Virtual Residential Gateway Home Pool Management
This chapter describes virtual residential gateway home pool management.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are applicable to SR OS Release 14.0.R3.
Overview
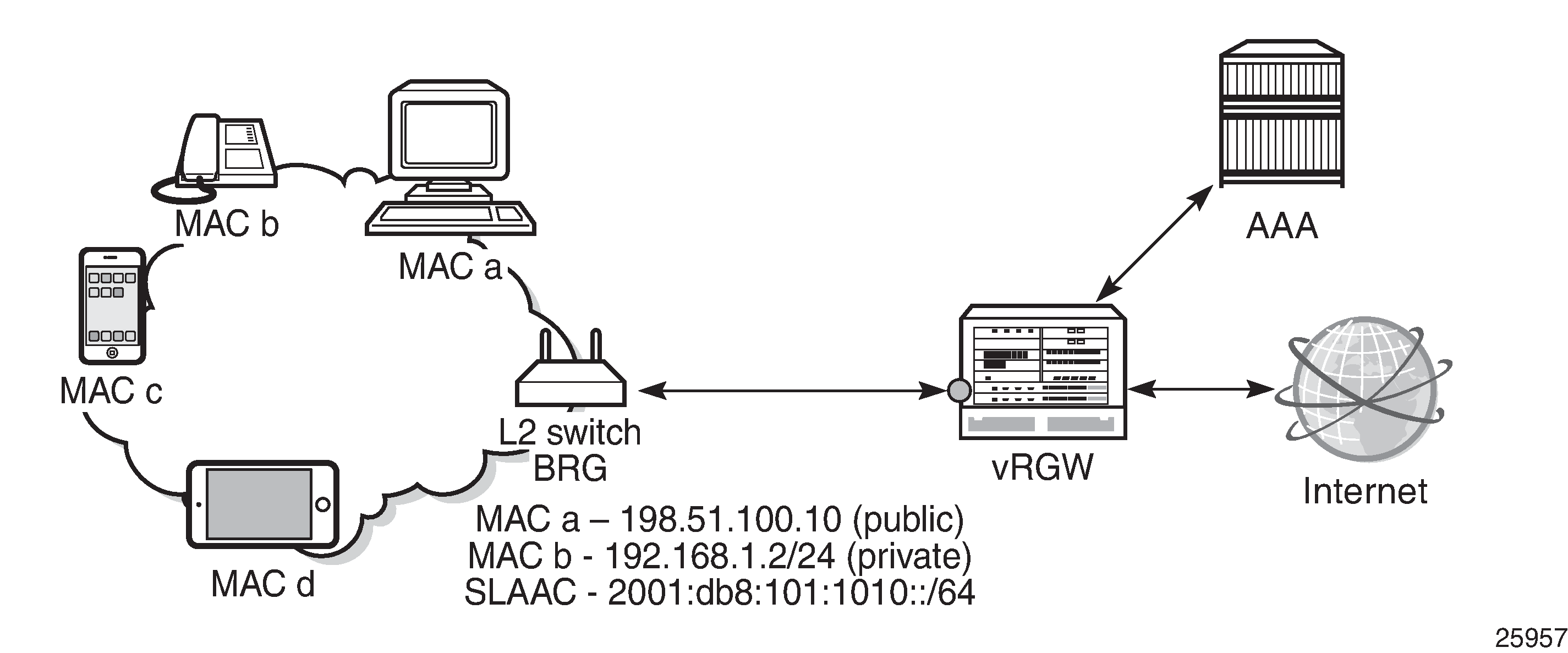
In the virtual residential gateway model, the Layer 3 (L3) functions are moved out of the traditional residential gateway (RGW) and into the network; see Virtual Residential Gateway in the Network with Bridged Residential Gateway at Home. Examples of L3 functions moved to the network are:
DHCPv4
Network Address Translation (NAT)
Firewalling
Universal Plug and Play
The in-home equipment interconnecting all devices in the home is referred to as the bridged residential gateway (BRG). The BRG only handles Layer 2 (L2) connectivity (for example, Ethernet and WiFi) and is always operating in bridged mode. The BRG has an L2 uplink connecting it to the virtual residential gateway (vRGW), either through a direct link or through tunneling technology. The vRGW handles all L3 connectivity.
For the vRGW to offer IPv4 connectivity to the devices in the home network, the vRGW provides the following features:
Private addresses from a single home address pool are offered. The address pools can overlap between homes.
Sticky or static addresses provide a fixed device to IP mapping.
Public addresses can be assigned, to enable home servers to be publicly accessible.
A demilitarized (DMZ) host can be defined.
Because multiple homes are allowed to use the same private subnet, the vRGW requires L2-aware NAT. L2-aware NAT is handled in the "L2-aware NAT (with dNAT and MNPs)" chapter in 7450 ESS, 7750 SR, and VSR Multiservice ISA and ESA Advanced Configuration Guide for Classic CLI.
For the vRGW to offer IPv6 connectivity to the devices in the home network, the vRGW provides the following features:
A /64 SLAAC prefix is assigned per home.
IA_NA address allocation using DHCPv6 relay or proxy is supported, following standard ESM rules.
Prefix Delegation (PD) is not supported.
Using the vRGW model, the ISP now has visibility on the MAC and IP addresses used by the in-home devices.
DHCP and IP Address Management
The vRGW has the following characteristics for DHCPv4:
-
One pool per home
-
IP overlap between homes
-
Sticky IP addresses
Sticky IP addresses are DHCPv4 addresses assigned to devices that need to have the same address all the time and are provided through the DHCP protocol. Home servers, network-attached storage (NAS), and network printers are examples of devices that typically are configured with sticky IP addresses. The vRGW sets a flag indicating that the IP address is reserved, to avoid assigning the sticky address to devices that do not have this requirement.
Static IP addresses can be used and configured for devices that do not use or support the DHCP protocol, and are configured manually on the device. The static IP address used can be a public or a private address. Traffic to and from private addresses undergoes NAT, whereas traffic to and from public addresses does not undergo NAT. The vRGW drops DHCP messages originating from devices that are considered to be static.
The vRGW requires the use of IPoE sessions for supporting BRGs, and creates an IPoE session per device. Static devices require at least one dynamic host to be created first so that the associated SAP or tunnel can be defined to send traffic over. Each static device is authenticated individually using RADIUS to retrieve the per-device parameters.
The vRGW has the following characteristics for IPv6:
-
Both SLAAC and IA_NA allocation are supported.
-
Static IPv6 addresses are not supported. However, a static IPv4 device can get an IPv6 SLAAC prefix if IPoE-linking is enabled.
-
No per-home pool is supported for IA_NA, but DHCPv6 can be relayed to an external or local DHCPv6 server.
The vRGW only operates in IPoE bridged mode, so that multiple hosts on the same BRG share the same SLAAC/64 prefix. Only one SLAAC prefix per BRG is supported.
Prefix delegation (PD) is not supported in the vRGW.
Demilitarized Zone (DMZ)
When a DMZ host is specified within a home, all downstream traffic not matching an existing flow or port forwarding rule is sent to that host. Without a DMZ host, this traffic is dropped. DMZ requires a single port-reservation block to be defined on the outside L2-aware NAT range.
Configuration
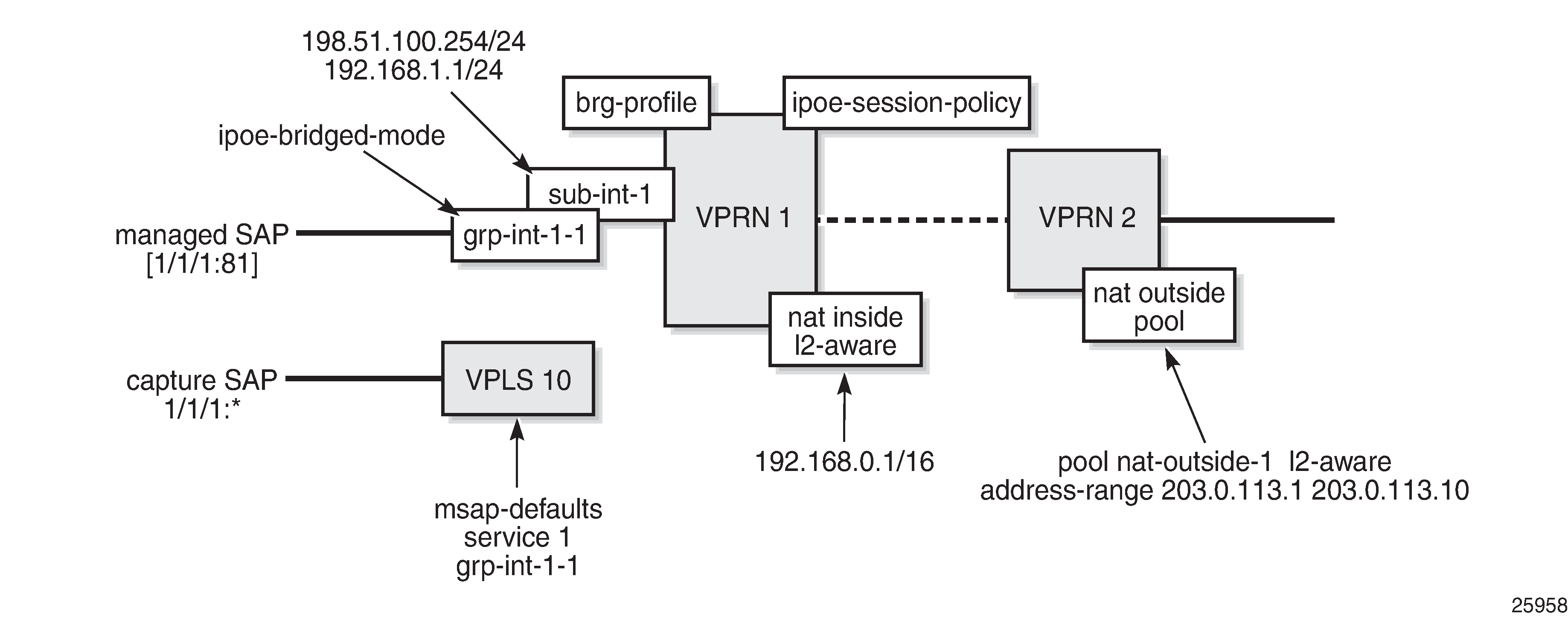
The services configuration overview shown in Services Configuration Overview applies to the examples used throughout this chapter. For L2-aware NAT, two routed services are configured. In this example, VPRN-1 provides the connection toward the customer premises, and hosts the NAT inside addresses. VPRN-2 provides the connection toward the Internet, and hosts the NAT outside addresses. Addresses from the documentation range as defined in RFC 5737 are used for the public addresses.
The examples in this chapter use capture and managed SAPs. The capture SAP is created manually on VPLS-10, and the managed SAPs are created dynamically on VPRN-1. Also, static SAPs can be used to support BRGs, but in that case the configuration file can grow rapidly when many SAPs are required.
Services Configuration
An excerpt of the configuration of VPRN-1 follows. This VPRN contains subscriber interface sub-int-1 with group interface grp-int-1-1, thereby using the routed central office (CO) model. No static SAPs are configured; managed SAPs will be created when triggers are received on VPLS-10. The IPoE session policy required for the vRGW is sess-pol-SAP-MAC, and the default BRG profile used is brg-prof-1.
Relay and proxy scenarios are configured for DHCPv4 and DHCPv6. SLAAC prefixes are taken from the wan-host prefix range, and must be advertised to devices using router-advertisement (RA) messages in response to router-solicit (RS) messages. For that purpose, group interface grp-int-1-1 is configured in its IPv6 context to support router advertisement and router solicitation. Also IPoE bridged mode is enabled in this context, so that the same SLAAC prefix can be allocated multiple times to the same SAP.
RADIUS authentication is enabled through authentication policy radius-AUTH. The inside L2-aware NAT range is 192.168.0.1/16, and the DHCP pool subnets defined in the BRG profile must belong to that range; see the ESM Configuration part in this chapter.
configure
service
vprn 1 customer 1 create
---snip---
route-distinguisher 64496:1
interface "int-DHCP" create
address 10.11.11.1/32
ipv6
address 2001:db8::11/128
local-dhcp-server "dhcp6-SRVC1"
exit
loopback
exit
subscriber-interface "sub-int-1" create
address 198.51.100.254/24
address 192.168.1.1/24
ipv6
link-local-address fe80::1
subscriber-prefixes
prefix 2001:db8:101::/48 wan-host
exit
exit
group-interface "grp-int-1-1" create
ipv6
router-advertisements
prefix-options
autonomous
exit
no shutdown
exit
dhcp6
proxy-server
no shutdown
exit
relay
server 2001:db8::11
no shutdown
exit
exit
router-solicit
inactivity-timer hrs 2
no shutdown
exit
ipoe-bridged-mode
exit
---snip---
arp-populate
dhcp
proxy-server
emulated-server 198.51.100.254
no shutdown
exit
trusted
lease-populate 128
gi-address 198.51.100.254
no shutdown
exit
authentication-policy "radius-AUTH"
ipoe-session
ipoe-session-policy "sess-pol-SAP-MAC"
sap-session-limit 128
no shutdown
exit
brg
default-brg-profile "brg-prof-1"
no shutdown
exit
oper-up-while-empty
exit
exit
nat
inside
l2-aware
address 192.168.0.1/16
exit
exit
exit
no shutdown
exit
exit
exit
VPRN-2 defines an interface to the outside world, int-VPRN2-INTERNET, as well as the outside L2-aware NAT range, which is 203.0.113.1 up to 203.0.113.10. Port-reservation blocks is set to 1, to ensure a unique outside IP per subscriber (home) and correct operation of the DMZ feature.
configure
service
vprn 2 customer 1 create
route-distinguisher 64496:2
interface "int-VPRN2-INTERNET" create
---snip---
exit
nat
outside
pool "nat-outside-1" nat-group 1 type l2-aware create
port-reservation blocks 1
address-range 203.0.113.1 203.0.113.10 create
exit
no shutdown
exit
exit
exit
no shutdown
exit
exit
exit
VPLS-10 defines the capture SAP on port 1/1/1. The triggers configured are dhcp, dhcp6, and rtr-solicit. The authentication policy and the IPoE session policy used are the same as the ones used on VPRN-1, and are radius-AUTH and sess-pol-SAP-MAC, respectively. The MSAP defaults indicate that the managed SAPs must be created on service 1, group interface grp-int-1-1, using MSAP policy msap-pol-MSAP.
configure
service
vpls 10 customer 1 create
description "VPLS for capture SAPs - BRG-demo"
stp
shutdown
exit
sap 1/1/1:* capture-sap create
description "capture SAP for MSAP creation on 1/1/1"
trigger-packet dhcp dhcp6 rtr-solicit
ipoe-session
ipoe-session-policy "sess-pol-SAP-MAC"
no shutdown
exit
msap-defaults
group-interface "grp-int-1-1"
policy "msap-pol-MSAP"
service 1
exit
authentication-policy "radius-AUTH"
no shutdown
exit
no shutdown
exit
exit
exit
RADIUS User Configuration
Although a protocol conversion and mediation platform (PCMP) will be used in conjunction with an external controller, for demonstration purposes this chapter relies on a RADIUS server only.
A sample RADIUS user configuration follows. The user’s MAC address is used for authenticating purposes. MAC address 00:0c:29:00:00:10 identifies the BRG. The addresses ranging from 00:0c:29:00:00:11 to 00:0c:29:00:00:1f identify the home devices connected to the same BRG so they all return the same Alc-BRG-Id. For the BRG, RADIUS provides primary and secondary DNS and NBNS servers, a set of reserved addresses, a DMZ address, a framed IPv6 prefix (used for SLAAC), a home-aware pool, and the BRG profile. The home pool subnet must be a subnet of the L2-aware inside subnet.
00:0c:29:00:00:10 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
Alc-BRG-Profile = "brg-prof-1",
Framed-IPv6-Prefix = 2001:db8:101:1010::/64,
Alc-DMZ-address = 192.168.1.254,
Alc-Home-Aware-Pool =
"192.168.1.1/24 192.168.1.100-192.168.1.254",
Alc-Reserved-Addresses =
"sticky 00:0c:29:00:00:11 192.168.1.110",
Alc-Reserved-Addresses +=
"static 00:0c:29:00:00:1f 192.168.1.254",
Alc-Reserved-Addresses +=
"static 00:0c:29:00:00:1e 198.51.100.110",
Alc-Portal-Url = "http://11.11.11.11",
Alc-Primary-Dns = 1.1.1.1,
Alc-Secondary-Dns = 1.1.2.2,
Alc-Primary-Nbns = 2.2.1.1,
Alc-Secondary-Nbns = 2.2.2.2,
Alc-Ipv6-Primary-DNS = 2001:db8:dddd:1::1,
Alc-Ipv6-Secondary-DNS = 2001:db8:dddd:2::1,
00:0c:29:00:00:11 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
00:0c:29:00:00:12 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
00:0c:29:00:00:13 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
00:0c:29:00:00:14 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
Alc-Primary-Dns = 1.1.3.3,
---snip---
The RADIUS server is allowed to return a SLAAC pool name using the Alc-SLAAC-IPv6-Pool attribute, but in that case local address assignment needs to be configured on the vRGW. See the ESM SLAAC Prefix Assignment via Local Address Server chapter for more information.
ESM Configuration
The subscriber management policies and profiles are defined as follows. The BRG profile brg-prof-1 provides an SLA profile, a sub-profile, a RADIUS server policy, plus the corresponding password, a RADIUS proxy server, and a DHCP pool. The DHCP pool is within the inside L2-aware NAT range defined for VPRN-1.
configure
subscriber-mgmt
ipoe-session-policy "sess-pol-SAP-MAC" create
exit
sla-profile "sla-prof-1" create
exit
sub-profile "sub-prof-1" create
nat-policy "nat-pol-1"
exit
sub-ident-policy "sub-ident-DIRECT" create
sub-profile-map
use-direct-map-as-default
exit
sla-profile-map
use-direct-map-as-default
exit
exit
msap-policy "msap-pol-MSAP" create
sub-sla-mgmt
def-sub-id use-sap-id
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
sub-ident-policy "sub-ident-DIRECT"
exit
exit
brg-profile "brg-prof-1" create
description "default BRG-profile, demo purposes"
sla-profile-string "sla-prof-1"
sub-profile-string "sub-prof-1"
dhcp-pool
subnet 192.168.1.1/24 start 192.168.1.2 end 192.168.1.254
exit
radius-authentication
password letmein
radius-server-policy "rad-serv-pol-RSP"
exit
exit
exit
exit
The RADIUS authentication and accounting policies are defined as follows.
configure
router
radius-server
server "radius-172.16.1.2" address 172.16.1.2 secret vsecret1 create
accept-coa
exit
exit
exit
exit
configure
aaa
radius-server-policy "rad-serv-pol-RSP" create
servers
router "Base"
source-address 192.0.2.1
server 1 name "radius-172.16.1.2"
exit
exit
exit
exit
configure
subscriber-mgmt
authentication-policy "radius-AUTH" create
description "Radius authentication policy"
password letmein
radius-authentication-server
source-address 192.0.2.1
exit
radius-server-policy "rad-serv-pol-RSP"
exit
radius-accounting-policy "radius-ACCT" create
update-interval 5
include-radius-attribute
mac-address
nat-port-range
subscriber-id
exit
radius-accounting-server
source-address 192.0.2.1
router "Base"
server 1 address 172.16.1.2 secret vsecret1
exit
exit
exit
exit
NAT Policy configuration
The NAT policy used in support for the BRGs is nat-pol-1, and refers to the outside address pool defined in VPRN-2.
configure
service
nat
nat-policy "nat-pol-1" create
pool "nat-outside-1" router 2
exit
exit
exit
exit
Operation and Verification
The following command shows the current BRG hosts. Six hosts are connected. The first host has a sticky address, the third a plain dynamic address, the fifth a public static address, and the last a private static address. The second and the fourth hosts correspond to the SLAAC hosts, and their allocation type is ‟not-applicable”. For the static hosts, no DHCP lease information is maintained.
*A:BNG# show subscriber-mgmt brg brg-hosts
===============================================================================
Bridged Residential Gateway hosts
===============================================================================
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:11
IP address : 192.168.1.110
Service : 1 (VPRN)
Allocation type : sticky-ip-address
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : true
Remaining lease time : 11479
Lease start time : 2016/09/19 20:51:22
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:11
IP address : 2001:db8:101:1010::
Service : 1 (VPRN)
Allocation type : not-applicable
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:14
IP address : 192.168.1.100
Service : 1 (VPRN)
Allocation type : dynamic
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : true
Remaining lease time : 11480
Lease start time : 2016/09/19 20:51:24
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:14
IP address : 2001:db8:101:1010::
Service : 1 (VPRN)
Allocation type : not-applicable
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1e
IP address : 198.51.100.110
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1f
IP address : 192.168.1.254
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
-------------------------------------------------------------------------------
No. of BRG hosts: 6
===============================================================================
*A:BNG#
The following command shows the active BRGs. Because all the hosts from the previous command belong to the same BRG, only a single BRG gateway exists. The SLAAC prefix, subnet, start address, end address, DMZ address, DNS addresses for IPv4 and IPv6, NBNS-1 and NBNS-2 addresses, and IPv4 and IPv6 portal addresses are obtained from the RADIUS server. ‟DMZ address in use” is set to ‟yes” because RADIUS returned the Alc-DMZ-address, and the outside L2 NAT pool has a single port-reservation block configured (ref. VPRN-2).
*A:BNG# show subscriber-mgmt brg gateways
===============================================================================
Bridged Residential Gateways
===============================================================================
Identifier : 00:0c:29:00:00:10
SLAAC prefix : 2001:db8:101:1010::/64
Subnet : 192.168.1.1/24
Subnet start address : 192.168.1.100
Subnet end address : 192.168.1.254
DMZ address : 192.168.1.254
DNS 1 v4 : 1.1.1.1
DNS 1 v6 : 2001:db8:dddd:1::1
DNS 2 v4 : 1.1.2.2
DNS 2 v6 : 2001:db8:dddd:2::1
NBNS 1 : 2.2.1.1
NBNS 2 : 2.2.2.2
DHCP lease time : 21600
DHCP stream destination : (Not Specified)
IPv4 portal URL : http://11.11.11.11
IPv6 portal URL : (Not Specified)
BRG profile : brg-prof-1
Subscriber profile : sub-prof-1
SLA profile : sla-prof-1
UPnP policy override : (Not Specified)
DMZ address in use : yes
Proxy authenticated : no
Ingress IPv4 filter override : N/A
Egress IPv4 filter override : N/A
Ingress IPv6 filter override : N/A
Egress IPv6 filter override : N/A
No QoS overrides found.
No Filter rules received.
-------------------------------------------------------------------------------
No. of gateways: 1
===============================================================================
*A:BNG#
The following command shows the active subscribers. Only a single subscriber exists, with two SLAAC hosts (origin is SLAAC), two dynamic hosts (origin is DHCP), and two ‟static” hosts (origin is AAA). Also, the NAT policy used and the outside IP address and the ports are shown.
*A:BNG# show service active-subscribers
===============================================================================
Active Subscribers
===============================================================================
-------------------------------------------------------------------------------
Subscriber 00:0c:29:00:00:10 (sub-prof-1)
-------------------------------------------------------------------------------
NAT Policy: nat-pol-1
Outside IP: 203.0.113.1 (vprn2)
Ports : 1024-5119
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
(1) SLA Profile Instance sap:[1/1/1:81] - sla:sla-prof-1
-------------------------------------------------------------------------------
IP Address
MAC Address Session Origin Svc Fwd
-------------------------------------------------------------------------------
192.168.1.110
00:0c:29:00:00:11 IPoE DHCP 1 Y
2001:db8:101:1010::/64
00:0c:29:00:00:11 IPoE SLAAC 1 Y
192.168.1.100
00:0c:29:00:00:14 IPoE DHCP 1 Y
2001:db8:101:1010::/64
00:0c:29:00:00:14 IPoE SLAAC 1 Y
198.51.100.110
00:0c:29:00:00:1e IPoE AAA 1 Y
192.168.1.254
00:0c:29:00:00:1f IPoE AAA 1 Y
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
Number of active subscribers : 1
-------------------------------------------------------------------------------
*A:BNG#
The following command shows the subscriber hierarchy for a single subscriber. This way it is apparent which host belongs to which IPoE session and on which SAP. The subscriber ID used is the MAC address of the BRG and is accompanied with the sub-profile used. The bridge ID is accompanied with the BRG profile. The NAT outside IP address is accompanied with the service number and the NAT policy.
*A:BNG# show service active-subscribers hierarchy subscriber "00:0c:29:00:00:10"
===============================================================================
Active Subscribers Hierarchy
===============================================================================
Hierarchy
-------------------------------------------------------------------------------
-- 00:0c:29:00:00:10 (sub-prof-1)
| brg-id: 00:0c:29:00:00:10 - brg-profile: brg-prof-1
| NAT Outside IP: 203.0.113.1 (vprn2) policy nat-pol-1
|
+-- sap:[1/1/1:81] - sla:sla-prof-1
|
|-- IPOE-session - mac:00:0c:29:00:00:11 - svc:1
| |
| |-- 192.168.1.110 - DHCP - L2Aware
| |
| +-- 2001:db8:101:1010::/64 - SLAAC
|
|-- IPOE-session - mac:00:0c:29:00:00:14 - svc:1
| |
| |-- 192.168.1.100 - DHCP - L2Aware
| |
| +-- 2001:db8:101:1010::/64 - SLAAC
|
|-- IPOE-session - mac:00:0c:29:00:00:1e - svc:1
| |
| +-- 198.51.100.110 - AAA
|
+-- IPOE-session - mac:00:0c:29:00:00:1f - svc:1
|
+-- 192.168.1.254 - AAA - L2Aware
===============================================================================
*A:BNG#
The following command shows the subscriber hosts on VPRN-1. All these hosts belong to the same subscriber, with subscriber ID 00:0c:29:00:00:10. The subscriber ID used is the MAC address of the BRG.
*A:BNG# show service id 1 subscriber-hosts
=============================================================
Subscriber Host table
=============================================================
Sap Subscriber
IP Address
MAC Address PPPoE-SID Origin Fwding State
-------------------------------------------------------------
[1/1/1:81] 00:0c:29:00:00:10
192.168.1.100
00:0c:29:00:00:14 N/A DHCP Fwding
[1/1/1:81] 00:0c:29:00:00:10
192.168.1.110
00:0c:29:00:00:11 N/A DHCP Fwding
[1/1/1:81] 00:0c:29:00:00:10
192.168.1.254
00:0c:29:00:00:1f N/A AAA Fwding
[1/1/1:81] 00:0c:29:00:00:10
198.51.100.110
00:0c:29:00:00:1e N/A AAA Fwding
[1/1/1:81] 00:0c:29:00:00:10
2001:db8:101:1010::/64
00:0c:29:00:00:11 N/A IPoE-SLAAC Fwding
[1/1/1:81] 00:0c:29:00:00:10
2001:db8:101:1010::/64
00:0c:29:00:00:14 N/A IPoE-SLAAC Fwding
-------------------------------------------------------------
Number of subscriber hosts : 6
=============================================================
*A:BNG#
The DHCP lease state table on VRPN-1 can then be shown with the following command. These addresses are taken from the Alc-Home-Aware-Pool as defined by the RADIUS server. The 192.168.1.110 address is a sticky address returned in the Alc-Reserved-Addresses attribute. Obviously, no entries appear for the static hosts.
*A:BNG# show service id 1 dhcp lease-state
===============================================================================
DHCP lease state table, service 1
===============================================================================
IP Address Mac Address Sap/Sdp Id Remaining Lease MC
LeaseTime Origin Stdby
-------------------------------------------------------------------------------
192.168.1.100 00:0c:29:00:00:14 [1/1/1:81] 03h11m20s Radius
192.168.1.110 00:0c:29:00:00:11 [1/1/1:81] 03h11m18s Radius
-------------------------------------------------------------------------------
Number of lease states : 2
===============================================================================
*A:BNG#
Because a public static IP address is returned by the RADIUS server when authenticating the BRG, a ‛static’ BRG host was created, and the routing table is adjusted accordingly.
*A:BNG# show router 1 route-table
===============================================================================
Route Table (Service: 1)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.11.11.1/32 Local Local 11h48m56s 0
int-DHCP 0
192.168.1.0/24 Local Local 11h48m56s 0
sub-int-1 0
198.51.100.0/24 Local Local 11h48m56s 0
sub-int-1 0
198.51.100.110/32 Remote Sub Mgmt 11h48m41s 0
[grp-int-1-1] 0
-------------------------------------------------------------------------------
No. of Routes: 4
Flags: n = Number of times nexthop is repeated
B = BGP backup route available
L = LFA nexthop available
S = Sticky ECMP requested
===============================================================================
*A:BNG#
The following command shows the corresponding L2-aware hosts. Only three L2-aware hosts are created, using private IP addresses on the ‛inside’, and public address on the ‛outside’. Traffic for these hosts passes through the ISA. Traffic for the static public address (10.0.10.110) does not undergo NAT and does not pass through the ISA.
*A:BNG# show service nat l2-aware-hosts
===============================================================================
Layer-2-Aware NAT hosts
===============================================================================
Subscriber : 00:0c:29:00:00:10
Inside IP address : 192.168.1.100
-------------------------------------------------------------------------------
Policy : nat-pol-1
Outside router : 2
Outside IP address : 203.0.113.1
Subscriber : 00:0c:29:00:00:10
Inside IP address : 192.168.1.110
-------------------------------------------------------------------------------
Policy : nat-pol-1
Outside router : 2
Outside IP address : 203.0.113.1
Subscriber : 00:0c:29:00:00:10
Inside IP address : 192.168.1.254
-------------------------------------------------------------------------------
Policy : nat-pol-1
Outside router : 2
Outside IP address : 203.0.113.1
-------------------------------------------------------------------------------
No. of hosts: 3
===============================================================================
*A:BNG#
The following command shows the corresponding IPoE sessions. There is one session per device/MAC-address, so there are four IPoE sessions for this subscriber.
*A:BNG# show service id 1 ipoe session
===============================================================================
IPoE sessions for svc-id 1
===============================================================================
Sap Id Mac Address Up Time MC-Stdby
Subscriber-Id
[CircuitID] | [RemoteID]
-------------------------------------------------------------------------------
[1/1/1:81] 00:0c:29:00:00:11 0d 11:48:42
00:0c:29:00:00:10
[1/1/1:81] 00:0c:29:00:00:14 0d 11:48:40
00:0c:29:00:00:10
[1/1/1:81] 00:0c:29:00:00:1e 0d 11:48:42
00:0c:29:00:00:10
[1/1/1:81] 00:0c:29:00:00:1f 0d 11:48:42
00:0c:29:00:00:10
-------------------------------------------------------------------------------
CID | RID displayed when included in session-key
Number of sessions : 4
===============================================================================
*A:BNG#
With this single subscriber connected, the following command shows the managed hosts that are created.
*A:BNG# show service id 1 managed-hosts type aaa
===============================================================================
Managed aaa hosts
===============================================================================
IP address MAC address
-------------------------------------------------------------------------------
192.168.1.254/32 00:0c:29:00:00:1f
198.51.100.110/32 00:0c:29:00:00:1e
-------------------------------------------------------------------------------
No. of Managed hosts: 2
===============================================================================
*A:BNG#
Conclusion
Using a BRG in the home network instead of a full-fledged L3 RGW offers network operators a view on the IP addresses and MAC addresses used by home devices, enabling them to provide per-device service offerings. Integrating BRGs in their networks can help the operators to optimize the revenue stream.