication
1a:1e:56:55:00:00 Cleartext-Password := "nokia"
Alc-Subsc-ID-str := "BRG-ID-5",
Alc-Bridge-Id := 555
Home (BRG) authentication
BRG-ID-5 Cleartext-Password := "nokia"
Alc-Bridge-Id := 555,
Alc-RT := target:100:555,
Alc-RD := 100:555,
Alc-Vxlan-VNI := 3
For accounting, in addition to the previous attributes, the operator can add the following attribute into accounting messages sent to the accounting server:
[241.26.6527.28] Alc-HLE-Device-Type to indicate the type of HLE host; the value is fixed to " home".
An example RADIUS accounting policy including LANEXT attributes follows:
configure
subscriber-mgmt
radius-accounting-policy "rad-acc-pol-1" create
---snip---
include-radius-attribute
---snip---
lanext-bridge-id
lanext-device-type
lanext-route-distinguisher
lanext-route-target
lanext-vni
---snip---
exit
radius-server-policy "rad-serv-pol-1"
exit
exit
exit
VXLAN/EVPN Parameters
A:WLANGW# configure router vrgw lanext
- lanext
[no] vxlan-port - Configure the remote VXLAN UDP port
[no] vxlan-vtep-ran* - Configure a range of VXLAN VTEP addresses
[no] wlan-gw-group - Configure the ISA WLAN Gateway group
[no] shutdown - Enable/disable the Home LAN Extension functionality
Where:
- vxlan-port <4789|8472> # default is 4789
- vxlan-vtep-range start <ip-address|ipv6-address> end <ip-address|ipv6-address>
- wlan-gw-group <wlan-gw-group-id> # value configured in previous step
Example:
configure
router
vrgw
lanext
vxlan-vtep-range start 20.20.20.1 end 20.20.20.20
wlan-gw-group 1
no shutdown
exit
exit
exit
exit
HLE is enabled on the Base routing instance.
As mentioned, RT is derived from the target:LANEXT_AS:bridge-id.
The LANEXT Autonomous System (AS) number can be configured in the following context:
A:WLANGW# configure subscriber-mgmt vrgw lanext router-target-as-number
- router-target-as-number <as-number>
<as-number> : [1..65535]
Example:
configure
subscriber-mgmt
vrgw
lanext
router-target-as-number 100
exit
exit
exit
exit
If the router AS number is not configured on the WLAN-GW, it must be returned from RADIUS in both Alc-RT & Alc-RD attributes during BRG authentication; otherwise, the host DHCP fails and the system shows the following error message in log 99.
53 2018/01/03 15:48:53.236 PST WARNING: DHCP #2005 vprn333 Lease State Population
Error
"Lease state table population error on SAP 3/1/nat-out-ip:2145.22 in service 333 - Could not link IPoE session (3/1/nat-out-ip:2145.22 - 1a:1e:56:77:00:00) with BRG BRG-ID-7: Router AS number is not configured"
BD-related Settings
On the group-interface level, the overall number of allowed BDs created can be limited. By default, the limit is zero, but it can be set between 1 and 131 071.
A:WLANGW>config>service>vprn>sub-if>grp-if>wlan-gw# max-lanext-bd
- max-lanext-bd <[1..131071]>
When HLE is enabled (under the VLAN vRGW LANEXT hierarchy) and max-lanext-bd on the group-interface level is zero, the following error message is displayed when the WLAN-GW is enabled in the group-interface context:
*A:WLANGW>config>service>vprn>sub-if>grp-if>wlan-gw# no shutdown
MINOR: SVCMGR #8456 The group-interface's max-lanext-bd must be greater than 0 to enable lanext in the VLAN range - VLAN range 4096-4096
If the number of BDs reaches that limit, the following message is displayed in log 99:
114 2018/01/03 16:04:14.215 PST WARNING: DHCP #2029 Base Miscellaneous DHCP Problem
"Failed to create bridge domain: max-lanext-bd limit reached - Bridge ID: 555, MAC: 1a:1e:56:55:00:00"
BD Access-Side Settings
The max-mac parameter in the access context is used to limit the number of MAC addresses learned from home devices:
*A:SR7-CMPT-vRGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# access
- access
[no] max-mac - Configure maximum number of MAC entries in bridged domain
[no] multi-access - Allow multiple access
The max-mac ranges between 1 and 128, with a default value of 20.
The multi-access parameter is used for Multi-Dwelling Unit (MDU) scenarios.
To override the default parameters, the vRGW LANEXT hierarchy should be in the shutdown state; an error is raised when trying to configure these parameters when LANEXT is enabled.
*A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext>access# max-mac 128
MINOR: SVCMGR #8452 Not allowed when lanext is no shut
*A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext>access# multi-access
MINOR: SVCMGR #8452 Not allowed when lanext is no shut
BD Network-Side Settings
The max-mac parameter in the network context is used to limit the number of MAC addresses learned from EVPN/DC.
*A:SR7-CMPT-vRGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# network
- network
[no] max-mac - Configure maximum number of VM MAC entries in bridged domain
[no] shutdown - Enable/disable data center connections
The max-mac ranges between 1 and 64, with a default value of 20. LANEXT is by default enabled (no shutdown).
*A:SR7-CMPT-vRGW>grp-if>wlan-gw>ranges>range>vrgw>lanext>network# max-mac
<[1..64]>
The operator can shut down the network side to disable the connection to the DC.
To override the default configuration, LANEXT should be shut down, as follows:
*A:SR7-CMPT-vRGW>grp-if>wlan-gw>ranges>range>vrgw>lanext>network# max-mac 64
MINOR: SVCMGR #8452 Not allowed when lanext is no shut
*A:SR7-CMPT-vRGW>grp-if>wlan-gw>ranges>range>vrgw>lanext>network# shutdown
MINOR: SVCMGR #8452 Not allowed when lanext is no shut
Finally, the LANEXT functionality is enabled under the following context:
*A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext#
[no] shutdown - Enable/disable the Home LAN Extension functionality
ARP/ND Handling and MAC Advertisement Optimizations
Assistive Address Resolution
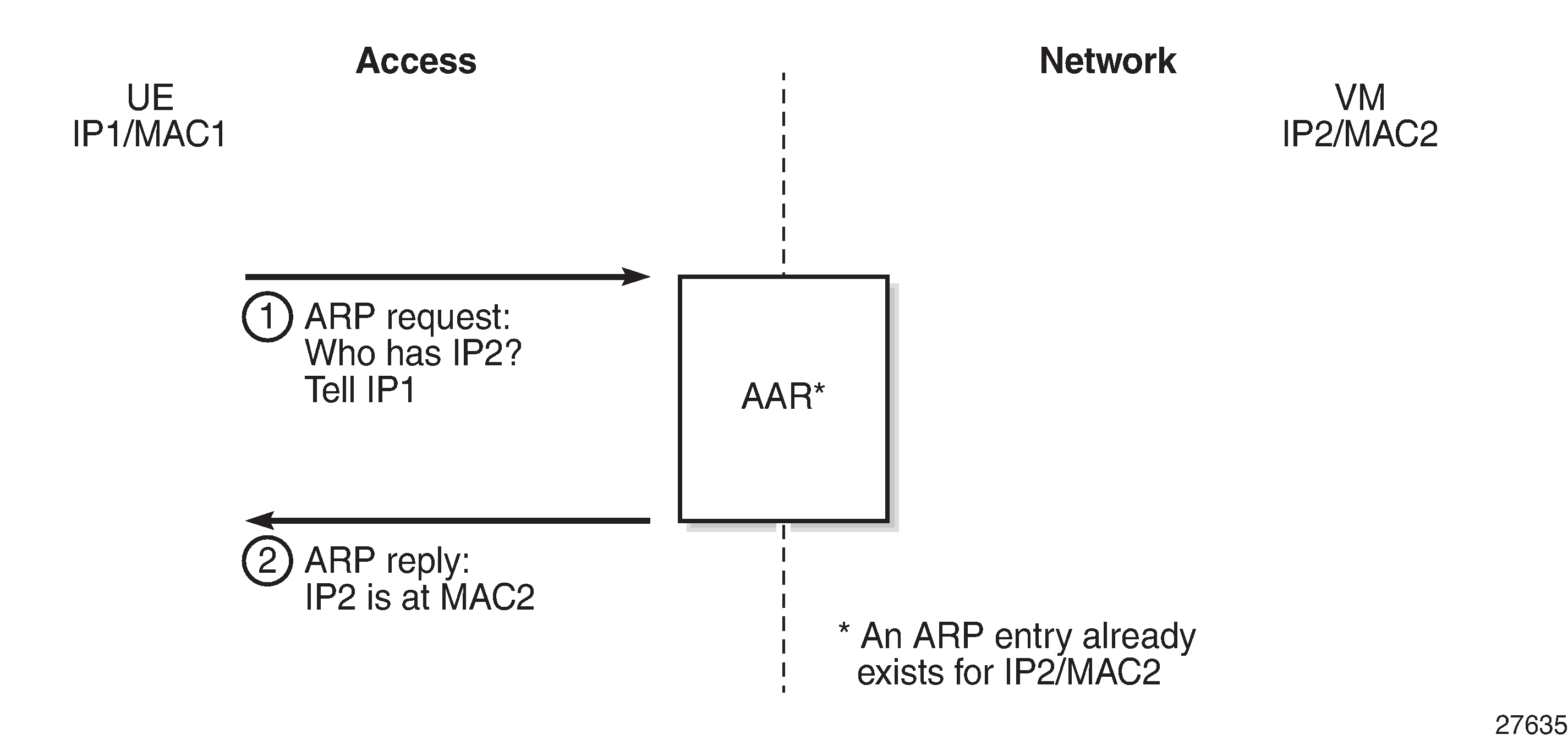
AAR is an optional HLE feature used to avoid sending ARP/ND requests from the home across a WAN to a remote network, or sending ARP/ND requests from the remote network across an access network to a home. The system responds to the ARP/ND request from the network or home with the learned ARP/ND entries, instead of flooding them.
With AAR enabled, the system populates the ARP and neighbor tables with the learned ARP and neighbor entries via either:
BGP EVPN MAC routes that contain an IP address, or
(G)ARP/ND/NS packets
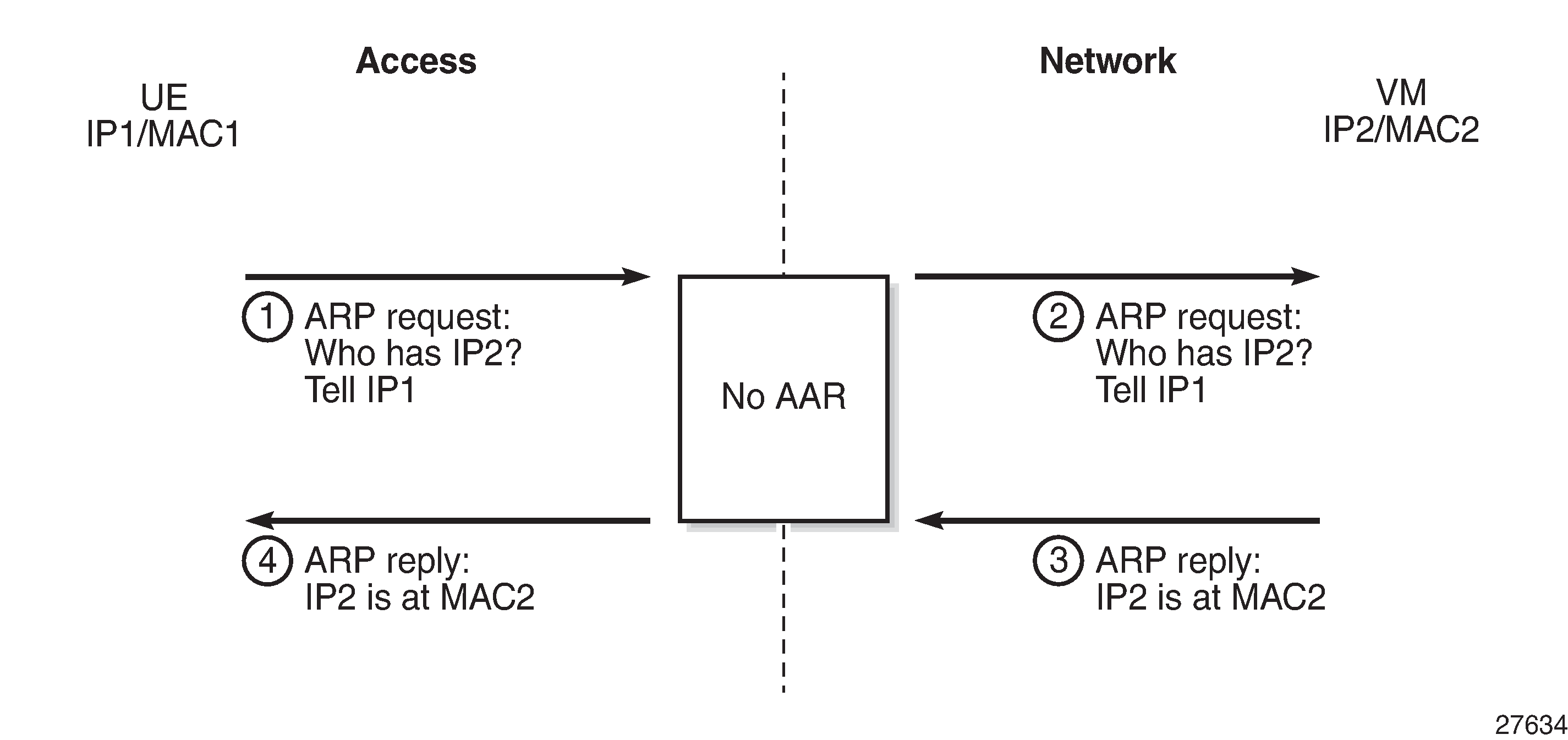
AAR Disabled
AAR is disabled by default. With AAR disabled, the ARP request is flooded from one side to the other; see ARP Requests Flooded with AAR Disabled. The BD ARP table will only be populated for the GW address and any IP/MAC learned via BGP EVPN MAC routes that contain an IP address.
AAR Enabled
To enable AAR, assistive-address-resolution is configured in the lanext context, as follows:
*A:SR7-CMPT-vRGW>grp-if>wlan-gw>ranges>range>vrgw>lanext#
[no] assistive-addr* - Enable/disable assistive address resolution in bridged domains
AAR can only be enabled when lanext is shut down, as follows:
A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# assistive-address-resolution
MINOR: SVCMGR #8452 Not allowed when lanext is no shut
In No ARP Request Flooding with AAR Enabled, when an ARP request is received, the ISA performs a lookup in the ARP table with the IP address as a key, and if found, it answers without flooding to the other side.
MAC Address Translation
MAC Address Translation (MAT) is an optional HLE feature that translates the host MAC address of a subscriber into a single BD MAC address. This feature decreases the number of BGP EVPN MAC routes to advertise per subscriber to one, and prevents BGP sending update messages when hosts are created and removed, which increases BGP stability.
MAT is performed on traffic in both directions:
traffic from access to network - the system changes the source MAC address to BD MAC address, as shown in MAT - Access to Network Direction.
Figure 5. MAT - Access to Network Direction 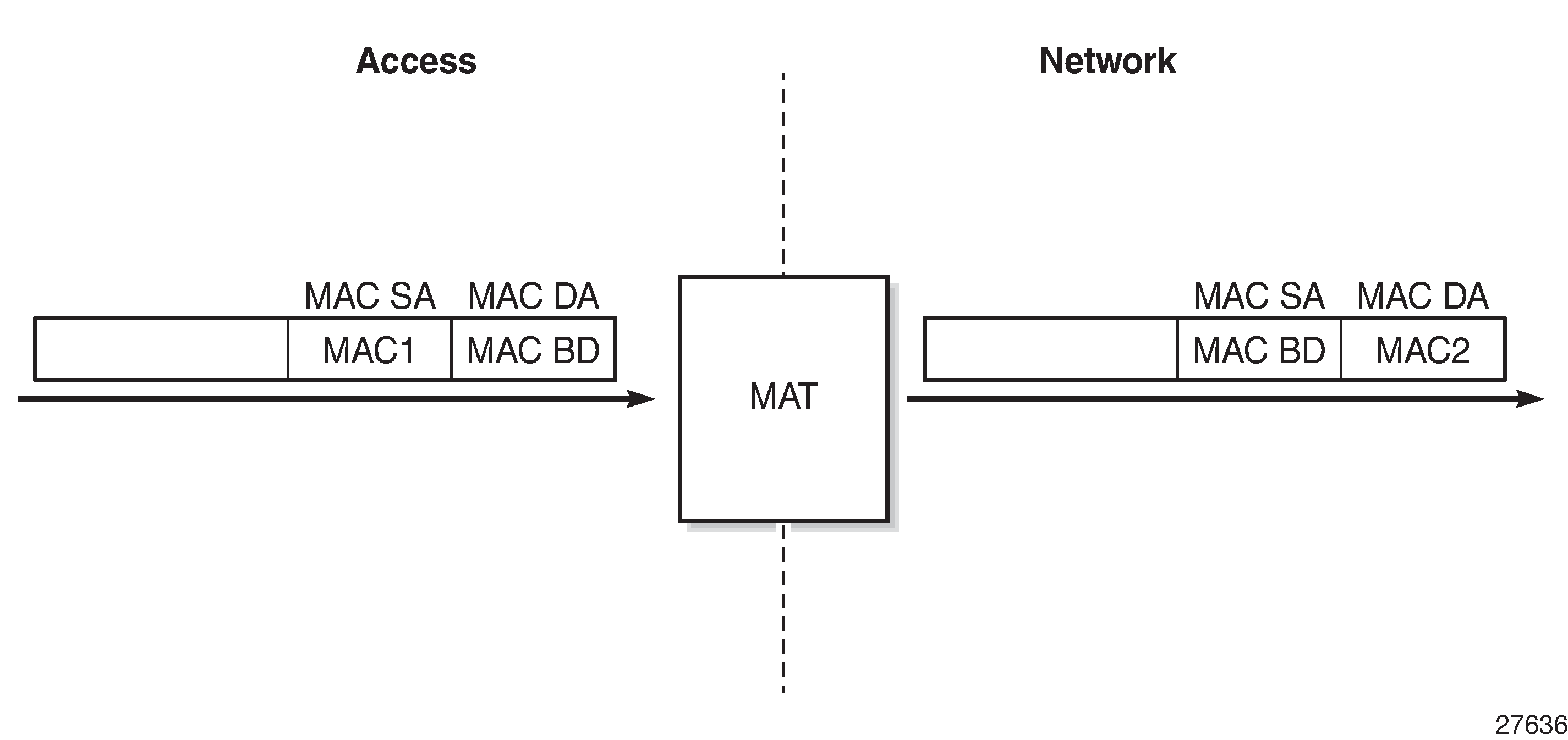
traffic from network to access - the system changes the destination MAC address (BD MAC) to the real host MAC address based on the ARP table or neighbor table lookup using the IP address as key, as shown in MAT - Network to Access Direction.
Figure 6. MAT - Network to Access Direction 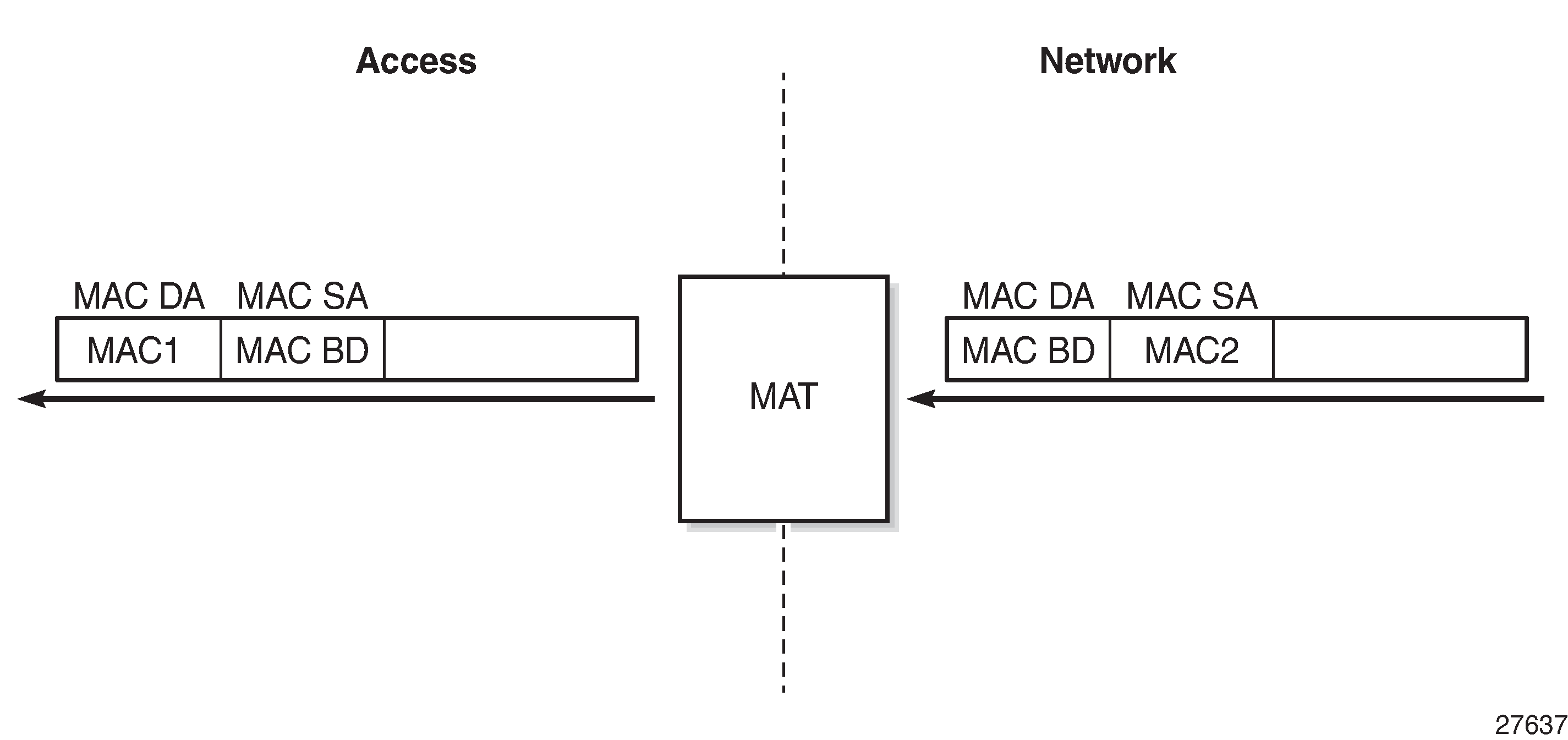
MAT is disabled by default. MAC is enabled by configuring mac-translation and bd-mac-prefix under the lanext context, as follows.
*A:SR7-CMPT-vRGW>grp-if>wlan-gw>ranges>range>vrgw>lanext#
[no] assistive-addr* - Enable/disable assistive address resolution in bridged domains
[no] bd-mac-prefix - Configure MAC translation prefix in bridged domains
[no] mac-translation - Enable/disable MAC translation in bridged domains
To configure MAT, the following conditions apply:
Assistive address resolution must be enabled
*A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# no shutdown MINOR: SVCMGR #8455 mac-translation requires assistive-address-resolutionlanext context must be shut down
A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# mac-translation MINOR: SVCMGR #8452 Not allowed when lanext is no shutBD-MAC-Prefix must be configured
*A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# shutdown *A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# mac-translation *A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext# no shutdown MINOR: SVCMGR #8454 mac-translation requires a bd-mac-prefix to be set *A:WLANGW>grp-if>wlan-gw>ranges>range>vrgw>lanext#
When MAT is configured, the BD ARP table will use a system-generated MAC address with MAC prefix as the configured BD-MAC-prefix, instead of the group-interface MAC address for the default GW entry.
This MAC address will be advertised toward the network as a BGP EVPN MAC route (route type 2), and used for MAC translation, as shown in MAT - Access to Network Direction and MAT - Network to Access Direction.
When MAT is disabled (default), ARP replies contain the real MAC address, in case there is an existing entry in the ARP table; otherwise, the ARP requests are flooded to the other side. Data traffic will contain the real MAC destination address (DA).
When MAT is enabled, ARP replies use the BD MAC address in both directions. No MAC routes from the host side are learned at the network side. Data traffic will contain the BD MAC DA.
For two hosts within the same BD, and for traffic in the network to access direction, the ISA does a lookup for ARP entries with the IP DA as a key. If the IP DA is found, the MAC DA is replaced by the MAC DA of the corresponding host.
ARP/MAT/BD-MAC-Prefix Possible Combinations shows possible combinations for ARP/MAT/BD-MAC-Prefix, where Combo1 is the default combination.
vRGW lanext |
Combo1 |
Combo2 |
Combo3 |
Combo4 |
Combo5 |
|---|---|---|---|---|---|
assistive-address-resolution |
Disabled |
Disabled |
Enabled |
Enabled |
Enabled |
bd-mac-prefix |
Disabled |
Enabled |
Disabled |
Enabled |
Enabled |
mac-translation |
Disabled |
Disabled |
Disabled |
Disabled |
Enabled |
Show Commands
The following command displays BD info, or a specific BD:
show subscriber-mgmt vrgw lanext bd [<bridge-id>]
A:WLANGW# show subscriber-mgmt vrgw lanext bd 555
===============================================================================
Bridge Domain(s)
===============================================================================
Bridge-id : 555
VNI : 3
Route Target : target:100:555
Route Distinguisher : 100:555
WlanGw GrpId : 1
ISA MemberId : 1
WlanGw Bd VlanTag : N/A
WlanGw Bd Service : 333
WlanGw Bd Interface : grp-int-1
WlanGw Bd Mac Translation : enabled
WlanGw Bd Mac : aa:bb:cc:00:00:03
WlanGw Bd Assist.Addr.Res : enabled
WlanGw Bd Netw MaxMac : 20
WlanGw Bd Netw State : enabled
WlanGw Bd Accs MaxMac : 20
-------------------------------------------------------------------------------
No. of Bridge Domains: 1
===============================================================================
The following command displays UE information for a specific BD:
show subscriber-mgmt wlan-gw ue bd <bridge-id>
Each host at home or VM in a DC is considered a WLAN-GW UE object, as follows:
A:WLANGW# show subscriber-mgmt wlan-gw ue bd 777
===============================================================================
User Equipments
===============================================================================
Bridge ID : 777
MAC address : 00:00:d8:3e:1c:29
-------------------------------------------------------------------------------
VLAN Q-tag : (Not Specified)
MPLS label : (Not Specified)
Tunnel router : "Base"
Tunnel remote IP address : 3.3.3.3
Tunnel local IP address : 20.20.20.1
Tunnel encapsulation : vxlan
Retail service : N/A
SSID : (Not Specified)
Previous Access Point IP : (Not Specified)
IMSI : (Not Specified)
Subscriber host service : N/A
Subscriber host SAP : N/A
Last move time : 2018/01/04 19:33:35
Bridge ID : 777
MAC address : 00:21:05:a1:ba:6a
-------------------------------------------------------------------------------
VLAN Q-tag : (Not Specified)
MPLS label : (Not Specified)
Tunnel router : "Base"
Tunnel remote IP address : 3.3.3.3
Tunnel local IP address : 20.20.20.1
Tunnel encapsulation : vxlan
Retail service : N/A
SSID : (Not Specified)
Previous Access Point IP : (Not Specified)
IMSI : (Not Specified)
Subscriber host service : N/A
Subscriber host SAP : N/A
Last move time : 2018/01/04 19:31:57
Bridge ID : 777
MAC address : 1a:1e:56:77:00:00
-------------------------------------------------------------------------------
VLAN Q-tag : 777
MPLS label : 1020
Tunnel router : "Base"
Tunnel remote IP address : 10.10.10.3
Tunnel local IP address : 1.1.1.1
Tunnel encapsulation : gre
Retail service : N/A
SSID : (Not Specified)
Previous Access Point IP : (Not Specified)
IMSI : (Not Specified)
Subscriber host service : 333
Subscriber host SAP : 3/1/nat-out-ip:2145.24
Last move time : 2018/01/04 19:31:55
-------------------------------------------------------------------------------
No. of UE: 3
=============================================================
The previous example was for GRE access (tunnel encapsulation GRE for UE on the access side); the following example is for the VLAN native L2-AP case.
*A:WLANGW# show subscriber-mgmt wlan-gw ue bd 555
===============================================================================
User Equipments
===============================================================================
Bridge ID : 555
MAC address : 00:00:d8:3e:1c:27
-------------------------------------------------------------------------------
VLAN Q-tag : (Not Specified)
MPLS label : (Not Specified)
Tunnel router : "Base"
Tunnel remote IP address : 10.10.10.3
Tunnel local IP address : 20.20.20.1
Tunnel encapsulation : vxlan
Retail service : N/A
SSID : (Not Specified)
Previous Access Point IP : (Not Specified)
IMSI : (Not Specified)
Subscriber host service : N/A
Subscriber host SAP : N/A
Last move time : 2018/01/05 10:44:41
Bridge ID : 555
MAC address : 1a:1e:56:55:00:00
-------------------------------------------------------------------------------
VLAN Q-tag : (Not Specified)
MPLS label : (Not Specified)
Tunnel router : "Base"
Tunnel remote IP address : fe80::22bf:ffff:fe00:1901
Tunnel local IP address : fe80::ff:fe02:202
Tunnel encapsulation : vlan
Retail service : N/A
SSID : (Not Specified)
Previous Access Point IP : (Not Specified)
IMSI : (Not Specified)
Subscriber host service : 333
Subscriber host SAP : 3/1/nat-out-ip:2145.29
Last move time : 2018/01/05 10:43:54
-------------------------------------------------------------------------------
No. of UE: 2
===============================================================================
Tools Commands
The following lists tools commands dump info regarding BD data plane tables, as well as BD statistics:
*A:WLANGW# tools dump wlan-gw lanext bd
- bd <bridge-id>
arp-table - Dump bridge domain ARP table
flood-table - Dump bridge domain flood table
mac-table - Dump bridge domain MAC table
neighbor-table - Dump bridge domain neighbor table
statistics - Dump bridge domain statistics
The following tools command is used to clear ARP/MAC/Neighbor table entries, as well as BD statistics:
*A:WLANGW# tools perform wlan-gw lanext bd
- bd <bridge-id>
clear-arp - Clear bridge domain ARP table
clear-mac - Clear bridge domain MAC table
clear-neighbor - Clear bridge domain neighbor table
clear-statisti* - Clear bridge domain statistics
ARP Table
The following tools command shows the ARP table when AAR is disabled and ARP requests are flooded when the ARP table does not contain an entry for the IP DA:
A:WLANGW# tools dump wlan-gw lanext bd 777 arp-table
===============================================================================
Matched 2 ARP entries for Bridge Domain 777 on Slot #3 MDA #1
===============================================================================
IP Address MAC Address Class Timestamp
-------------------------------------------------------------------------------
192.168.0.101 00:21:05:a1:ba:6a Network 01/03/2018 11:59:39
192.168.0.1 00:00:00:02:02:02 Access 01/03/2018 11:59:37
===============================================================================
Where:
192.168.0.1 00:00:00:02:02:02 is the entry learned from the BRG subnet default GW and group-interface MAC
192.168.0.101 00:21:05:a1:ba:6a is an entry learned from the network side via the BGP EVPN MAC route (type 2), which contains IP address 192.168.0.101, as shown in the following output:
A:WLANGW# show router bgp routes evpn mac mac-address 00:21:05:a1:ba:6a =============================================================================== BGP Router ID:10.10.10.4 AS:65100 Local AS:65100 =============================================================================== Legend - Status codes : u - used, s - suppressed, h - history, d - decayed, * - valid l - leaked, x - stale, > - best, b - backup, p - purge Origin codes : i - IGP, e - EGP, ? - incomplete =============================================================================== BGP EVPN MAC Routes =============================================================================== Flag Route Dist. MacAddr ESI Tag Mac Mobility Label1 Ip Address NextHop ------------------------------------------------------------------------------- u*>i 200:777 00:21:05:a1:ba:6a ESI-0 0 Static VNI 777 192.168.0.101 3.3.3.3 ------------------------------------------------------------------------------- Routes : 1 ===============================================================================
The following tools command shows the ARP table when AAR is enabled and bd-mac-prefix configured:
*A:WLANGW# tools dump wlan-gw lanext bd 666 arp-table
===============================================================================
Matched 4 ARP entries for Bridge Domain 666 on Slot #3 MDA #1
===============================================================================
IP Address MAC Address Class Timestamp
-------------------------------------------------------------------------------
192.168.0.100 00:00:d8:3e:1c:28 Network 01/05/2018 11:27:59
192.168.0.51 1a:1e:56:66:00:01 Access 01/05/2018 11:27:59
192.168.0.1 aa:bb:cc:00:00:02 Access 01/05/2018 10:43:54
192.168.0.50 1a:1e:56:66:00:00 Access 01/05/2018 11:27:59
===============================================================================
Where:
192.168.0.1 aa:bb:cc:00:00:02 is the entry for the BRG subnet default GW with bd-mac-prefix AA:BB:CC configured
192.168.0.100 00:00:d8:3e:1c:28 is an entry learned from the network side via ARP
MAC Table
The following tools command shows the MAC table for GRE access:
*A:WLANGW# tools dump wlan-gw lanext bd 777 mac-table
===============================================================================
Matched 3 MAC entries for Bridge Domain 777 on Slot #3 MDA #1
===============================================================================
UE-Mac Vlan Bridge-Id Description L2-Svc L2-Vlan
Tunnel Class Type Router Src-IP
Anchor Dst-IP
-------------------------------------------------------------------------------
1a:1e:56:77:00:00 777 777 ESM-user N/A N/A
3/1 Access GRE Base 10.10.10.3
3/1/nat-out-ip:2145.28 1.1.1.1
-------------------------------------------------------------------------------
00:00:d8:3e:1c:29 N/A 777 ESM-user N/A N/A
3/1 Network VXLAN Base 3.3.3.3
3/1/nat-out-ip:2145.28 20.20.20.1
-------------------------------------------------------------------------------
00:21:05:a1:ba:6a N/A 777 ESM-user N/A N/A
3/1 Network VXLAN Base 3.3.3.3
3/1/nat-out-ip:2145.28 20.20.20.1
-------------------------------------------------------------------------------
===============================================================================
The following tools command shows the MAC table for VLAN native L2-AP access:
A:WLANGW# tools dump wlan-gw lanext bd 555 mac-table
===============================================================================
Matched 2 MAC entries for Bridge Domain 555 on Slot #3 MDA #1
===============================================================================
UE-Mac Vlan Bridge-Id Description L2-Svc L2-Vlan
Tunnel Class Type Router Src-IP
Anchor Dst-IP
-------------------------------------------------------------------------------
00:00:d8:3e:1c:27 N/A 555 ESM-user N/A N/A
3/1 Network VXLAN Base 10.10.10.3
3/1/nat-out-ip:2145.29 20.20.20.1
-------------------------------------------------------------------------------
1a:1e:56:55:00:00 N/A 555 ESM-user 2147483692 555
3/1 Access L2 Base fe80::22bf:ffff:fe00:1901
3/1/nat-out-ip:2145.29 fe80::ff:fe02:202
-------------------------------------------------------------------------------
===============================================================================
The type is VXLAN for MAC addresses learned from the network side.
Flood Table
The following tools command shows the flood table for GRE:
*A:WLANGW# tools dump wlan-gw lanext bd 777 flood-table
===============================================================================
Matched 2 flood entries for Bridge Domain 777 on Slot #3 MDA #1
===============================================================================
Tunnel Class Type Vlan Src-IP
Port Encap Dst-IP
-------------------------------------------------------------------------------
3/1 Access GRE 777 10.10.10.3
3/1/nat-in-ip 2049.1 1.1.1.1
-------------------------------------------------------------------------------
3/1 Network VXLAN N/A 3.3.3.3
3/1/nat-out-ip 2081.3 20.20.20.1
-------------------------------------------------------------------------------
===============================================================================
The following tools command shows the flood table for VLAN native L2-AP:
*A:WLANGW# tools dump wlan-gw lanext bd 555 flood-table
===============================================================================
Matched 2 flood entries for Bridge Domain 555 on Slot #3 MDA #1
===============================================================================
Tunnel Class Type Vlan Src-IP
Port Encap Dst-IP
-------------------------------------------------------------------------------
3/1 Access L2 N/A fe80::22bf:ffff:fe00:1901
3/1/nat-in-ip 2305.1 fe80::ff:fe02:202
-------------------------------------------------------------------------------
3/1 Network VXLAN N/A 10.10.10.3
3/1/nat-out-ip 2081.3 20.20.20.1
-------------------------------------------------------------------------------
===============================================================================
Statistics
To view statistics for traffic crossing a specific BD, the following tools command is used:
*A:WLANGW# tools dump wlan-gw lanext bd 555 statistics
===============================================================================
Statistics for Bridge Domain 555 on Slot #3 MDA #1
===============================================================================
upstream rx frames : 9703260
downstream rx frames : 2
upstream rx octets : 9664443740
downstream rx octets : 692
arp entry dropped : 0
arp entry no resources : 0
arp entry expired : 0
arp entry conflict : 0
neighbor entry dropped : 0
neighbor entry no resources : 0
neighbor entry expired : 0
neighbor entry conflict : 0
flood entry dropped : 0
flood no resources : 0
flood throttled : 0
flood upstream forward : 1
flood upstream dropped : 0
flood downstream forward : 0
flood downstream dropped : 0
===============================================================================
Where:
Upstream direction means traffic coming from the DC or home going toward the BD.
Downstream direction means traffic coming from the Internet toward the BD.
Conclusion
This chapter describes HLE based on vRGW and BGP EVPN to extend home LAN to DC VMs via VXLAN, for different access models (softGRE and VLAN L2-AP).