Virtual Residential Gateway Authentication Scenarios
This chapter describes virtual residential gateway authentication scenarios.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 14.0.R3.
Overview
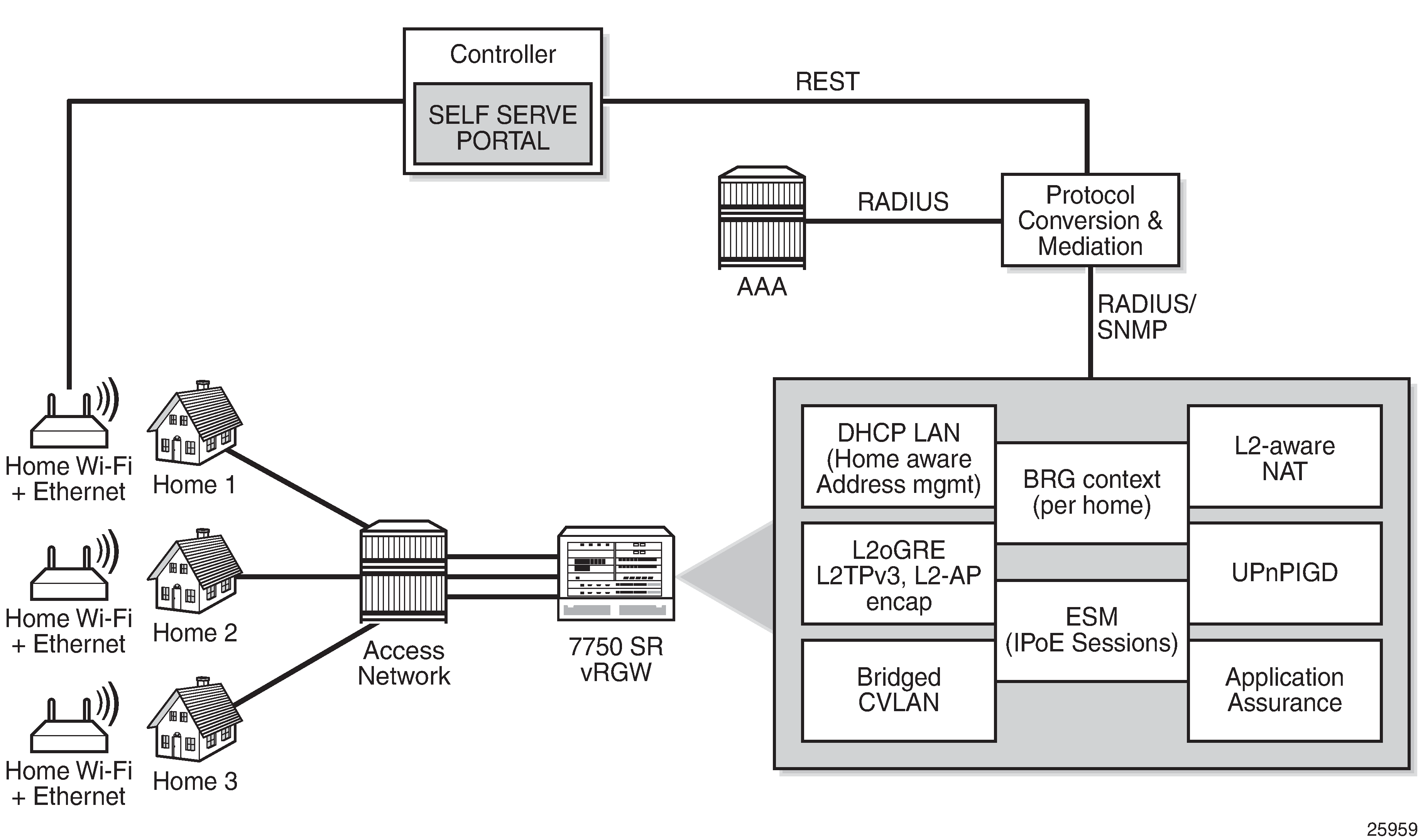
In the virtual residential gateway (vRGW) model, the Layer 3 (L3) functions are moved out of the traditional residential gateway (RGW) and into the network. The Virtual Residential Gateway Home Pool Management chapter provides the rationale for this scenario, and describes how services must be configured for the service router to support this model.
The home network can be self-managed through a service portal, where end users can connect and change home-specific settings; see BRG and home device management. The portal logic is implemented in a controlling entity providing a RESTful interface. A protocol conversion and mediation platform (PCMP) is needed to translate the RESTful interface into RADIUS (and SNMP), and vice versa. The PCMP operates in conjunction with the 5620 SAM. In the remainder of this chapter, PCMP and the controller are represented as a single component.
Managing individual BRGs requires the vRGW to maintain a context for every BRG, so each BRG is identified through the BRG ID. This context is created when authenticating the BRG, and stores the home-level settings. The BRG context is deleted when the BRG is not deemed alive anymore.
The BRG ID can be derived from any of the parameters in the RADIUS Access-Request message, such as the SAP, tunnel-source, or called-station ID by a controlling entity; see the Implicit authentication and Explicit authentication sections that follow in this chapter. Typically, the MAC address of the BRG serves as the BRG ID, and that is what is used throughout this chapter.
The vRGW supports two scenarios for authenticating bridged gateways and their hosts:
Explicit authentication
Implicit authentication
Explicit authentication
Two main phases are distinguished in the explicit authentication scenario; see Explicit BRG authentication. The first phase is the BRG authentication phase, the second phase is the device authentication phase. The example in Explicit BRG authentication uses IPv4, but also works with IPv6.
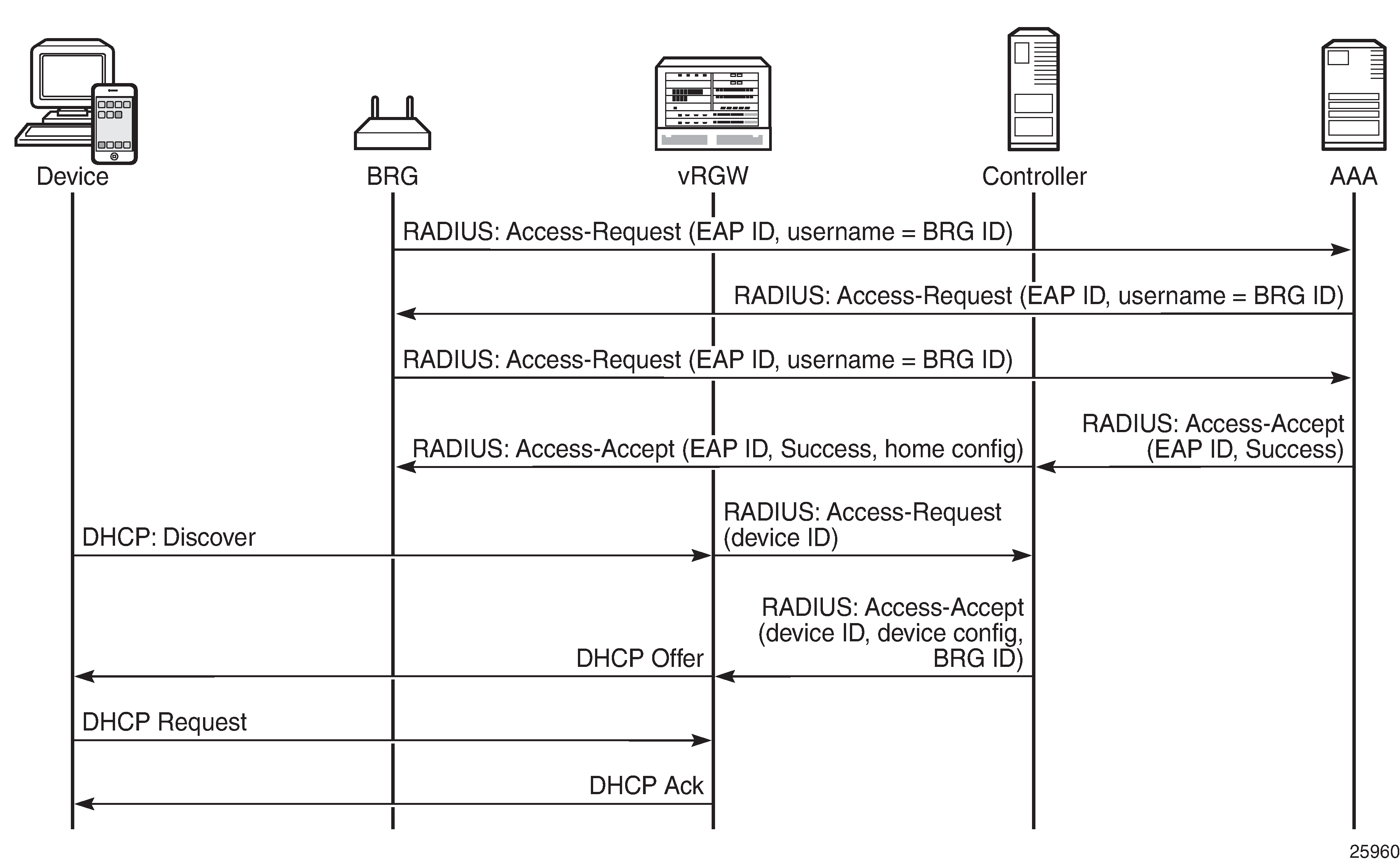
The first message in the first phase is an Access-Request message sent by the BRG toward the AAA/RADIUS server, and uses the extensible authentication protocol (EAP). This message is proxied by the vRGW as well as by the controller to the AAA server, and the BRG ID is used as the username. The last message of the first phase is the Access-Accept message. When the controller receives this message from the AAA server, it fetches and adds the per-home configuration parameters to the Access-Accept message before forwarding this message to the vRGW.
The second phase starts with the Discover message of a typical Discover-Offer-Request-Ack (DORA) message sequence. The vRGW then initiates device authentication toward the controller, which returns the BRG ID and, optionally, device-specific configuration data in an Access-Accept message. The controller usually will not proxy device authentication toward the AAA server. Typically, the RADIUS protocol is used between the vRGW and the controller. As such, the vRGW will send an Access-Request message to the controller for every new device, including static devices, to get the per-device configuration.
Usually, the vRGW combines the home-specific data with the device-specific data, where the more specific device data overrules the home-specific data. The combined data is then used to create the corresponding ESM hosts and IPoE sessions.
If the home-specific data includes Alc-Reserved-Addresses attributes defining static devices, these devices are authenticated automatically as soon as at least one dynamic device is connected.
The explicit authentication scenario requires the BRG profile to include a RADIUS proxy server; see the Configuration section in this chapter for a practical example.
Implicit authentication
In the implicit authentication scenario, the BRG is authenticated when the first device connects to the vRGW; see Implicit BRG authentication for an example.
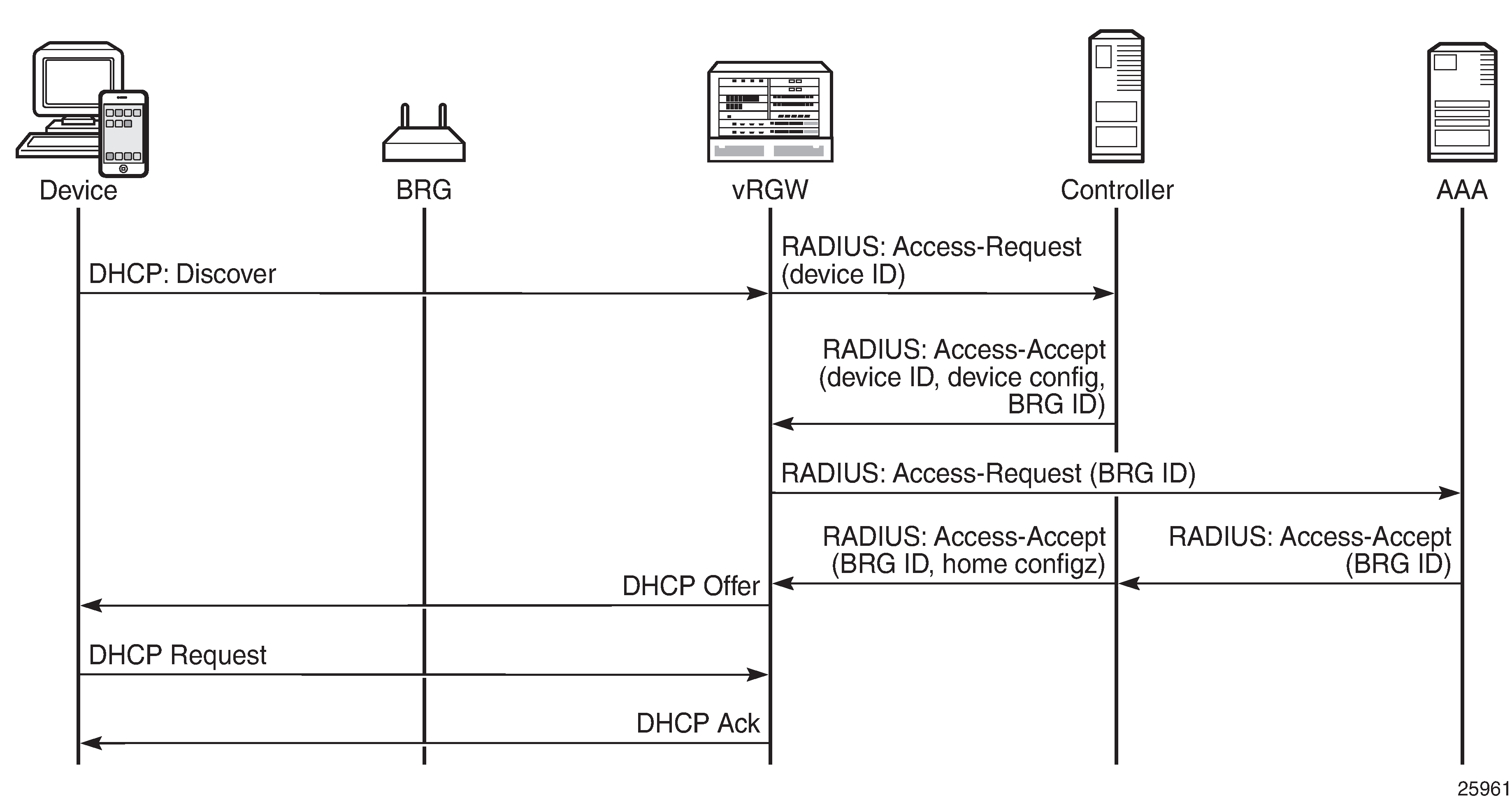
In Implicit BRG authentication, the Discover message triggers the vRGW to send an Access-Request message toward the controller. The controller returns device-specific data including the BRG ID. Because there is no context for this BRG yet, the vRGW starts BRG authentication toward the AAA/RADIUS server. The controller proxies this message, and on return adds the home-specific data to the Access-Accept message. The overall result is that the vRGW now knows the home- and device-specific data.
As with the explicit authentication scenario, the combined data is then used to create the corresponding ESM hosts and IPoE sessions.
No separate BRG authentication is required when subsequent devices connect and device authentication returns a BRG ID that is already known to the vRGW.
As with the explicit authentication scenario, if the home-specific data includes Alc-Reserved-Addresses attributes defining static home devices, the static devices are authenticated automatically when at least one dynamic device is connected.
The implicit authentication scenario requires the BRG profile to include a RADIUS authentication context defining a RADIUS server policy and a password; see the Configuration section in this chapter for an example.
Connectivity verification and BRG deletion
For the purpose of clearing resources when these resources are not needed anymore, the vRGW performs the BRG connectivity verification and deletion process. When BRG connectivity is considered lost, the BRG and its hosts are deleted automatically.
Parameters controlling the BRG connectivity verification and deletion process are located in the BRG profile context:
*A:BNG>config>subscr-mgmt>brg-profile#
connectivity-verification count 3 timeout 30 retry-time 900
count <nr-of-attempts> : [1..5] – default: 3
timeout <timeout-seconds> : [5..60] – default: 30
retry-time <retry-seconds> : [300..3600] – default: 300
hold-time <seconds> [30..86400] - default: no hold-time
initial-hold-time <seconds> [0..900] - default: 300
When the last dynamic host associated with a BRG is deleted, while at the same time connectivity-verification is enabled, the vRGW starts a liveliness test toward the BRG through ICMP (v4 or v6) messages. These messages are sent to either the BRG tunnel source IP address or the BRG RADIUS source IP address. If the BRG has neither of these addresses (for example, because each BRG is managed through a unique VLAN in the implicit authentication scenario), connectivity verification is not executed and only the hold-timer applies. If no answer is returned by the BRG in time (timeout), the vRGW considers the BRG in a failed state, and tries again (retry-time) for some maximum number of times (count).
The vRGW starts the hold-timer when the maximum number of tries is reached, or when connectivity verification is disabled (no connectivity verification). When the hold-timer expires, the BRG context is deleted together with the associated hosts.
The initial-hold-timer is required in the scenario where operators want to use explicit authentication without connectivity-verification, and with no hold-timer defined. In this scenario, defining a non-zero initial-hold-timer value avoids BRG contexts from being deleted immediately after their creation.
If a new dynamic host connects while executing the liveliness test or while the hold-timer or the initial-hold-timer is running, the connectivity verification and BRG deletion process is canceled.
The hold-timer is ignored when manually clearing BRGs and related hosts with the following command.
clear subscriber-mgmt brg gateway
brg-id <brg-ident>
host <ieee-address>
all-hosts
idle-bindings
all-gateways
Configuration
The services configuration shown in Example service configuration for explicit and implicit BRG authentication applies to the examples throughout this chapter. Because the main focus of this chapter is on BRG and home device authentication, the detailed configuration of VPLS 10 containing the capture SAP and of VPRN-2 containing the outside L2-aware NAT range is not repeated here. See the Virtual Residential Gateway Home Pool Management chapter for those configurations.
In summary, VPRN-1 provides the connection toward the customer premises, and hosts the NAT inside addresses. VPRN-2 provides the connection toward the Internet, and hosts the NAT outside addresses. Also, VPRN-3 provides connection to the management interfaces of the BRGs, and is used for the explicit BRG authentication scenario.
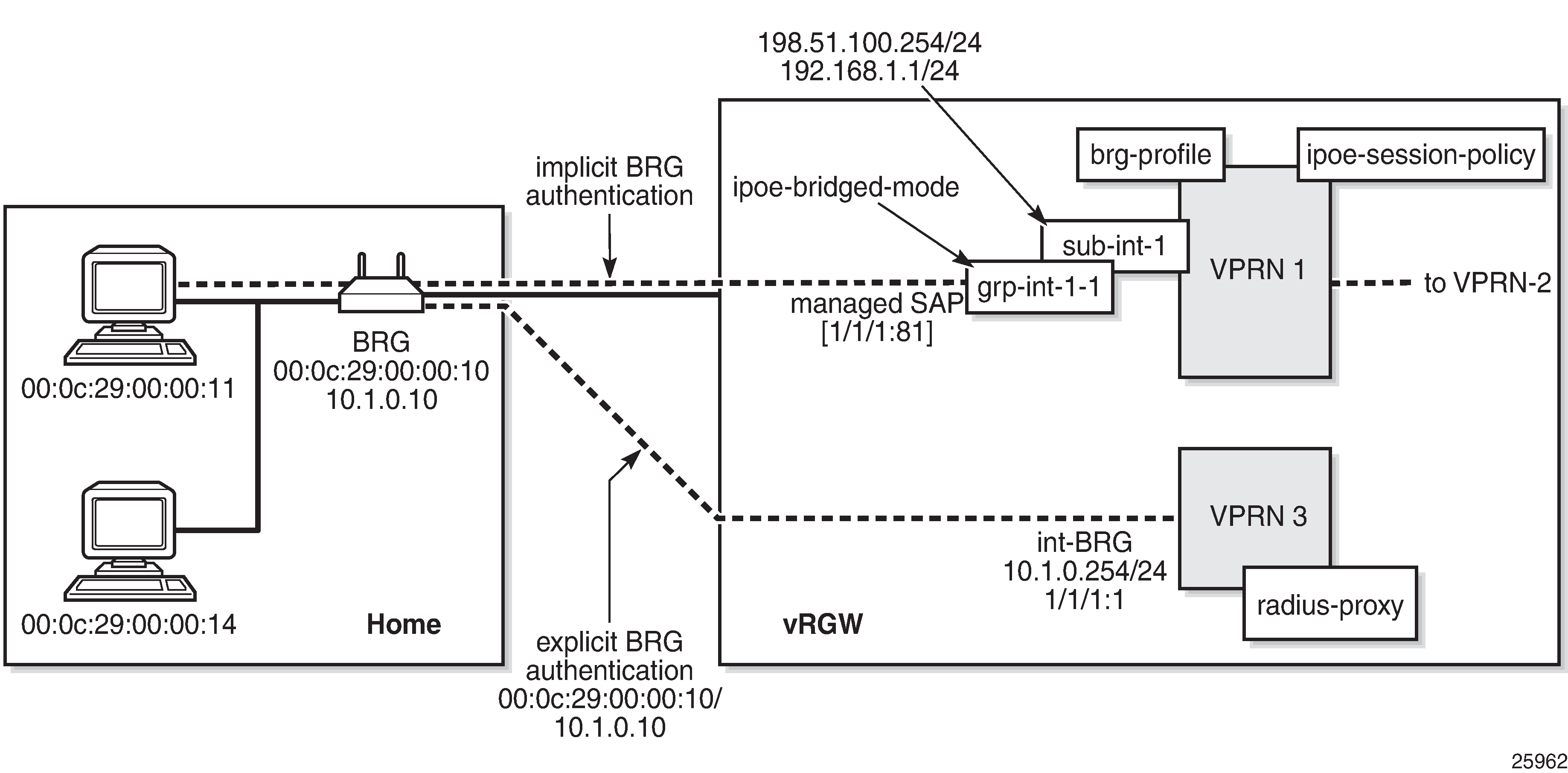
Service configuration
An excerpt of the configuration of VPRN-1 follows. The group interface grp-int-1-1 has RADIUS authentication enabled through authentication policy radius-AUTH, and BRG authentication through the default BRG profile brg-prof-1.
configure
service
vprn 1 customer 1 create
---snip---
subscriber-interface "sub-int-1" create
address 198.51.100.254/24
address 192.168.1.1/24
---snip---
group-interface "grp-int-1-1" create
ipv6
---snip---
ipoe-bridged-mode
exit
---snip---
authentication-policy "radius-AUTH"
ipoe-session
ipoe-session-policy "sess-pol-SAP-MAC"
sap-session-limit 128
no shutdown
exit
brg
default-brg-profile "brg-prof-1"
no shutdown
exit
oper-up-while-empty
exit
exit
nat
inside
l2-aware
address 192.168.0.1/16
exit
exit
exit
no shutdown
exit
exit
exit
BRG profile
The BRG profile brg-prof-1 is defined in the subscriber management context and provides an SLA profile, a subscriber profile, a DHCP pool, a RADIUS server policy plus the corresponding password, and a RADIUS proxy server.
For explicit BRG authentication, the RADIUS proxy server is used; for implicit BRG authentication, the RADIUS server policy and password defined in the RADIUS authentication context are used.
configure
subscriber-mgmt
---snip---
brg-profile "brg-prof-1" create
description "default BRG-profile, demo purposes"
sla-profile-string "sla-prof-1"
sub-profile-string "sub-prof-1"
dhcp-pool
subnet 192.168.1.1/24 start 192.168.1.2 end 192.168.1.254
exit
radius-authentication
password letmein
radius-server-policy "rad-serv-pol-RSP"
exit
radius-proxy-server router 3 name "rad-prox-RPROX"
exit
exit
exit
RADIUS proxy configuration
VPRN-3 is defined for supporting explicit BRG authentication via a RADIUS proxy. The int-BRG interface is on SAP 1/1/1:1, and provides connectivity to the management interface of the physical BRGs. The RADIUS proxy listens on the int-LB-PROXY interface, and directs the incoming RADIUS messages to the server, as defined by the default authentication-server policy.
configure
service
vprn 3
route-distinguisher 64496:3
interface "int-LB-PROXY" create
address 10.33.33.1/32
loopback
exit
interface "int-BRG" create
address 10.1.0.254/24
sap 1/1/1:1 create
exit
exit
radius-proxy
server "rad-prox-RPROX" purpose authentication create
default-authentication-server-policy "rad-serv-pol-RSP"
interface "int-LB-PROXY"
secret vsecret1
no shutdown
exit
exit
no shutdown
exit
exit
exit
RADIUS policies
The RADIUS authentication and accounting policies are defined as follows, so authentication and accounting happens via the base router instance.
configure
router
radius-server
server "radius-172.16.1.2" address 172.16.1.2 secret vsecret1 create
accept-coa
exit
exit
exit
exit
configure
aaa
radius-server-policy "rad-serv-pol-RSP" create
servers
router "Base"
source-address 192.0.2.1
server 1 name "radius-172.16.1.2"
exit
exit
exit
exit
configure
subscriber-mgmt
authentication-policy "radius-AUTH" create
description "RADIUS authentication policy"
password letmein
radius-server-policy "rad-serv-pol-RSP"
exit
radius-accounting-policy "radius-ACCT" create
update-interval 5
include-radius-attribute
mac-address
nat-port-range
subscriber-id
exit
radius-accounting-server
source-address 192.0.2.1
router "Base"
server 1 address 172.16.1.2 secret vsecret1
exit
exit
exit
exit
RADIUS user configuration
Although a PCMP will be used in conjunction with an external controller, for demonstration purposes, this chapter relies on a RADIUS server only.
A sample RADIUS user configuration follows. MAC addresses are used for authentication. MAC address 00:0c:29:00:00:10 identifies the BRG. The addresses ranging from 00:0c:29:00:00:11 to 00:0c:29:00:00:1f identify the home devices connected to that BRG so they all return the same Alc-BRG-Id.
00:0c:29:00:00:10 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
Framed-IPv6-Prefix = 2001:db8:101:1010::/64,
Alc-DMZ-address = 192.168.1.254,
Alc-Home-Aware-Pool =
"192.168.1.1/24 192.168.1.100-192.168.1.254",
Alc-Reserved-Addresses =
"sticky 00:0c:29:00:00:11 192.168.1.110",
Alc-Reserved-Addresses +=
"static 00:0c:29:00:00:1f 192.168.1.254",
Alc-Reserved-Addresses +=
"static 00:0c:29:00:00:1e 198.51.100.110",
Alc-Portal-Url = "http://11.11.11.11",
Alc-Primary-Dns = 1.1.1.1,
Alc-Secondary-Dns = 1.1.2.2,
Alc-Primary-Nbns = 2.2.1.1,
Alc-Secondary-Nbns = 2.2.2.2,
Alc-Ipv6-Primary-DNS = 2001:db8:dddd:1::1,
Alc-Ipv6-Secondary-DNS = 2001:db8:dddd:2::1,
00:0c:29:00:00:11 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
00:0c:29:00:00:12 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
00:0c:29:00:00:13 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
00:0c:29:00:00:14 Cleartext-Password := "letmein"
Alc-BRG-Id = "00:0c:29:00:00:10",
Alc-Primary-Dns = 1.1.3.3,
Debug configuration
The following debug configuration can be used for troubleshooting purposes.
debug
router "Base"
radius
packet-type authentication accounting coa
detail-level high
exit
exit
router "1"
ip
dhcp
detail-level medium
mode egr-ingr-and-dropped
exit
icmp6
exit
exit
router "3"
radius-proxy
server "rad-prox-RPROX"
detail-level high
direction both
packet-type access-request access-accept access-reject
access-challenge accounting-request
accounting-response other
exit
exit
exit
exit
Explicit authentication
In the explicit authentication scenario, the BRG is authenticated before any home device attempts to connect. The following trace shows that the RADIUS proxy server in router 3 receives an Access-Request from BRG with BRG ID 00:0c:29:00:00:10, and passes this to the AAA/RADIUS server, which returns the BRG specific data. Two static addresses and one sticky address are associated with this BRG.
1 2016/09/20 16:27:22.11 CEST MINOR: DEBUG #2001 vprn3 RADIUS
"RADIUS: Receive
Proxy-server rad-prox-RPROX"
2 2016/09/20 16:27:22.11 CEST MINOR: DEBUG #2001 vprn3 RADIUS
"RADIUS: Receive
Access-Request(1) id 18 len 81 from 10.1.0.10:49169 vrid 3 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:10
PASSWORD [2] 16 bD5mfBsZr5M/aFgOa7iAtE
NAS IP ADDRESS [4] 4 10.1.0.10
MESSAGE AUTHENTICATOR [80] 16 0x6c9a951328e303920ba50fa8f7eea0c3
"
3 2016/09/20 16:27:22.11 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 1 len 81 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:10
PASSWORD [2] 16 m9Lo8f7y.V35pw3KzGBs.U
NAS IP ADDRESS [4] 4 10.1.0.10
MESSAGE AUTHENTICATOR [80] 16 0xbe54c468e3e6952f0cedfadd3477683b
Hex Packet Dump:
---snip---
"
4 2016/09/20 16:27:22.11 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 1 len 388 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
FRAMED IPV6 PREFIX [97] 18 2001:db8:101:1010::/64
VSA [26] 6 Alcatel(6527)
BRG DMZ ADDRESS [221] 4 192.168.1.254
VSA [26] 44 Alcatel(6527)
BRG HOME AWARE POOL [220] 42 192.168.1.1/24 192.168.1.100-192.168.1.254
VSA [26] 40 Alcatel(6527)
BRG RESERVED ADDRESS [223] 38 sticky 00:0c:29:00:00:11 192.168.1.110
VSA [26] 40 Alcatel(6527)
BRG RESERVED ADDRESS [223] 38 static 00:0c:29:00:00:1f 192.168.1.254
VSA [26] 41 Alcatel(6527)
BRG RESERVED ADDRESS [223] 39 static 00:0c:29:00:00:1e 198.51.100.110
VSA [26] 20 Alcatel(6527)
PORTAL URL [177] 18 http://11.11.11.11
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 1.1.1.1
VSA [26] 6 Alcatel(6527)
SECONDARY DNS [10] 4 1.1.2.2
VSA [26] 6 Alcatel(6527)
PRIMARY NBNS [29] 4 2.2.1.1
VSA [26] 6 Alcatel(6527)
SECONDARY NBNS [30] 4 2.2.2.2
VSA [26] 18 Alcatel(6527)
IPV6 PRIMARY DNS [105] 16 2001:db8:dddd:1::1
VSA [26] 18 Alcatel(6527)
IPV6 SECONDARY DNS [106] 16 2001:db8:dddd:2::1
Hex Packet Dump:
---snip---
"
5 2016/09/20 16:27:22.12 CEST MINOR: DEBUG #2001 vprn3 RADIUS
"RADIUS: Transmit
Proxy-server rad-prox-RPROX"
6 2016/09/20 16:27:22.12 CEST MINOR: DEBUG #2001 vprn3 RADIUS
"RADIUS: Transmit
Access-Accept(2) 10.1.0.10:49169 id 18 len 388 vrid 3
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
FRAMED IPV6 PREFIX [97] 18 2001:db8:101:1010::/64
VSA [26] 6 Alcatel(6527)
BRG DMZ ADDRESS [221] 4 192.168.1.254
VSA [26] 44 Alcatel(6527)
BRG HOME AWARE POOL [220] 42 192.168.1.1/24 192.168.1.100-192.168.1.254
VSA [26] 40 Alcatel(6527)
BRG RESERVED ADDRESS [223] 38 sticky 00:0c:29:00:00:11 192.168.1.110
VSA [26] 40 Alcatel(6527)
BRG RESERVED ADDRESS [223] 38 static 00:0c:29:00:00:1f 192.168.1.254
VSA [26] 41 Alcatel(6527)
BRG RESERVED ADDRESS [223] 39 static 00:0c:29:00:00:1e 198.51.100.110
VSA [26] 20 Alcatel(6527)
PORTAL URL [177] 18 http://11.11.11.11
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 1.1.1.1
VSA [26] 6 Alcatel(6527)
SECONDARY DNS [10] 4 1.1.2.2
VSA [26] 6 Alcatel(6527)
PRIMARY NBNS [29] 4 2.2.1.1
VSA [26] 6 Alcatel(6527)
SECONDARY NBNS [30] 4 2.2.2.2
VSA [26] 18 Alcatel(6527)
IPV6 PRIMARY DNS [105] 16 2001:db8:dddd:1::1
VSA [26] 18 Alcatel(6527)
IPV6 SECONDARY DNS [106] 16 2001:db8:dddd:2::1
"
As a result, the vRGW creates and stores context for this BRG, which can be displayed using the following command. The Proxy authenticated flag is set to ‟yes”.
*A:BNG# show subscriber-mgmt brg gateways
===============================================================================
Bridged Residential Gateways
===============================================================================
Identifier : 00:0c:29:00:00:10
SLAAC prefix : 2001:db8:101:1010::/64
Subnet : 192.168.1.1/24
Subnet start address : 192.168.1.100
Subnet end address : 192.168.1.254
DMZ address : 192.168.1.254
DNS 1 v4 : 1.1.1.1
DNS 1 v6 : 2001:db8:dddd:1::1
DNS 2 v4 : 1.1.2.2
DNS 2 v6 : 2001:db8:dddd:2::1
NBNS 1 : 2.2.1.1
NBNS 2 : 2.2.2.2
DHCP lease time : 21600
DHCP stream destination : (Not Specified)
IPv4 portal URL : http://11.11.11.11
IPv6 portal URL : (Not Specified)
BRG profile : brg-prof-1
Subscriber profile : sub-prof-1
SLA profile : sla-prof-1
UPnP policy override : (Not Specified)
DMZ address in use : no
Proxy authenticated : yes
Ingress IPv4 filter override : N/A
Egress IPv4 filter override : N/A
Ingress IPv6 filter override : N/A
Egress IPv6 filter override : N/A
No QoS overrides found.
No Filter rules received.
-------------------------------------------------------------------------------
No. of gateways: 1
===============================================================================
*A:BNG#
Initially, no hosts are created and associated with this BRG, as the following command shows.
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" hosts
No entries found.
*A:BNG#
To show the static and sticky addresses associated with the BRG, use the following command. Even without any device connected to this BRG, some bindings are created.
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" bindings
===============================================================================
Bridged Residential Gateway home-aware pool address bindings
===============================================================================
Home-aware pool : 00:0c:29:00:00:10
-------------------------------------------------------------------------------
MAC address : 00:0c:29:00:00:11
IP address : 192.168.1.110
Allocation type : sticky-ip-address
DHCP lease : false
Remaining lease time : (Unknown)
Lease start time : N/A
MAC address : 00:0c:29:00:00:1e
IP address : 198.51.100.110
Allocation type : static
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
MAC address : 00:0c:29:00:00:1f
IP address : 192.168.1.254
Allocation type : static
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
-------------------------------------------------------------------------------
No. of bindings: 3
===============================================================================
*A:BNG#
When the first device connects, in this example using DHCPv4 (DORA), this device is authenticated using RADIUS, and the controller returns the corresponding BRG ID and device-specific primary DNS server (messages 7 and 8). Because the BRG has two static addresses associated with it, at the same time these are also authenticated (messages 12 and 15 for the first static host, 13 and 16 for the second static host). The device with MAC address 00:0c:29:00:00:14 has a dedicated primary DNS server, which overrules the primary DNS server defined at BRG level (messages 8, 10, and 14).
7 2016/09/20 16:29:08.53 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 2 len 79 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:14
PASSWORD [2] 16 Lh/0pV5SVw5Cp7gBJe75s.
NAS IP ADDRESS [4] 4 192.0.2.1
NAS PORT TYPE [61] 4 Ethernet(15)
NAS PORT ID [87] 8 1/1/1:81
Hex Packet Dump:
---snip---
"
8 2016/09/20 16:29:08.53 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 2 len 57 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 1.1.3.3
Hex Packet Dump:
---snip---
"
9 2016/09/20 16:29:08.53 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:81) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Discover
[255] End
"
10 2016/09/20 16:29:08.53 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:81) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.100
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Offer
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 21600
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: length = 8
1.1.3.3
1.1.2.2
[44] NETBIOS name server: length = 8
2.2.1.1
2.2.2.2
[255] End
"
11 2016/09/20 16:29:08.64 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:81) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Request
[50] Requested IP addr: 192.168.1.100
[54] DHCP server addr: 192.168.1.1
[255] End
"
12 2016/09/20 16:29:08.64 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 3 len 79 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:1e
PASSWORD [2] 16 hW.TR6SdCXXMO/3iZ.3WNk
NAS IP ADDRESS [4] 4 192.0.2.1
NAS PORT TYPE [61] 4 Ethernet(15)
NAS PORT ID [87] 8 1/1/1:81
Hex Packet Dump:
---snip---
"
13 2016/09/20 16:29:08.64 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 4 len 79 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:1f
PASSWORD [2] 16 vXTCIxeAZzeGRFAQy8eS/k
NAS IP ADDRESS [4] 4 192.0.2.1
NAS PORT TYPE [61] 4 Ethernet(15)
NAS PORT ID [87] 8 1/1/1:81
Hex Packet Dump:
---snip---
"
14 2016/09/20 16:29:08.64 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:81) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.100
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Ack
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 21600
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: length = 8
1.1.3.3
1.1.2.2
[44] NETBIOS name server: length = 8
2.2.1.1
2.2.2.2
[255] End
"
15 2016/09/20 16:29:08.63 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 3 len 45 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
Hex Packet Dump:
---snip---
"
16 2016/09/20 16:29:08.63 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 4 len 45 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
Hex Packet Dump:
---snip---
"
Displaying the bindings again shows that there is now an additional dynamic host, for which the allocation type is dynamic.
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" bindings
===============================================================================
Bridged Residential Gateway home-aware pool address bindings
===============================================================================
Home-aware pool : 00:0c:29:00:00:10
-------------------------------------------------------------------------------
MAC address : 00:0c:29:00:00:11
IP address : 192.168.1.110
Allocation type : sticky-ip-address
DHCP lease : false
Remaining lease time : (Unknown)
Lease start time : N/A
MAC address : 00:0c:29:00:00:14
IP address : 192.168.1.100
Allocation type : dynamic
DHCP lease : true
Remaining lease time : 21580
Lease start time : 2016/09/20 16:29:08
MAC address : 00:0c:29:00:00:1e
IP address : 198.51.100.110
Allocation type : static
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
MAC address : 00:0c:29:00:00:1f
IP address : 192.168.1.254
Allocation type : static
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
-------------------------------------------------------------------------------
No. of bindings: 4
===============================================================================
*A:BNG#
The following command shows the hosts associated with this BRG. The sticky address is not in the list because the host is not online. For the sticky address to appear, that device must send a DHCPv4 Discover message, initiating its own authentication.
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" hosts
===============================================================================
Bridged Residential Gateway hosts
===============================================================================
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:14
IP address : 192.168.1.100
Service : 1 (VPRN)
Allocation type : dynamic
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : true
Remaining lease time : 21567
Lease start time : 2016/09/20 16:29:08
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1e
IP address : 198.51.100.110
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1f
IP address : 192.168.1.254
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
-------------------------------------------------------------------------------
No. of BRG hosts: 3
===============================================================================
*A:BNG#
Even when the last dynamic host disconnects, the static hosts remain, as shown by the following command.
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" hosts
===============================================================================
Bridged Residential Gateway hosts
===============================================================================
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1e
IP address : 198.51.100.110
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1f
IP address : 192.168.1.254
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
-------------------------------------------------------------------------------
No. of BRG hosts: 2
===============================================================================
*A:BNG#
As long as the BRG is still alive, these hosts will remain, and so will the BRG context. For that reason, the vRGW might start connectivity verification and eventually delete the BRG and its hosts, depending on the configuration.
The BRG context can also be cleared manually using the following command, after which the BRG and the associated hosts are deleted.
*A:BNG# clear subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10"
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" hosts
No entries found.
*A:BNG# show subscriber-mgmt brg gateways
No entries found.
*A:BNG#
Implicit authentication
In the implicit authentication scenario, the BRG is authenticated when the first host is authenticated, which requires two phases. In the first phase, the RADIUS server is accessed for authenticating the device (00:0c:29:00:00:11), returning the device-specific data including the BRG ID. In the second phase, the RADIUS server is accessed for authenticating the BRG (00:0c:29:00:00:10), returning the home-specific data. Because the RADIUS server returns two reserved static addresses, SR OS additionally authenticates the static devices.
18 2016/09/20 16:30:59.88 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 5 len 79 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:11
PASSWORD [2] 16 OhUXqlDfL7XPKlx8EmoMak
NAS IP ADDRESS [4] 4 192.0.2.1
NAS PORT TYPE [61] 4 Ethernet(15)
NAS PORT ID [87] 8 1/1/1:81
Hex Packet Dump:
---snip---
"
19 2016/09/20 16:30:59.89 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 5 len 45 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
Hex Packet Dump:
---snip---
"
20 2016/09/20 16:30:59.89 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 6 len 88 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:10
PASSWORD [2] 16 u87pDAyiQx.TVIGEHFV22U
NAS IP ADDRESS [4] 4 192.0.2.1
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
Hex Packet Dump:
---snip---
"
21 2016/09/20 16:30:59.89 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 6 len 388 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
FRAMED IPV6 PREFIX [97] 18 2001:db8:101:1010::/64
VSA [26] 6 Alcatel(6527)
BRG DMZ ADDRESS [221] 4 192.168.1.254
VSA [26] 44 Alcatel(6527)
BRG HOME AWARE POOL [220] 42 192.168.1.1/24 192.168.1.100-192.168.1.254
VSA [26] 40 Alcatel(6527)
BRG RESERVED ADDRESS [223] 38 sticky 00:0c:29:00:00:11 192.168.1.110
VSA [26] 40 Alcatel(6527)
BRG RESERVED ADDRESS [223] 38 static 00:0c:29:00:00:1f 192.168.1.254
VSA [26] 41 Alcatel(6527)
BRG RESERVED ADDRESS [223] 39 static 00:0c:29:00:00:1e 198.51.100.110
VSA [26] 20 Alcatel(6527)
PORTAL URL [177] 18 http://11.11.11.11
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 1.1.1.1
VSA [26] 6 Alcatel(6527)
SECONDARY DNS [10] 4 1.1.2.2
VSA [26] 6 Alcatel(6527)
PRIMARY NBNS [29] 4 2.2.1.1
VSA [26] 6 Alcatel(6527)
SECONDARY NBNS [30] 4 2.2.2.2
VSA [26] 18 Alcatel(6527)
IPV6 PRIMARY DNS [105] 16 2001:db8:dddd:1::1
VSA [26] 18 Alcatel(6527)
IPV6 SECONDARY DNS [106] 16 2001:db8:dddd:2::1
Hex Packet Dump:
---snip---
"
22 2016/09/20 16:30:59.89 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:81) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:0c:29:00:00:11 xid: 0x1
DHCP options:
[53] Message type: Discover
[255] End
"
23 2016/09/20 16:30:59.89 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:81) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.110
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 00:0c:29:00:00:11 xid: 0x1
DHCP options:
[53] Message type: Offer
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 21600
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: length = 8
1.1.1.1
1.1.2.2
[44] NETBIOS name server: length = 8
2.2.1.1
2.2.2.2
[255] End
"
24 2016/09/20 16:31:00.00 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:81) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:0c:29:00:00:11 xid: 0x1
DHCP options:
[53] Message type: Request
[50] Requested IP addr: 192.168.1.110
[54] DHCP server addr: 192.168.1.1
[255] End
"
25 2016/09/20 16:31:00.00 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:81) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.110
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 00:0c:29:00:00:11 xid: 0x1
DHCP options:
[53] Message type: Ack
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 21600
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: length = 8
1.1.1.1
1.1.2.2
[44] NETBIOS name server: length = 8
2.2.1.1
2.2.2.2
[255] End
"
26 2016/09/20 16:31:00.00 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 7 len 79 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:1e
PASSWORD [2] 16 hz9D.7GnC2H.LSaqMZ4TiE
NAS IP ADDRESS [4] 4 192.0.2.1
NAS PORT TYPE [61] 4 Ethernet(15)
NAS PORT ID [87] 8 1/1/1:81
Hex Packet Dump:
---snip---
"
27 2016/09/20 16:31:00.00 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 8 len 79 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:1f
PASSWORD [2] 16 zIWsyfz7KatfZ42IB4/uY.
NAS IP ADDRESS [4] 4 192.0.2.1
NAS PORT TYPE [61] 4 Ethernet(15)
NAS PORT ID [87] 8 1/1/1:81
Hex Packet Dump:
---snip---
"
28 2016/09/20 16:30:59.99 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 7 len 45 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
Hex Packet Dump:
---snip---
"
29 2016/09/20 16:30:59.99 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 8 len 45 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
Hex Packet Dump:
---snip---
"
Subsequent connections of additional devices connected to the BRG result in one single RADIUS access per device. There is no need to reauthenticate the BRG.
30 2016/09/20 16:32:10.74 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:81) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Discover
[255] End
"
31 2016/09/20 16:32:10.74 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.2:1812 id 9 len 79 vrid 1 pol rad-serv-pol-RSP
USER NAME [1] 17 00:0c:29:00:00:14
PASSWORD [2] 16 TcHWkAooYb5Tcpj9KPR3M.
NAS IP ADDRESS [4] 4 192.0.2.1
NAS PORT TYPE [61] 4 Ethernet(15)
NAS PORT ID [87] 8 1/1/1:81
Hex Packet Dump:
---snip---
"
32 2016/09/20 16:32:10.74 CEST MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 9 len 57 from 172.16.1.2:1812 vrid 1 pol rad-serv-pol-RSP
VSA [26] 19 Alcatel(6527)
BRG ID [225] 17 00:0c:29:00:00:10
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 1.1.3.3
Hex Packet Dump:
---snip---
"
33 2016/09/20 16:32:10.74 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:81) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.100
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Offer
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 21600
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: length = 8
1.1.3.3
1.1.2.2
[44] NETBIOS name server: length = 8
2.2.1.1
2.2.2.2
[255] End
"
34 2016/09/20 16:32:10.84 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:81) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Request
[50] Requested IP addr: 192.168.1.100
[54] DHCP server addr: 192.168.1.1
[255] End
"
35 2016/09/20 16:32:10.84 CEST MINOR: DEBUG #2001 vprn1 PIP
"PIP: DHCP
instance 2 (1), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:81) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 192.168.1.100
siaddr: 192.168.1.1 giaddr: 192.168.1.1
chaddr: 00:0c:29:00:00:14 xid: 0x2
DHCP options:
[53] Message type: Ack
[54] DHCP server addr: 192.168.1.1
[51] Lease time: 21600
[1] Subnet mask: 255.255.255.0
[3] Router: 192.168.1.1
[6] Domain name server: length = 8
1.1.3.3
1.1.2.2
[44] NETBIOS name server: length = 8
2.2.1.1
2.2.2.2
[255] End
"
The following command shows the corresponding BRG hosts.
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" hosts
===============================================================================
Bridged Residential Gateway hosts
===============================================================================
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:11
IP address : 192.168.1.110
Service : 1 (VPRN)
Allocation type : sticky-ip-address
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : true
Remaining lease time : 21514
Lease start time : 2016/09/20 16:31:00
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:14
IP address : 192.168.1.100
Service : 1 (VPRN)
Allocation type : dynamic
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : true
Remaining lease time : 21584
Lease start time : 2016/09/20 16:32:10
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1e
IP address : 198.51.100.110
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
Identifier : 00:0c:29:00:00:10
MAC address : 00:0c:29:00:00:1f
IP address : 192.168.1.254
Service : 1 (VPRN)
Allocation type : static
Home-aware pool : 00:0c:29:00:00:10
DHCP lease : (Unknown)
Remaining lease time : (Unknown)
Lease start time : N/A
-------------------------------------------------------------------------------
No. of BRG hosts: 4
===============================================================================
*A:BNG#
Releasing both dynamic devices results in all BRG hosts being deleted, including the static hosts.
*A:BNG# show subscriber-mgmt brg gateway brg-id "00:0c:29:00:00:10" hosts
No entries found.
*A:BNG#
Also, the BRG is deleted automatically.
*A:BNG# show subscriber-mgmt brg gateways
No entries found.
*A:BNG#
Conclusion
This chapter describes the explicit and the implicit authentication models for the BRG. The explicit authentication model requires the BRG to contain an embedded RADIUS client, and offers better security in comparison with the implicit model, which does not require an embedded RADIUS client.