ARP Hosts
This chapter describes advanced ARP host configurations.
Topics in this chapter include:
Applicability
This section describes ARP hosts and is applicable to the 7450 ESS and 7750 SR series and was tested on SR OS 13.0 R3.
Overview
In business access areas, CPEs typically get their IP address information through DHCP and PPPoE. However, CPE network facing interfaces can be configured statically. In such cases, the first packet the network receives from the user is an ARP to the Broadband Service Aggregator (BSA) or Broadband Service Router (BSR) interface. In order to accommodate such configurations, Enhanced Subscriber Management (ESM) feature set supports RP hosts.
In practice, this means that authentication, self-provisioning and Service Level Agreement (SLA) enforcement can be triggered by reception of ARP packets.
The BRAS node will learn the IP-MAC association based on the received ARP request packet and will instanciate subscriber hosts based on results from RADIUS authentication, the same way as this would happen through DHCP or PPPoE.
This chapter provides configuration and troubleshooting commands for ARP hosts. Features common with other host types and not unique to ARP hosts are not described in this chapter. (Not exhaustive list: RADIUS managed routes, routed subscriber with dynamic BGP peering, Wholesale/Retail, Managed SAPs configurations, ESM related host limitation mechanisms, host High-Availability, multi-chassis peer synchronization).
Knowledge of the Triple Play Service Delivery Architecture (TPSDA) concepts is assumed throughout this chapter.
Enhanced Subscriber Management and RADIUS authentication are mandatory for the use of ARP hosts.
ARP host is supported in the bridged CO (VPLS) and the routed CO (Subscriber Interface) model. It is triggered by the first ARP packet received from the host. ARP host is also supported in a wholesale/retail context and on managed SAPs (MSAP).
The IP and MAC addresses are extracted from the ARP request. They are copied in the access-request message sent to the RADIUS server:
RADIUS attribute [1] Username = IP address
VSA [26][27] Client Hardware Address = MAC address
On successful authentication RADIUS will reply with an access-accept message, and ESM will create the ARP host. ESM string assignment options are out of the scope for this scenario.
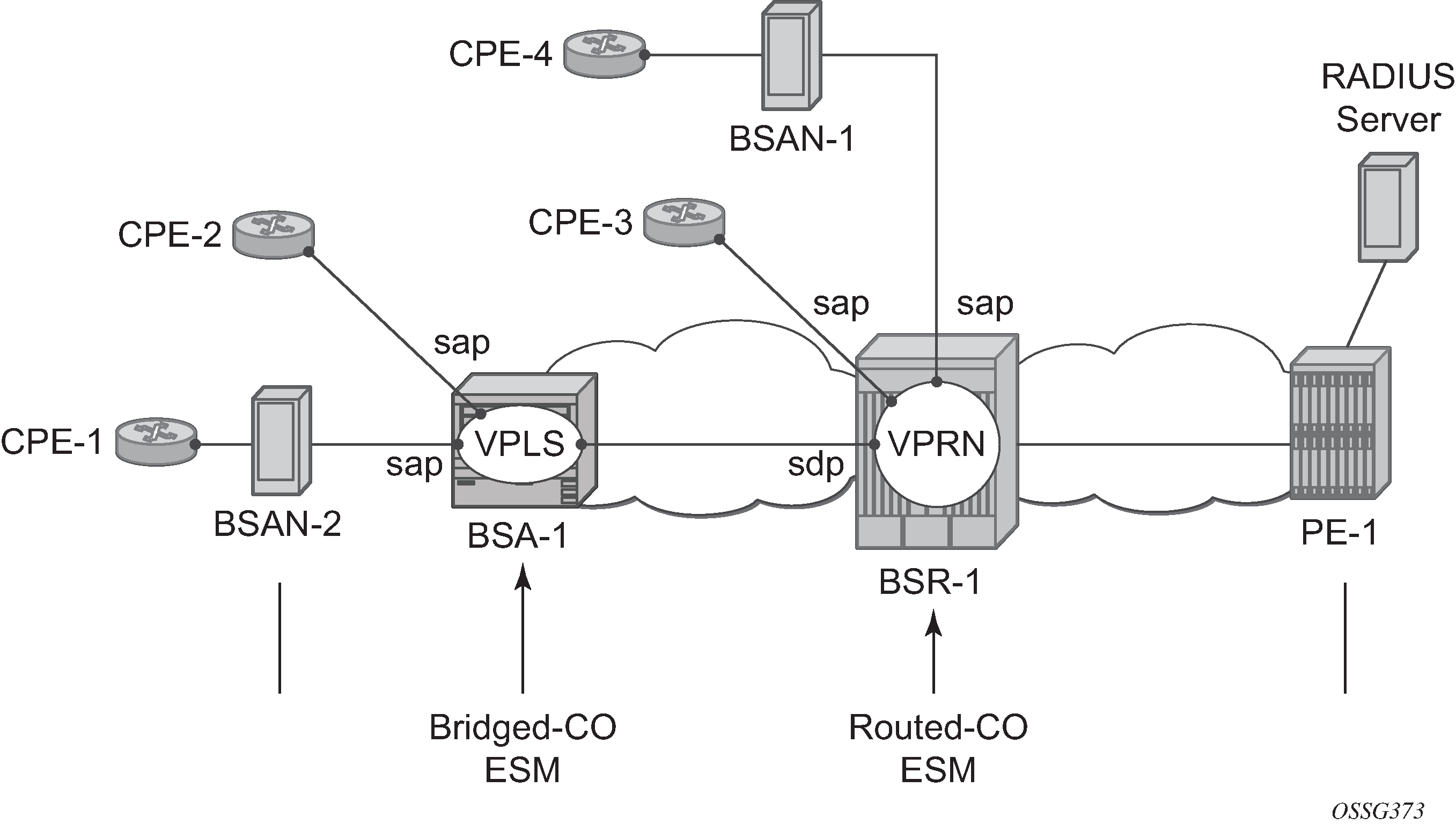
Configuration
ARP Hosts in a Bridged CO Environment
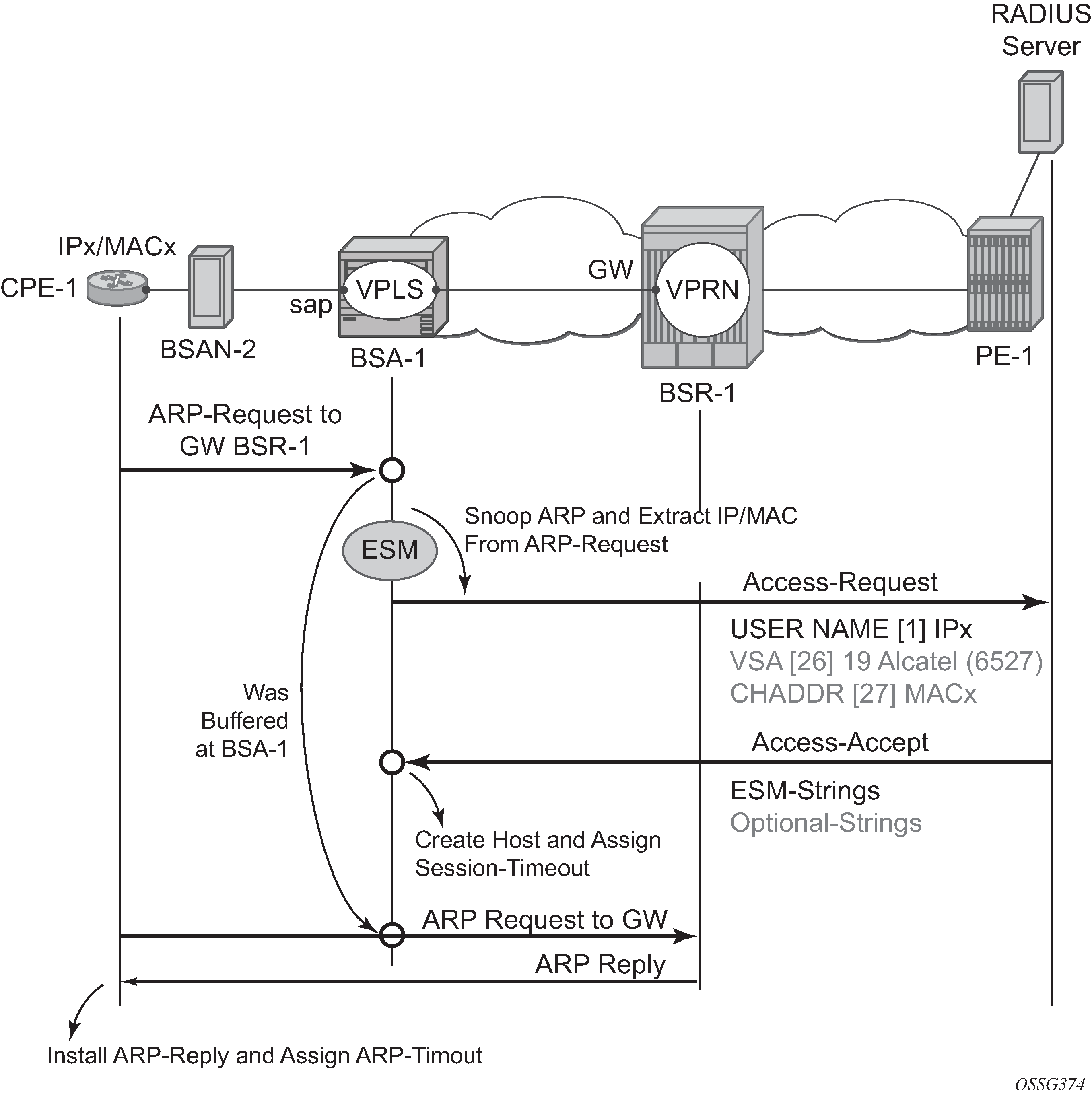
Enabling ARP-host for the Bridged CO model requires a composite service; a VPLS on the BSA node and a VPRN/IES on the BSR node. RADIUS authentication and subscriber management, which mandates IP-MAC or NH-MAC type anti-spoofing, are mandatory for ARP hosts.
# on BSA-1
configure
service
vpls 2 customer 1 create
description "ARP host - Bridged CO"
stp
shutdown
exit
sap 1/1/1:1 create
authentication-policy "authentication-1"
anti-spoof ip-mac
sub-sla-mgmt
sub-ident-policy "sub-id-default"
multi-sub-sap 10
no shutdown
exit
arp-host
no shutdown
exit
exit
spoke-sdp 12:2 create
exit
no shutdown
exit
exit
exit
The RADIUS authentication policy does not require any specific parameter settings. The RADIUS username attribute will always contain the host IP address, meaning that the authentication policy parameter user-name-format is irrelevant for ARP hosts.
configure
subscriber-mgmt
authentication-policy "authentication-1" create
password ALU
radius-authentication-server
server 1 address 172.16.1.1 secret ALU
exit
# re-authentication is optional
re-authentication
# only required when RADIUS Disconnect is needed (optional)
accept-authorization-change
exit
exit
The CPE ARPs are snooped and the first CPE ARP triggers a RADIUS accept-request. Any subsequent ARPs will trigger RADIUS re-authentication only if the ARP host configurable min-auth-interval is expired and if the previously defined re-authentication parameter is set. The initial ARP is only forwarded to the BSR-1 upon successful RADIUS authentication by means of a RADIUS access-accept message. The same RADIUS access-accept message and passing the several session limit checks, triggers the instanciation of the host.
The BSR-1 node requires a VPRN/IES as part of the composite service. No ARP-host-specific parameters are required on the BSR-1 for the bridged CO model.
# on BSR-1
configure service
vprn 1 customer 1 create
route-distinguisher 64496:1
auto-bind-tunnel
resolution-filter
ldp
exit
resolution filter
exit
vrf-target target:64496
interface "int-BSA1-p2mp-1" create
description "ARP host - Bridged CO" address 10.2.0.6/29
ip-mtu 1500
spoke-sdp 21:2 create
exit
exit
exit
exit
ARP Hosts in a Routed CO Environment
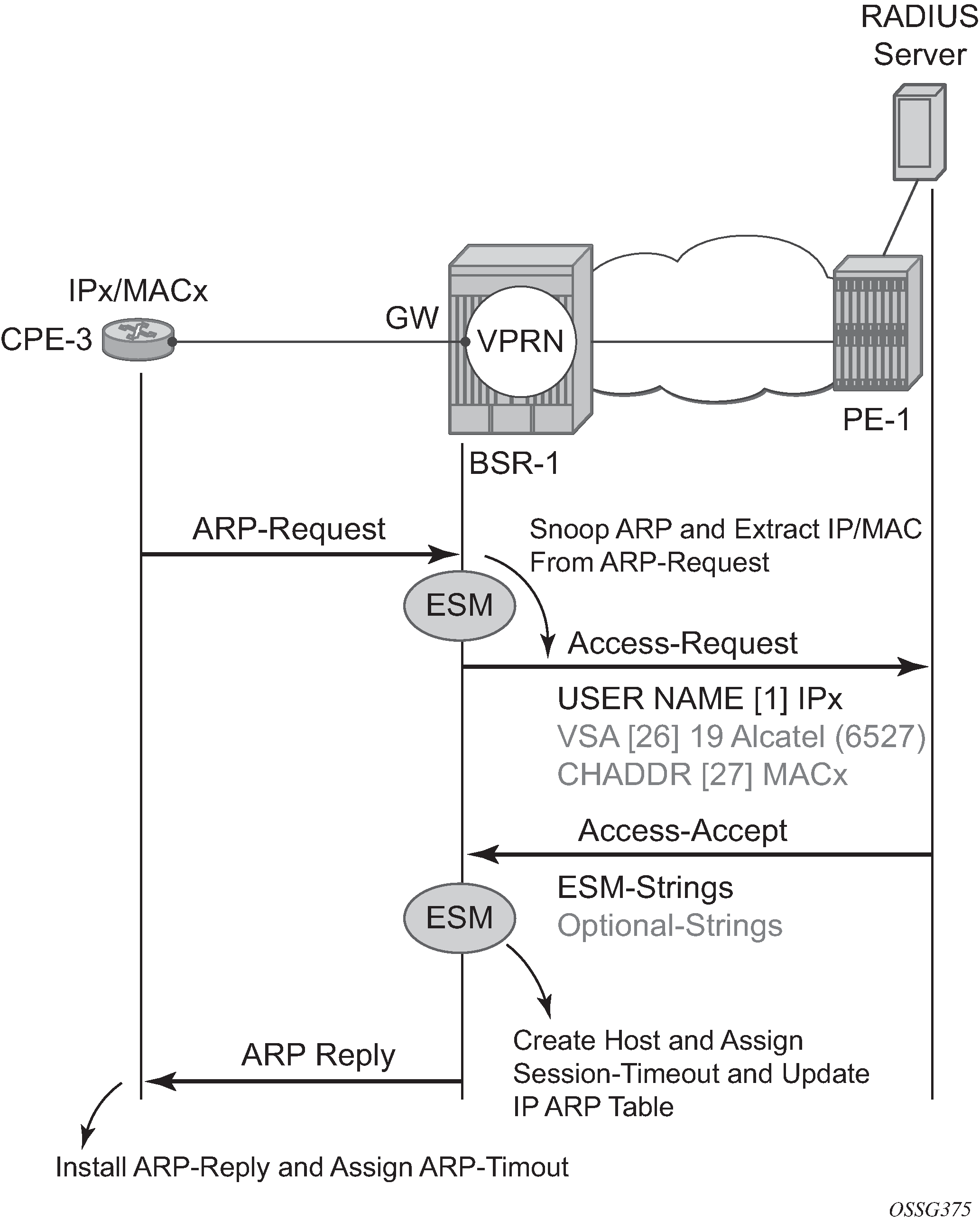
Enabling ARP-host for the routed CO model is identical for VPRN and IES services. RADIUS authentication and subscriber management, which mandates IP-MAC or NH-MAC type anti-spoofing, are mandatory for ARP hosts.
The initial ARP will, only upon successful RADIUS authentication and passing the several sessions limit checks, create the ARP host. The ARP reply or update of the IP ARP table is not performed on any unsuccessful RADIUS authentication.
# on BSR-1
configure service
vprn 1 customer 1 create
route-distinguisher 64496:1
auto-bind-tunnel
resolution-filter
ldp
exit
resolution filter
exit
vrf-target target:64496:1
subscriber-interface "sub-int-1" create
description "ARP host - Routed CO" address 10.1.0.6/29
group-interface "group-int-1" create
authentication-policy "authentication-1"
sap 1/1/1:1 create
anti-spoof ip-mac
sub-sla-mgmt
sub-ident-policy "sub-id-default"
no shutdown
exit
exit
arp-host
no shutdown
exit
exit
exit
exit
exit
RADIUS User Configuration Bridged/Routed CO
The username in the RADIUS access request is always the statically configured IP address from the CPE and configured as key in the RADIUS users file. The RADIUS Framed-Route attribute is not required and is silently ignored (if returned to BSA/BSR node).
"10.1.0.1" Auth-Type := Local, User-Password == ALU
Alc-Subsc-ID-Str = "arp-host-routed-%{User-name}",
Alc-Subsc-Prof-Str = "sub-profile-1",
Alc-SLA-Prof-Str = "sla-profile-1"
"10.2.0.1" Auth-Type := Local, User-Password == ALU
Alc-Subsc-ID-Str = "arp-host-bridged-%{User-name}",
Alc-Subsc-Prof-Str = "sub-profile-1",
Alc-SLA-Prof-Str = "sla-profile-1"
Setup and Debugging of ARP Host
Identical methodologies are used to debug/setup and troubleshoot ARP hosts for the bridged or the Routed CO model. The Routed CO model is used as an example through the rest of this section on ARP hosts.
There are two modes of ARP host debugging: all and dropped-only. The dropped-only mode shows all cases where the creation of the ARP host will be unsuccessful.
By default, all enabled ARP hosts on a service will be monitored. More specific filtering on a particular IP, MAC or SAP is optional.
All main traps are by default cyclically logged in log-id 99 and can be viewed anytime.
debug service id 1 arp-host mode all
ARP host mandate RADIUS authentication and a separate debug option is available for RADIUS interaction.
debug radius detail
CPE-3 with statically configured IP1 10.1.0.1 sends an ARP to the BSR-1 gateway.
1 2015/06/22 15:48:00.72 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.1:1812 id 2 len 79 vrid 1 pol authentication-1
USER NAME [1] 8 10.1.0.1
PASSWORD [2] 16 gy3yhtT5dF9YYilHtiiNNk
NAS IP ADDRESS [4] 4 192.0.2.2
VSA [26] 19 Alcatel(6527)
CHADDR [27] 17 00:00:0a:01:00:01
"
2 2015/06/22 15:48:00.74 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 2 len 94 from 172.16.1.1:1812 vrid 1 pol authentication-1
VSA [26] 26 Alcatel(6527)
SUBSC ID STR [11] 24 arp-host-routed-10.1.0.1
VSA [26] 15 Alcatel(6527)
SUBSC PROF STR [12] 13 sub-profile-1
VSA [26] 15 Alcatel(6527)
SLA PROF STR [13] 13 sla-profile-1
"
3 2015/06/22 15:48:00.75 CEST MINOR: DEBUG #2001 vprn1 ARP Host
"ARP Host: Created ARP host
VPRN 1, SAP 1/1/1:1
IP: 10.1.0.1
MAC: 00:00:0a:01:00:01
"
A:BSR-1# show log log-id 99
---snip---
58 2015/06/22 15:48:00.73 CEST WARNING: SVCMGR #2500 Base Subscriber created
"Subscriber arp-host-routed-10.1.0.1 has been created in the system"
The user name in the RADIUS access-request contains the CPE’s IP address independent from the user-name-format defined in the authentication policy. The MAC address of the ARP host is included in the RADIUS access-request as VSA (Alc-Client-Hardware-Addr) independent on the include-radius-attribute mac-address parameter from the authentication policy.
The show service id 1 arp-host command displays all active ARP hosts on this service.
A:BSR-1# show service id 1 arp-host
===============================================================================
ARP host table, service 1
===============================================================================
IP Address Mac Address Sap Id Remaining MC
Time Stdby
-------------------------------------------------------------------------------
10.1.0.1 00:00:0a:01:00:01 1/1/1:1 03h59m23s
-------------------------------------------------------------------------------
Number of ARP hosts : 1
===============================================================================
A:BSR-1#
More specific filters such as sap, ip-address, mac and others can be used to show dedicated ARP hosts created on the BSR.
A:BSR-1# show service id 1 arp-host ip-address 10.1.0.1 detail
===============================================================================
ARP hosts for service 1
===============================================================================
Service ID : 1
IP Address : 10.1.0.1
MAC Address : 00:00:0a:01:00:01
Subscriber-interface : sub-int-1
Group-interface : group-int-1
SAP : 1/1/1:1
Remaining Time : 03h59m15s
Sub-Ident : "arp-host-routed-10.1.0.1"
Sub-Profile-String : "sub-profile-1"
SLA-Profile-String : "sla-profile-1"
App-Profile-String : ""
ARP host ANCP-String : ""
ARP host Int Dest Id : ""
Category-Map-Name : ""
RADIUS-User-Name : "10.1.0.1"
Session Timeout (s) : 14400
Start Time : 06/22/2015 15:48:00
Last Auth : 06/22/2015 15:48:00
Last Refresh : 06/22/2015 15:48:00
Persistence Key : N/A
-------------------------------------------------------------------------------
Number of ARP hosts : 1
===============================================================================
A:BSR-1#
Dynamically created ARP hosts are added as /32 addresses to the routing table and marked with protocol type Sub Mgmt. Routes of the Sub Mgmt protocol type are not exported into vpn-ipv4 by the default vrf-target policy. A separate, dedicated vrf-export policy is required to achieve this.
A:BSR-1# show router 1 route-table 10.1.0.0/24 longer
===============================================================================
Route Table (Service: 1)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.1.0.0/29 Local Local 00h04m21s 0
sub-int-1 0
10.1.0.1/32 Remote Sub Mgmt 00h00m56s 0
[group-int-1] 0
-------------------------------------------------------------------------------
No. of Routes: 2
Flags: n = Number of times nexthop is repeated
B = BGP backup route available
L = LFA nexthop available
S = Sticky ECMP requested
===============================================================================
A:BSR-1#
Specific ARP host counters can be shown or cleared using the CLI command show/clear service id 1 ARP host statistics.
A:BSR-1# show service id 1 arp-host statistics
===============================================================================
ARP host statistics
===============================================================================
Num Active Hosts : 1
Received Triggers : 5
Ignored Triggers : 3
Ignored Triggers (overload) : 0
SHCV Checks Forced : 0
Hosts Created : 1
Hosts Updated : 1
Hosts Deleted : 0
Authentication Requests Sent : 4
===============================================================================
A:BSR-1#
The ARP hosts mandate Enhanced Subscriber managed (ESM) and therefore an anti-spoofing configuration (IP-MAC or NH-MAC). The anti-spoofing table with active hosts can be viewed with the command show service id 1 subscriber-hosts.
A:BSR-1# show service id 1 subscriber-hosts
=============================================================
Subscriber Host table
=============================================================
Sap Subscriber
IP Address
MAC Address PPPoE-SID Origin Fwding State
-------------------------------------------------------------
1/1/1:1 arp-host-routed-10.1.0.1
10.1.0.1
00:00:0a:01:00:01 N/A ARP-Host Fwding
-------------------------------------------------------------
Number of subscriber hosts : 1
=============================================================
A:BSR-1#
An ARP host can be manually deleted from the system using one of the two following methods:
clear service id 1 arp-host
RADIUS disconnect message
Using the first method, clear service id 1 arp-host and omitting any more specific parameter results in the removal of all ARP hosts in this service. Extra filters such as ip-address, mac or sap-id are required to remove a specific ARP host.
*A:BSR-1# clear service id 1 arp-host
- arp-host {all | mac <ieee-address> | sap <sap-id> | ip-address <ip-address[/mask]> }
- arp-host {port <port-id> | {inter-dest-id <intermediate-destination-id> | no-inter-dest-id} [port <port-id>] }
- arp-host statistics [sap <sap-id> | interface <interface-name>]
A:BSR-1# clear service id 1 arp-host ip-address 10.1.0.1
Using the second method, RADIUS disconnect always result in the removal of a unique host because nas-port-id and framed-ip-address are mandatory parameters in the RADIUS disconnect message. This RADIUS disconnect message is used also for other host-types.
nas-port-id = 1/1/1:1
framed-ip-address=10.1.0.1
RADIUS disconnect messages are, for security reasons, rejected by default. The RADIUS disconnect messages can be accepted by enabling the accept-authorization-change parameter in the authentication policy. The debug radius detail command and show subscriber-mgmt authentication coa-statistics can be used during troubleshooting.
10 2015/06/22 15:51:08.43 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Disconnect Request(40) id 247 len 44 from 172.16.1.1:46749 vrid 1
SESSION ID [44] 22 02DAFF0000000255881288
"
11 2015/06/22 15:51:08.42 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Disconnect Ack(41) 172.16.1.1:46749 id 247 len 26 vrid 1 pol authentication-1
TERMINATE CAUSE [49] 4 Admin Reset(6)
"
12 2015/06/22 15:51:08.43 CEST MINOR: DEBUG #2001 vprn1 ARP Host
"ARP Host: Removed ARP host
VPRN 1, SAP 1/1/1:1
IP: 10.1.0.1
MAC: 00:00:0a:01:00:01
"
In both cases the ARP host with an IP address is removed from the system together with all related state information (such as an anti-spoof filter and an IP ARP entry).
ARP Host Session Timeout
The remaining time is initialized at the ARP host session timeout value (300s to 14400s) and starts counting down when an ARP host is instanciated. Ultimately the host is removed from the system when the remaining time becomes zero. Any subsequent arp-request or arp-reply for this host results in the remaining value to be reset to the host session timeout value defined.
The default assigned session timeout at ARP host creation time is 14400 seconds, a value which can be overruled by the optional RADIUS attribute session-Timeout but not by the node group-interface arp-timeout parameter.
RADIUS values lower than 300 seconds will be silently adjusted to 300 seconds and values above 14400 seconds are topped silently to 14400 seconds.
"10.1.0.1" Auth-Type := Local, User-Password == ALU
Alc-Subsc-ID-Str = "arp-host-routed-%{User-name}",
Alc-Subsc-Prof-Str = "sub-profile-1",
Alc-SLA-Prof-Str = "sla-profile-1",
Session-Timeout = 300 # value in seconds
A:BSR-1# show service id 1 arp-host
===============================================================================
ARP host table, service 1
===============================================================================
IP Address Mac Address Sap Id Remaining MC
Time Stdby
-------------------------------------------------------------------------------
10.1.0.1 00:00:0a:01:00:01 1/1/1:1 00h04m56s
-------------------------------------------------------------------------------
Number of ARP hosts : 1
===============================================================================
A:BSR-1#
A:BSR-1# show service id 1 arp-host ip-address 10.1.0.1 detail
===============================================================================
ARP hosts for service 1
===============================================================================
Service ID : 1
IP Address : 10.1.0.1
MAC Address : 00:00:0a:01:00:01
Subscriber-interface : sub-int-1
Group-interface : group-int-1
SAP : 1/1/1:1
Remaining Time : 00h04m39s
Sub-Ident : "arp-host-routed-10.1.0.1"
Sub-Profile-String : "sub-profile-1"
SLA-Profile-String : "sla-profile-1"
App-Profile-String : ""
ARP host ANCP-String : ""
ARP host Int Dest Id : ""
Category-Map-Name : ""
RADIUS-User-Name : "10.1.0.1"
Session Timeout (s) : 300
Start Time : 06/22/2015 15:53:11
Last Auth : 06/22/2015 15:53:11
Last Refresh : 06/22/2015 15:53:11
Persistence Key : N/A
-------------------------------------------------------------------------------
Number of ARP hosts : 1
===============================================================================
A:BSR-1#
Typical time related parameters of the ARP host are:
Parameter |
Comment |
|---|---|
Session Timeout |
Time value in seconds and retrieved by default or by the RADIUS Accept message and pasted into the remaining time at the moment of ARP host creation or RADIUS re-authentication. |
Remaining Time |
The remaining time before the ARP host is deleted from the system (updated each time an ARP request/reply is seen for this host). |
Start Time |
Time and date when this host was created (first ARP received). |
Last Auth |
Time and date when this host was last RADIUS authenticated. |
Last Refresh |
Time and date when last ARP was received for this host. |
ARP hosts do not have an expiry timer in the ARP table and have type managed.
A:BSR-1# show service id 1 arp 10.1.0.1
===============================================================================
ARP Table
===============================================================================
IP Address MAC Address Type Expiry Interface SAP
-------------------------------------------------------------------------------
10.1.0.1 00:00:0a:01:00:01 Managed 00h00m00s group-int-1 1/1/1:1
===============================================================================
A:BSR-1#
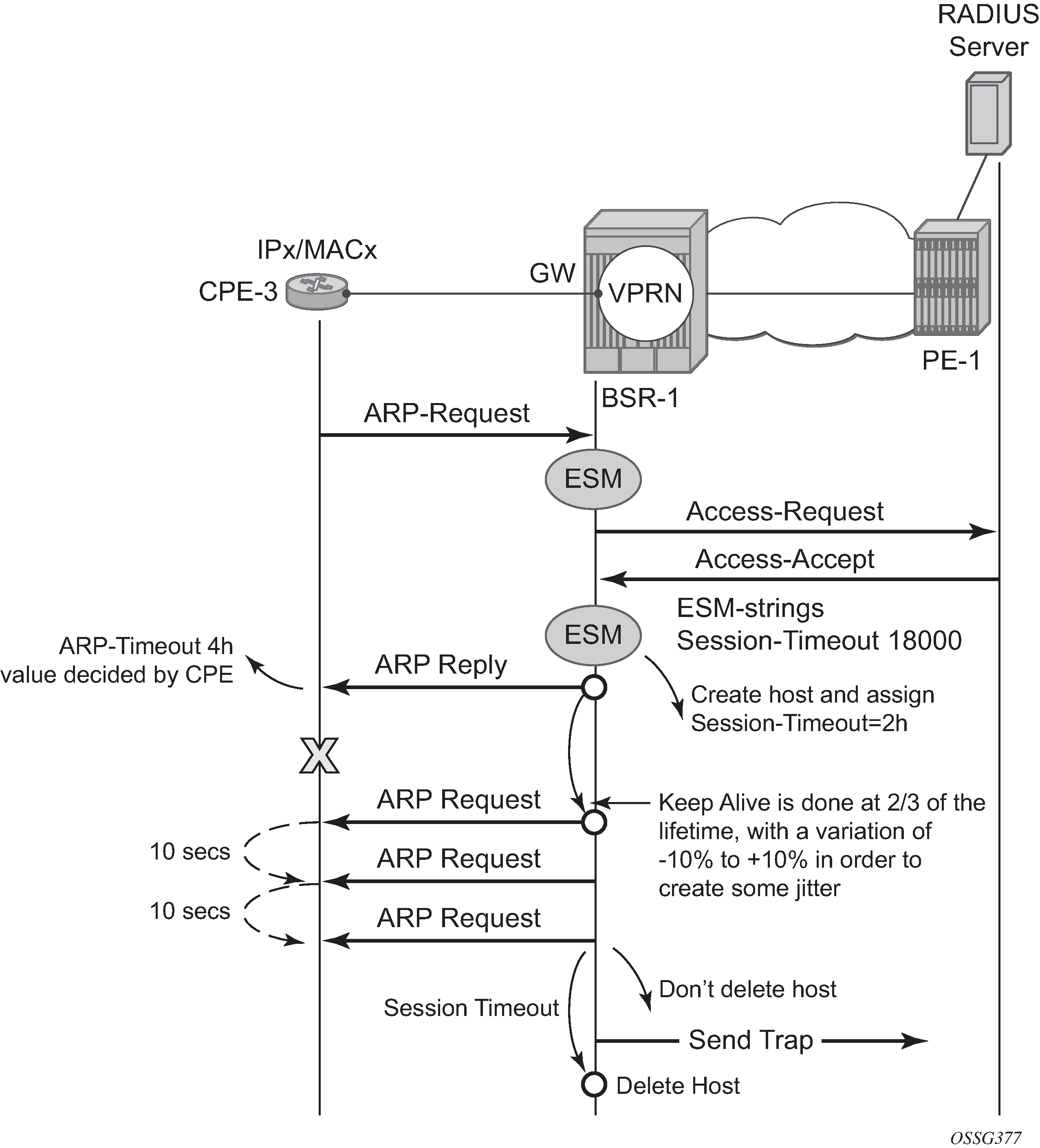
An automatic mechanism is implemented to handle the possible asynchronicity between the ARP session timeout values installed on the BSR and the ARP timeouts installed on the CPE. This mechanism is mostly effective in case the timeout on the CPE exceeds the timeout on the BSR. In this case, the BSR session would expire, resulting in a host removal with a deletion of the corresponding anti-spoof entry because the CPE ARP request arrives too late. This CPE ARP request will however recreate the session but requires the complete setup of the host RADIUS authentication included. This mechanism causes unwanted service interruption for this ARP host.
A better approach, which is implemented in an automatic way, and illustrated in ARP Host Session Timeout Example is an ARP request triggered by the BSR towards the CPE prior to the session timeout. The ARP reply sent by the CPE then will reset the remaining lifetime for the ARP host to the session timeout. If the ARP reply is received outside the min-auth-interval window and the parameter re-authentication in the authentication policy is set, then RADIUS re-authentication is executed. This re-authentication mechanism is described later in theThrottling Toward RADIUSThrottling Toward RADIUS section.
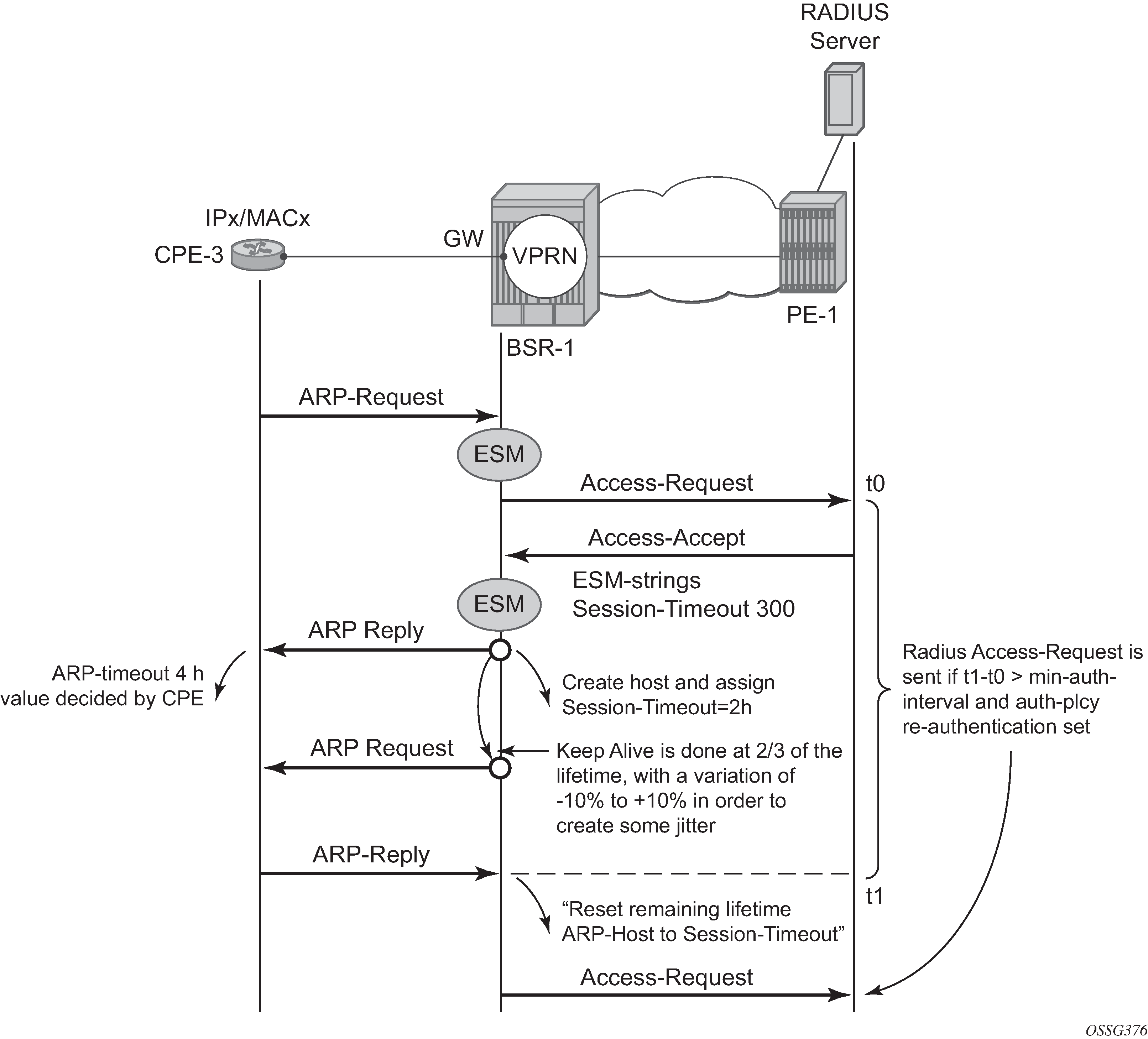
This mechanism, also known as automatic Subscriber Host Connectivity Verification (SHCV), will prevent that the host will be deleted and re-created, resulting in undesired service interruptions, in case asynchronous CPE-BSR ARP session values would be used.
The debug service id 1 host-connectivity-verify command shows the sequence of events and can be used for troubleshooting. Debugging and ARP host counters show the automatic SHCV mechanism with an active CPE.
4 2015/06/25 16:32:45.21 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Forced Check Scheduled
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
5 2015/06/25 16:32:46.11 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Forced Check
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
6 2015/06/25 16:32:46.12 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Received Reply
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
7 2015/06/25 16:32:46.12 CEST MINOR: DEBUG #2001 vprn1 ARP Host
"ARP Host: Updated ARP host
VPRN 1, SAP 1/1/1:1
IP: 10.1.0.1
MAC: 00:00:0a:01:00:01
"
8 2015/06/25 16:34:29.34 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Received Reply
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
9 2015/06/25 16:34:29.34 CEST MINOR: DEBUG #2001 vprn1 ARP Host
"ARP Host: Updated ARP host
VPRN 1, SAP 1/1/1:1
IP: 10.1.0.1
MAC: 00:00:0a:01:00:01
"
A:BSR-1# show service id 1 arp-host statistics
===============================================================================
ARP host statistics
===============================================================================
Num Active Hosts : 1
Received Triggers : 3
Ignored Triggers : 0
Ignored Triggers (overload) : 0
SHCV Checks Forced : 1
Hosts Created : 1
Hosts Updated : 2
Hosts Deleted : 0
Authentication Requests Sent : 1
===============================================================================
A:BSR-1#
CPEs that are not active and which therefore do not respond to ARP requests as part of the automatic SHCV check will be rechecked three times with 10 second intervals.
The number of retries and the interval cannot be changed. A trap is generated, but the ARP host is not removed and will remain until the session-timeout expires or until the host revives. This mechanism is displayed in Trap Generation Example.
16 2015/06/25 16:42:38.21 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Forced Check Scheduled
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
17 2015/06/25 16:42:39.11 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Forced Check
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
18 2015/06/25 16:42:49.11 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Forced Check
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
19 2015/06/25 16:42:59.11 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Forced Check
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
20 2015/06/25 16:43:09.11 CEST MINOR: DEBUG #2001 vprn1 SHCV
"SHCV: Connectivity Lost
1/1/1:1
ARP host 10.1.0.1 00:00:0a:01:00:01"
21 2015/06/25 16:43:10.21 CEST MINOR: DEBUG #2001 vprn1 ARP Host
"ARP Host: Removed ARP host
VPRN 1, SAP 1/1/1:1
IP: 10.1.0.1
MAC: 00:00:0a:01:00:01
"
Throttling Toward RADIUS
A new ARP request from the ARP host will trigger RADIUS re-authentication only when the min-auth-interval has expired. The minimum RADIUS authentication interval between two consecutive authentication attempts for the same ARP host is by default 15 minutes but can range between 1 and 6000 minutes.
configure
service
vprn 1 customer 1 create
---snip---
arp-host
min-auth-interval 60 # value in minutes
no shutdown
exit
exit
exit
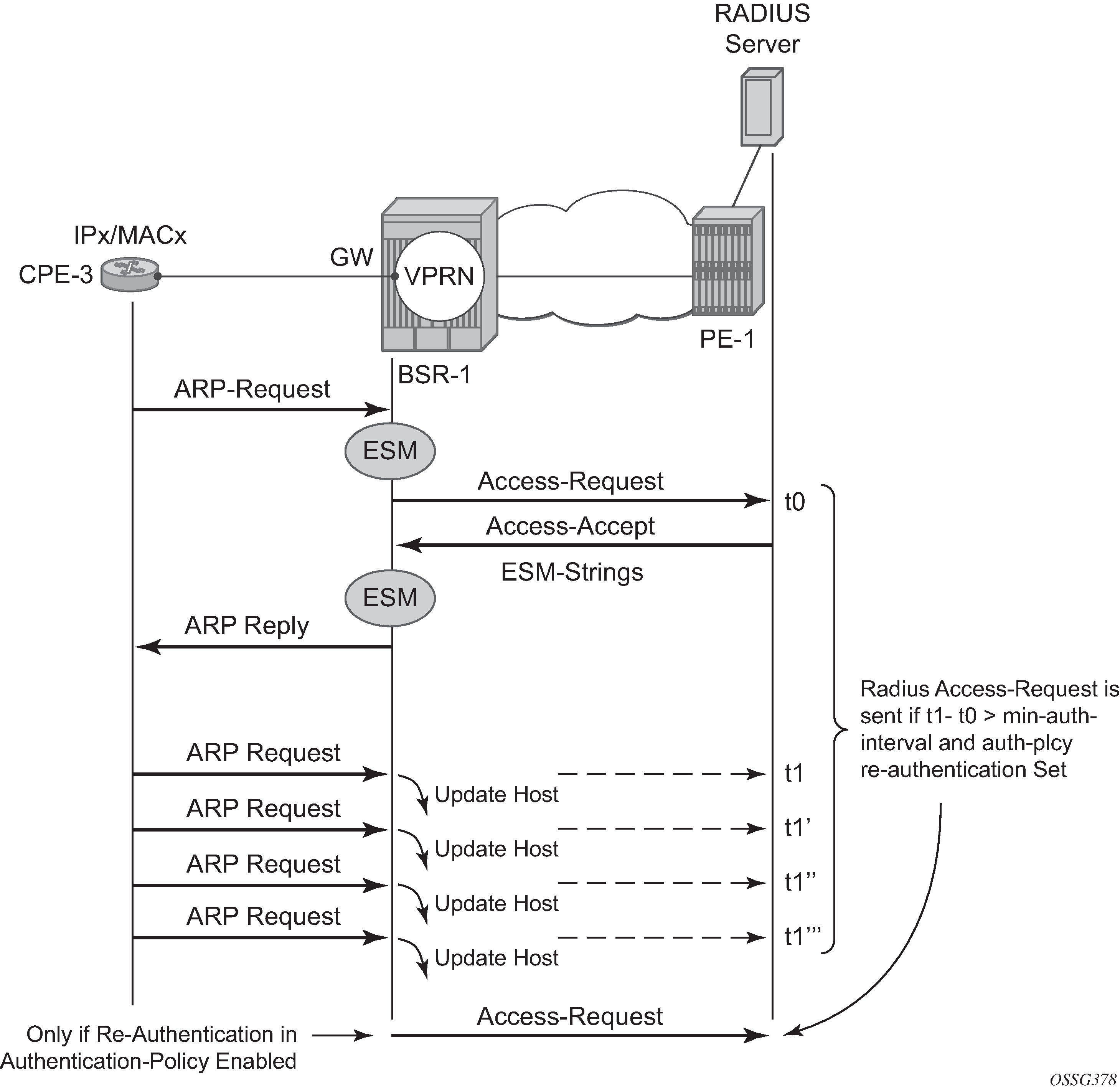
A:BSR-1# show service id 1 arp-host detail
===============================================================================
ARP hosts for service 1
===============================================================================
Service ID : 1
IP Address : 10.1.0.1
MAC Address : 00:00:0a:01:00:01
Subscriber-interface : sub-int-1
Group-interface : group-int-1
SAP : 1/1/1:1
Remaining Time : 00h04m31s
Sub-Ident : "arp-host-routed-10.1.0.1"
Sub-Profile-String : "sub-profile-1"
SLA-Profile-String : "sla-profile-1"
App-Profile-String : ""
ARP host ANCP-String : ""
ARP host Int Dest Id : ""
Category-Map-Name : ""
RADIUS-User-Name : "10.1.0.1"
Session Timeout (s) : 300
Start Time : 06/22/2015 15:59:32
Last Auth : 06/22/2015 15:59:32
Last Refresh : 06/22/2015 16:00:33
Persistence Key : N/A
-------------------------------------------------------------------------------
Number of ARP hosts : 1
===============================================================================
A:BSR-1#
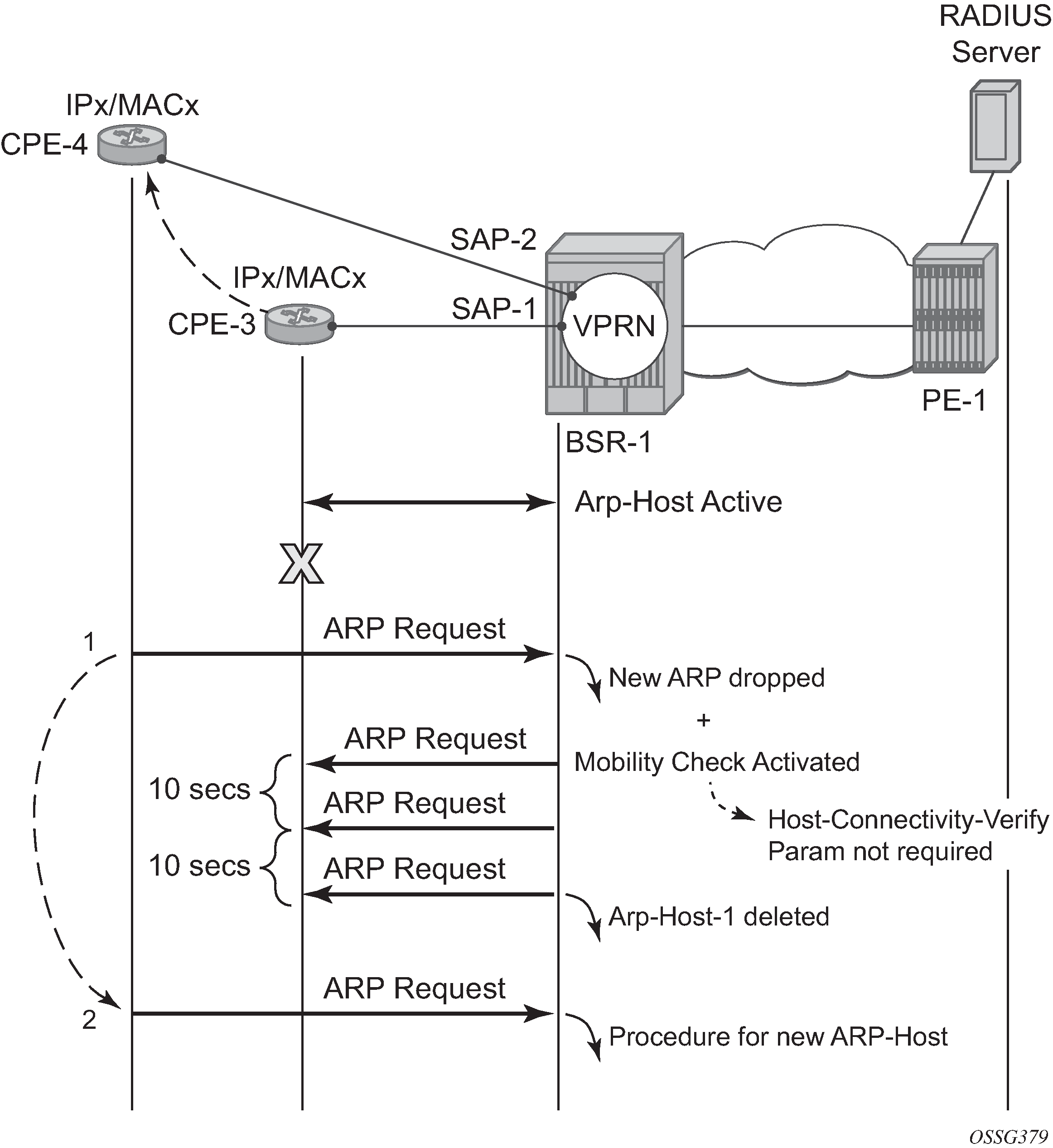
ARP Host Mobility
In order for ARP host mobility to function, host-connectivity-verification must not be enabled. This is different when compared with DHCP host mobility.
The implementation for routed CO is displayed in ARP Host Mobility Example and works the same for bridged CO. The mac-pinning command in routed CO context has no influence on this behavior.
ARP Host Persistency
ARP hosts can be made persistent across reboots and do not differ with other host types such as DHCP hosts.
configure
system
persistence
subscriber-mgmt
location cf3:
exit
exit
The persistence key and the index into the persistency file are linked to the ARP host at host creation time.
A:BSR-1# show service id 1 arp-host detail
===============================================================================
ARP hosts for service 1
===============================================================================
Service ID : 1
IP Address : 10.1.0.1
MAC Address : 00:00:0a:01:00:01
Subscriber-interface : sub-int-1
Group-interface : group-int-1
SAP : 1/1/1:1
Remaining Time : 00h04m32s
Sub-Ident : "arp-host-routed-10.1.0.1"
Sub-Profile-String : "sub-profile-1"
SLA-Profile-String : "sla-profile-1"
App-Profile-String : ""
ARP host ANCP-String : ""
ARP host Int Dest Id : ""
Category-Map-Name : ""
RADIUS-User-Name : "10.1.0.1"
Session Timeout (s) : 300
Start Time : 06/22/2015 15:59:32
Last Auth : 06/22/2015 15:59:32
Last Refresh : 06/22/2015 16:03:33
Persistence Key : 0x00000000
-------------------------------------------------------------------------------
Number of ARP hosts : 1
===============================================================================
*A:BSR-1#
The content of the stored record is viewed with the tools dump persistency command using the persistency key as a record number.
*A:BSR-1# tools dump persistence submgt record 0x00000000
----------------------------------------
Persistence Record
----------------------------------------
Client : submgt
Persist-Key : 0x00000000
Filename : cf3:\submgmt.011
Entries : Index FedHandle Last Update Action Valid
000040 0x00000000 2015/06/22 14:01:31 (UTC) ADD Yes
Data : 243 bytes
Host Type : ARP host
Service ID : 1
SAP ID : 1/1/1:1
NH MAC : 00:00:0a:01:00:01
Created : 2015/06/22 13:59:32 (UTC)
IP : 10.1.0.1
Session Timeout: 300 (seconds)
RADIUS Fallback: NO
Acct-Sess-Id : 02DAFF00000008558814C4
Multi-Sess-Id : 02DAFF00000009558814C4
Class Attr : 0 bytes
User-Name : "10.1.0.1"
host is authenticated by radius: true
Subscriber-Id : "arp-host-routed-10.1.0.1"
Sub-Profile-Str: "sub-profile-1"
SLA-Profile-Str: "sla-profile-1"
*A:BSR-1#
Session Limitation Options
The maximum number of allowed arp-hosts in a bridged CO model can be configured with the per SAP parameter host-limit in the range of 1 to 32767.
configure
service
vpls 2
---snip---
sap 1/1/3:1
arp-host
# default value for host-limit is 1
host-limit 1
no shutdown
exit
exit
exit
The maximum number of allowed arp-hosts in a routed CO model can be configured with the per group interface parameter host-limit in the range of 1 to 32767 and/or by the sap-host-limit parameter.
configure
service
vprn 1
---snip---
arp-host
# default value for host-limie is 1
host-limit 1
# default value for sap-host-limit is 1
sap-host-limit 1
no shutdown
exit
exit
Specific ESM-related host limit mechanisms such as sla-profile host-limit and sub-sla-mgmt multi-sub-sap also apply to ARP hosts but are not further elaborated in this section.
Debugging arp-host mode dropped-only indicates the dropped reason and a logging trap is included in the standard log 99.
56 2015/06/22 16:08:35.37 CEST MINOR: DEBUG #2001 vprn1 ARP Host
"ARP Host: Dropped trigger
VPRN 1, SAP 1/1/1:1
Problem: Interface limit (1) of ARP hosts reached
IP: 10.1.0.2
MAC: 00:00:0a:01:00:02
"
*A:BSR-1# show log log-id 99
---snip---
78 2015/06/22 16:08:55.52 CEST WARNING: SVCMGR #2520 vprn1 ARP Host Population Error
"ARP host table population error on SAP 1/1/1:1 in service 1 - Interface limit (1) of ARP hosts reached"
Increasing the sap-host-limit to 100 and the host-limit to 2000 results in the following summary:
*A:BSR-1# show service id 1 arp-host summary
====================================================================
ARP host Summary, service 1
====================================================================
Interface Name Used Provided Admin State
--------------------------------------------------------------------
group-int-1 1 2000 inService
--------------------------------------------------------------------
Interfaces: 1 1
--------------------------------------------------------------------
====================================================================
*A:BSR-1#
Conclusion
This chapter provides configuration and troubleshooting commands for dynamic ARP hosts. ARP hosts can be instantiated in a Layer 2 bridged CO (VPLS) environment as well as in a Layer 3 Routed CO (IES/VPRN subscriber interface) context.