WiFi Aggregation and Offload — Open SSID with DSM and Lawful Intercept
This chapter provides information about WiFi Aggregation and Offload — Open SSID with DSM and Lawful Intercept.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 12.0.R4.
Overview
WiFi Aggregation and Offload functionality for the 7750 SR has been supported in SR OS 10.0.R1 and later. This includes a RADIUS proxy server with RADIUS proxy cache and support for soft-GRE tunnels.
Initially, WLAN-GW subscribers were implemented using Enhanced Subscriber Management (ESM) on the Control Processing Module (CPM). To achieve higher scalability, subscribers can be implemented using Distributed Subscriber Management (DSM) on the Multi-Service Integrated Service Adapter (MS-ISA) cards, as described in this chapter.
Law enforcement agencies often require operators to provide a method of intercepting traffic from specific User Equipment (UE). This chapter describes a method of configuring Lawful Intercept (LI) for a DSM UE.
Starting with Release 12.0.R4, DSM can be used for higher scalability by instantiating subscribers on the MS-ISA cards, even after authentication, instead of creating them on the CPM as when using ESM. Therefore, the maximum number of UEs per WLAN-GW, and other performance factors such as setup rate, are higher. When using DSM, commands that are different from those used with ESM are used to monitor the UEs. These commands are similar to those used by the previously available migrant users feature, which only instantiated the users on the MS-ISA cards prior to their authentication.
Lawful intercept can also be configured to intercept traffic to and from a UE. For security reasons, the configuration for LI can be kept separate and invisible to the regular admin user of the 7750 SR, even if this admin user has full admin access. In this situation, any information about the intercept is only available to the LI user. An example LI configuration is shown in this document, with the intercept configured using CLI. It is also possible to trigger DSM LI using RADIUS (in Access-Accept or Change of Authorization (CoA) messages). The RADIUS attributes are encrypted so that knowledge of the intercept cannot be gained by examining a packet capture.
Configuration
The WiFi offload scenario with open SSID, DSM and LI shown in WiFi Offload Scenario with Open SSID, DSM and LI has following characteristics:
Open SSID with web portal authentication
DSM with fixed IPv4 address for all UEs, with L2-aware NAT
Access Point (AP) access in Virtual Private Routed Network (VPRN) 1000
UEs terminated in VPRN 2004
Lawful Intercept with separate user account for monitoring or configuring intercepts using the CLI
Figure 1. WiFi Offload Scenario with Open SSID, DSM and LI 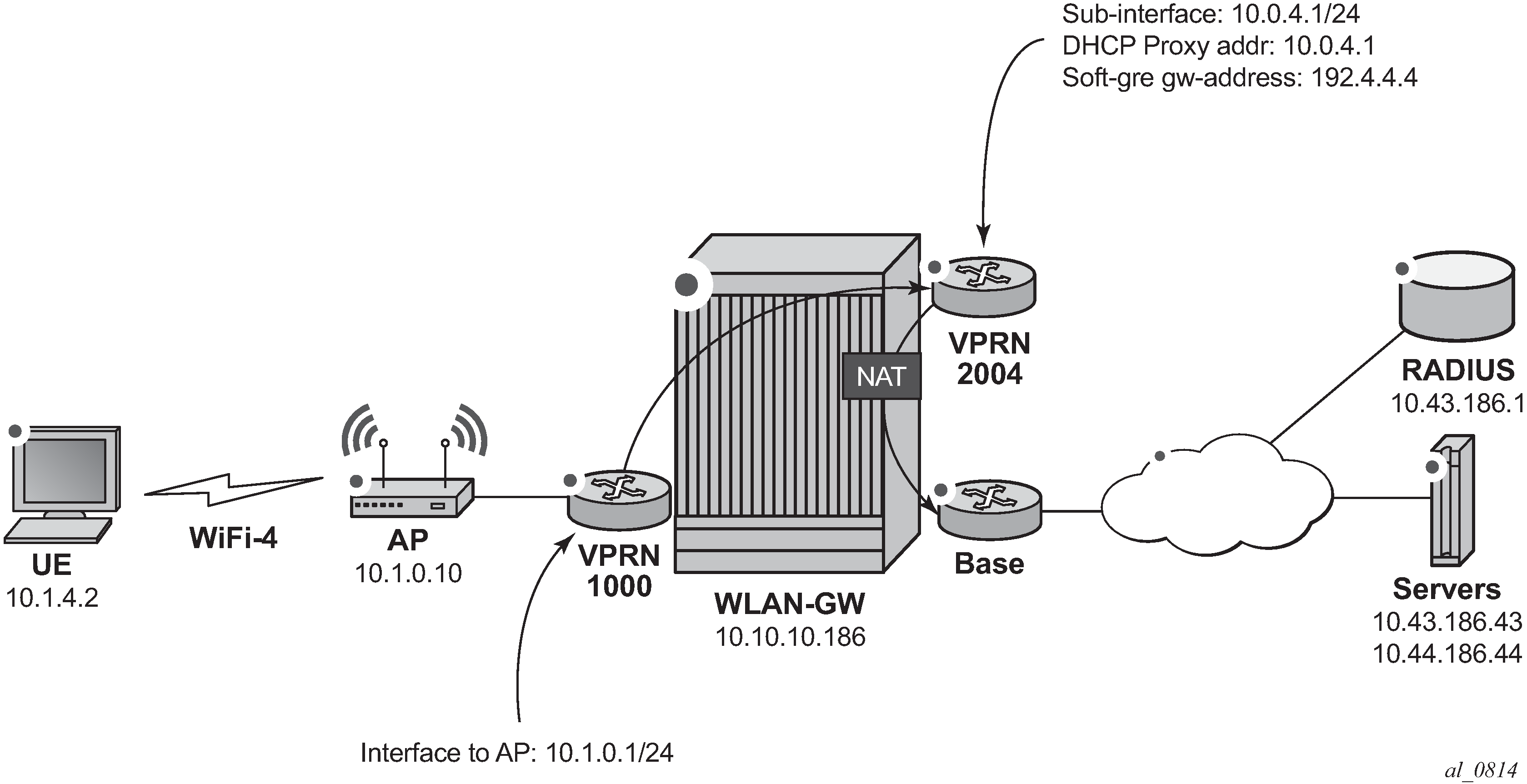
WLAN-GW
Note that the uplink interface, Interior Gateway Protocol (IGP), and system configuration is outside the scope of this document.
The following Card and Media Dependent Adapter (MDA) configuration only shows the WLAN-Input/Output Module (IOM). An IOM card containing two MS-ISA cards provides the WLAN-GW functionality. The MDA type for the ISA cards is isa-bb, the same type that is used for NAT.
*A:WLAN-GW# /configure card 3
*A:WLAN-GW>config>card# info
----------------------------------------------
card-type iom3-xp
mda 1
mda-type isa-bb
no shutdown
exit
mda 2
mda-type isa-bb
no shutdown
exit
no shutdown
----------------------------------------------
The following ISA configuration applies.
*A:WLAN-GW# /configure isa
*A:WLAN-GW>config>isa# info
----------------------------------------------
wlan-gw-group 1 create
active-iom-limit 1
iom 3
no shutdown
exit
----------------------------------------------
The following NAT configuration provides an outside pool of type wlan-gw-anchor required to support DSM.
*A:WLAN-GW# /configure router nat
*A:WLAN-GW>config>router>nat# info
----------------------------------------------
outside
pool "WiFi-4-dsm" nat-group 1 type wlan-gw-anchor create
port-reservation ports 15
address-range 10.0.40.0 10.0.40.255 create
exit
no shutdown
exit
exit
----------------------------------------------
*A:WLAN-GW# /configure service nat
*A:WLAN-GW>config>service>nat# info
----------------------------------------------
nat-policy "WiFi-4-dsm" create
pool "WiFi-4-dsm" router Base
exit
----------------------------------------------
The following Authentication, Authorization and Accounting (AAA) configuration contains an isa-radius-policy. The nas-ip-address-origin parameter selects the IP address sent as the Network Access Server (NAS) IP Address attribute in the ISA RADIUS requests. The source-address-range configures the IP address used by the first MS-ISA card on this WLAN-GW to send and receive RADIUS messages. Other WLAN IOM MS-ISA cards will get consecutive IP addresses in order of slot number. The password and secret configured here have to match the RADIUS server configuration.
*A:WLAN-GW# /configure aaa
*A:WLAN-GW>config>aaa# info
----------------------------------------------
isa-radius-policy "IRS_4" create
nas-ip-address-origin isa-ip
password "7USmr6f7JkxD5zb3MeEZnjf1BSqaZkcH" hash2
servers
access-algorithm round-robin
router "Base"
source-address-range 10.10.186.1
server 1 create
authentication
coa
ip-address 10.43.186.1
secret "7USmr6f7JkxD5zb3MeEZnjf1BSqaZkcH" hash2
no shutdown
exit
exit
exit
----------------------------------------------
The following subscriber management configuration contains the http-redirect-policy for redirecting newly connected UEs to the web portal, and allowing only traffic to the web portal IP address and the Domain Name Server (DNS) server.
*A:WLAN-GW# /configure subscriber-mgmt
*A:WLAN-GW>config>subscr-mgmt# info
----------------------------------------------
http-redirect-policy "WiFi-4-dsm-redirect" create
url "http://portal1.3ls.net/portal4.php?mac=$MAC"
forward-entries
dst-ip 10.43.186.1 protocol tcp dst-port 80 prefix-length 32
dst-ip 10.43.186.43 protocol udp dst-port 53 prefix-length 32
exit
exit
----------------------------------------------
The following policy configuration is used for exporting required routes, including the address of the APs, the outside NAT prefixes, and the ISA RADIUS source IP addresses.
*A:WLAN-GW# /configure router policy-options
*A:WLAN-GW>config>router>policy-options# info
----------------------------------------------
prefix-list "WiFi"
prefix 10.0.0.0/16 longer
prefix 10.10.186.0/24 longer
exit
prefix-list "WiFi-APs"
prefix 10.1.0.0/16 longer
exit
policy-statement "toisis"
entry 10
from
prefix-list "WiFi" "WiFi-APs"
exit
action accept
exit
exit
exit
policy-statement "WiFi-APs"
entry 10
from
prefix-list "WiFi-APs"
exit
action accept
exit
exit
exit
----------------------------------------------
The following configuration is used for exporting the outside NAT prefixes and the ISA RADIUS source IP addresses to ISIS.
*A:WLAN-GW# /configure router isis
*A:WLAN-GW>config>router>isis# info
----------------------------------------------
export "toisis"
----------------------------------------------
The following configures VPRN 1000 for AP connectivity, where the AP prefix is exported to the Global Route Table (GRT) so that it can be managed from servers reachable through the Base router.
*A:WLAN-GW# /configure service vprn 1000
*A:WLAN-GW>config>service>vprn# info
----------------------------------------------
route-distinguisher 65400:1000
interface "toAP" create
address 10.1.0.1/24
sap 1/1/7 create
exit
exit
grt-lookup
enable-grt
static-route 0.0.0.0/0 grt
exit
export-grt "WiFi-APs"
exit
----------------------------------------------
The following configures VPRN 2004 for UE termination, with distributed-sub-mgmt enabled and the ISA RADIUS policy configured under vlan-tag-ranges.
*A:WLAN-GW# /configure service vprn 2004
*A:WLAN-GW>config>service>vprn# info
----------------------------------------------
description "Open WiFi with DSM"
route-distinguisher 65400:2004
subscriber-interface "SI4" create
address 10.0.4.1/24
group-interface "GI4" wlangw create
wlan-gw
gw-address 192.4.4.4
mobility
trigger data iapp
exit
router 1000
wlan-gw-group 1
vlan-tag-ranges
range default
authentication
authentication-policy "IRS_4"
exit
dhcp
active-lease-time min 5
initial-lease-time min 5
l2-aware-ip-address 10.1.4.2
primary-dns 10.43.186.43
secondary-dns 10.44.186.44
no shutdown
exit
distributed-sub-mgmt
no shutdown
exit
nat-policy "WiFi-4-dsm"
exit
exit
no shutdown
exit
exit
exit
nat
inside
l2-aware
address 10.1.4.1/24
exit
exit
exit
wlan-gw
exit
no shutdown
----------------------------------------------
The following LI user configuration allows user LIadmin to configure and view the Lawful Intercept configuration.
*A:WLAN-GW# /configure system security
*A:WLAN-GW>config>system>security# info
----------------------------------------------
profile "li"
default-action deny-all
li
entry 1
match "back"
action permit
exit
entry 2
exit
entry 10
match "configure system security"
action permit
exit
entry 20
match "configure li"
action permit
exit
entry 30
match "show li"
action permit
exit
entry 40
match "file"
action permit
exit
entry 50
match "info"
action permit
exit
entry 60
match "admin display-config"
action permit
exit
entry 70
match "tools perform security"
action permit
exit
entry 80
match "tools dump li wlan-gw ue"
action permit
exit
entry 100
match "exit"
action permit
exit
exit
user "LIadmin"
password "$2y$10$Yp3sQZpGlbg6K3CeQoCHi.wyBOj7ts5/tsY/nqb0bbFjuFZ9G5wsi"
access console li
console
no member "default"
member "li"
exit
exit
----------------------------------------------
The following mirror configuration of type ip-only forwards intercepted traffic to a server.
*A:WLAN-GW# /configure mirror
*A:WLAN-GW>config>mirror# info
----------------------------------------------
mirror-dest 199 type ip-only create
encap
layer-3-encap ip-udp-shim create
gateway create
ip src 10.10.10.186 dest 10.43.186.43
udp src 3199 dest 3199
exit
exit
exit
no shutdown
exit
----------------------------------------------
The following configures a BOF, with li-local-save, a local LI config file, and li-separate, ensuring that only the LI user can view or modify LI parameters.
*A:WLAN-GW# show bof
===============================================================================
BOF (Memory)
===============================================================================
li-local-save
li-separate
The following LI source configuration to intercept the UE can only be configured or viewed by user LIadmin. The configuration is saved in cf3:\li.cfg, encrypted. The intercept-id and session-id will appear in the LI packets, which can be decoded in Wireshark using Decode As, Jmirror.
*A:WLAN-GW# /configure li
*A:WLAN-GW>config>li# info
----------------------------------------------
#--------------------------------------------------
echo "LI Log Configuration"
#--------------------------------------------------
log
exit
#--------------------------------------------------
echo "LI Filter Lock State Configuration"
#--------------------------------------------------
li-filter-lock-state locked
#--------------------------------------------------
echo "LI Mirror Source Configuration"
#--------------------------------------------------
li-source 199
wlan-gw
dsm-subscriber mac 68:7f:74:8b:3d:d7
intercept-id 1
session-id 199
exit
exit
no shutdown
exit
----------------------------------------------
Freeradius
This default configuration section sets the VSA Alc-Wlan-Ue-Creation-Type with value 1, which triggers the creation of a DSM host (value 0 is ESM). The Nas-Ip-Address is returned in the Alc-Wlan-Portal-URL to tell the web portal which MS-ISA address should receive the RADIUS CoA request:
/etc/freeradius/users:
DEFAULT Auth-Type := Local, User-Password := "alcatel", user-name=~"^.*$"
Alc-Subsc-ID-Str = "%{User-Name}",
Alc-Wlan-Ue-Creation-Type = 1,
Alc-Wlan-Portal-Redirect = "WiFi-4-dsm-redirect",
Alc-Wlan-Portal-URL = "http://portal1.3ls.net/portal4.php?nas=%{Nas-Ip-Address}&mac=%{User-Name}&ssid=WiFi-4",
As an alternative to configuring the LI for the UE in the CLI, the following RADIUS attributes can be sent in the Access-Accept and CoA.
Alc-LI-Action = "enable",
Alc-LI-Destination = "199",
Alc-LI-Intercept-Id = 1,
In /etc/freeradius/clients.conf, each ISA is a client.
client 10.10.186.1 {
secret = alcatel
shortname = WLAN-GW-ISA1
}
client 10.10.186.2 {
secret = alcatel
shortname = WLAN-GW-ISA2
}
A RADIUS CoA sent during a successful portal login makes the following UE a DSM subscriber with full access.
echo "User-Name='.$mac.',Alc-Wlan-Ue-Creation-Type="1",Alc-Subsc-Prof-Str="SUBP_4",Alc-SLA-Prof-Str=SLAP_4,Alc-Primary-Dns = 10.43.186.43," | /usr/bin/radclient -x -r 1 -t 2 '.$nas.' coa alcatel
Access Points
The following must be configured on the Access Point as a minimum:
IP address 10.1.1.10/24
Default route to 10.1.1.1
Open SSID WiFi-4 mapped to VLAN 40
Soft-GRE tunnel with destination 192.4.4.4, with VLAN 40 mapped to this tunnel
Show Commands
The following commands show the status of the UEs. For DSM users, the UEs are displayed using a tools command. Before portal authentication, the UE is in Portal state.
*A:WLAN-GW# /tools dump wlan-gw ue
===============================================================================
Matched 1 session on Slot #3 MDA #1
===============================================================================
UE-Mac : 68:7f:74:8b:3d:d7 UE-vlan : 40
UE IP Addr : 10.1.4.2 UE timeout : 293 sec
Description : Portal
Auth-time : 09/08/2014 11:30:34
Tunnel MDA : 3/2 Tunnel Router : 1000
MPLS label : 40 Shaper : Default
Tunnel Src IP : 10.1.0.10 Tunnel Dst IP : 192.4.4.4
Tunnel Type : GRE
Anchor SAP : 3/1/nat-out-ip:2049.3
AP-Mac : Unknown AP-RSSI : Unknown
AP-SSID : Unknown
Last-forward : 09/08/2014 11:30:39 Last-move : None
Session Timeout : None Idle Timeout : N/A
Acct Update : None Acct Interval : N/A
Acct Session-Id : N/A
Acct Policy : N/A
NAT Policy : WiFi-4-dsm
Redirect Policy : WiFi-4-dsm-redirect
IP Filter : N/A
App-profile : N/A
Rx Oper PIR : N/A Rx Oper CIR : N/A
Tx Oper PIR : N/A Tx Oper CIR : N/A
Rx Frames : 204 Rx Octets : 17381
Tx Frames : 78 Tx Octets : 67793
-------------------------------------------------------------------------------
===============================================================================
No sessions on Slot #3 MDA #2 match the query
After login to the web portal, the UE transitions to a DSM-user and the Redirect Policy is removed,
*A:WLAN-GW# /tools dump wlan-gw ue
===============================================================================
Matched 1 session on Slot #3 MDA #1
===============================================================================
UE-Mac : 68:7f:74:8b:3d:d7 UE-vlan : 40
UE IP Addr : 10.1.4.2 UE timeout : 284 sec
Description : DSM-user
Auth-time : 09/08/2014 11:30:45
Tunnel MDA : 3/2 Tunnel Router : 1000
MPLS label : 40 Shaper : Default
Tunnel Src IP : 10.1.0.10 Tunnel Dst IP : 192.4.4.4
Tunnel Type : GRE
Anchor SAP : 3/1/nat-out-ip:2049.3
AP-Mac : Unknown AP-RSSI : Unknown
AP-SSID : Unknown
Last-forward : 09/08/2014 11:30:47 Last-move : None
Session Timeout : None Idle Timeout : N/A
Acct Update : None Acct Interval : N/A
Acct Session-Id : N/A
Acct Policy : N/A
NAT Policy : WiFi-4-dsm
Redirect Policy : N/A
IP Filter : N/A
App-profile : N/A
Rx Oper PIR : N/A Rx Oper CIR : N/A
Tx Oper PIR : N/A Tx Oper CIR : N/A
Rx Frames : 273 Rx Octets : 23186
Tx Frames : 122 Tx Octets : 108083
-------------------------------------------------------------------------------
===============================================================================
No sessions on Slot #3 MDA #2 match the query
User LIadmin can view the configured intercept,
*A:WLAN-GW>config>li# /tools dump li wlan-gw ue
===============================================================================
Matched 1 session on Slot #3 MDA #1
===============================================================================
UE-Mac : 68:7f:74:8b:3d:d7 Mirror Service : 199
LI Intercept-Id : 1 LI Session-Id : 199
-------------------------------------------------------------------------------
===============================================================================
No sessions on Slot #3 MDA #2 match the query
Debug
In this example, the following debug configuration applies.
debug
mirror-source 99
port 1/1/7 egress ingress
port 1/1/9 egress ingress
no shutdown
exit
wlan-gw
group 1
ue 68:7f:74:8b:3d:d7 packet dhcp radius
exit
exit
exit
The debug trace starts with DHCP.
150 2014/09/08 11:30:31.93 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 3/1, SeqNo 3528
Info: anchor ingressing frame
received upstream from tunnel
Ethernet: from 68:7f:74:8b:3d:d7 to ff:ff:ff:ff:ff:ff (ethertype: 0x0800)
IP/UDP: from 0.0.0.0 (port 68) to 255.255.255.255 (port 67)
DHCP:
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0xca073331
DHCP options:
[53] Message type: Discover
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[12] Host name: W81VM
[60] Class id: MSFT 5.0
[55] Param request list: len = 13
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
252 Unknown option
43 Vendor specific
[255] End
"
151 2014/09/08 11:30:31.93 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 3/2, SeqNo 706
Info: tunnel ingressing frame
received downstream from anchor
Ethernet: from 00:00:00:02:02:02 to 68:7f:74:8b:3d:d7 (ethertype: 0x0800)
IP/UDP: from 10.1.4.1 (port 67) to 10.1.4.2 (port 68)
DHCP:
ciaddr: 0.0.0.0 yiaddr: 10.1.4.2
siaddr: 10.1.4.1 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0xca073331
DHCP options:
[53] Message type: Offer
[54] DHCP server addr: 10.1.4.1
[1] Subnet mask: 255.255.255.0
[3] Router: 10.1.4.1
[51] Lease time: 300
[6] Domain name server: length = 8
10.43.186.43
10.44.186.44
[255] End
"
152 2014/09/08 11:30:32.09 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 3/1, SeqNo 3529
Info: anchor ingressing frame
received upstream from tunnel
Ethernet: from 68:7f:74:8b:3d:d7 to ff:ff:ff:ff:ff:ff (ethertype: 0x0800)
IP/UDP: from 0.0.0.0 (port 68) to 255.255.255.255 (port 67)
DHCP:
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0xca073331
DHCP options:
[53] Message type: Request
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[50] Requested IP addr: 10.1.4.2
[54] DHCP server addr: 10.1.4.1
[12] Host name: W81VM
[81] client FQDN: rcode1: 0, rcode2: 0, domain name = (hex) 00 57 38 31 56
4d
[60] Class id: MSFT 5.0
[55] Param request list: len = 13
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
252 Unknown option
43 Vendor specific
[255] End
"
153 2014/09/08 11:30:32.09 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 3/2, SeqNo 707
Info: tunnel ingressing frame
received downstream from anchor
Ethernet: from 00:00:00:02:02:02 to 68:7f:74:8b:3d:d7 (ethertype: 0x0800)
IP/UDP: from 10.1.4.1 (port 67) to 10.1.4.2 (port 68)
DHCP:
ciaddr: 0.0.0.0 yiaddr: 10.1.4.2
siaddr: 10.1.4.1 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0xca073331
DHCP options:
[53] Message type: Ack
[54] DHCP server addr: 10.1.4.1
[1] Subnet mask: 255.255.255.0
[3] Router: 10.1.4.1
[51] Lease time: 300
[58] Renew timeout: 150
[59] Rebind timeout: 263
[6] Domain name server: length = 8
10.43.186.43
10.44.186.44
[255] End
"
RADIUS authentication is triggered by the first data packet.
154 2014/09/08 11:30:34.76 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 3/1, SeqNo 3563
Info: anchor egressing frame
radius-auth-req
IP/UDP: from 10.10.186.1 (port 1082) to 10.43.186.1 (port 1812)
RADIUS: Access-Request (continued)
"
155 2014/09/08 11:30:34.76 EDT MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 10.10.186.1:1082 id 45 len 126 vrid 1
NAS IP ADDRESS [4] 4 10.10.186.1
USER NAME [1] 17 68:7f:74:8b:3d:d7
PASSWORD [2] 16 MvqAtmAOvSeeWgNIGyT/t.
CALLING STATION ID [31] 17 68:7f:74:8b:3d:d7
CALLED STATION ID [30] 17 00:00:00:00:00:00
VSA [26] 19 Alcatel(6527)
CHADDR [27] 17 68:7f:74:8b:3d:d7
"
156 2014/09/08 11:30:34.76 EDT MINOR: DEBUG #2001 Base WLAN-GW
"WLAN-GW: MDA 3/1, SeqNo 3564
Info: anchor ingressing frame
portal auth-accept
IP/UDP: from 10.43.186.1 (port 1812) to 10.10.186.1 (port 1082)
RADIUS: Access-Accept (continued)
"
157 2014/09/08 11:30:34.76 EDT MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 45 len 258 from 10.43.186.1:1812 vrid 1
VSA [26] 19 Alcatel(6527)
SUBSC ID STR [11] 17 68:7f:74:8b:3d:d7
VSA [26] 20 Alcatel(6527)
VSA [26] 20 Alcatel(6527)
VSA [26] 20 Alcatel(6527)
VSA [26] 6 Alcatel(6527)
WLAN UE CREATION TYPE [184] 4 1
VSA [26] 25 Alcatel(6527)
WLAN PORTAL REDIRECT [172] 23 WiFi-4-dsm-redirect
VSA [26] 86 Alcatel(6527)
WLAN PORTAL URL [173] 84 http://portal1.3ls.net/portal4.php?nas=10.10.186.
1&mac=68:7f:74:8b:3d:d7&ssid=WiFi-4
"
RADIUS returns the redirect policy and portal URL, and the UE is then in Portal state. Next, the user logs in and a CoA is sent by the portal.
159 2014/09/08 11:30:45.07 EDT MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Change of Authorization(43) id 220 len 91 from 10.43.186.1:53449 vrid 1
USER NAME [1] 17 68:7f:74:8b:3d:d7
VSA [26] 6 Alcatel(6527)
WLAN UE CREATION TYPE [184] 4 1
VSA [26] 8 Alcatel(6527)
SUBSC PROF STR [12] 6 SUBP_4
VSA [26] 8 Alcatel(6527)
SLA PROF STR [13] 6 SLAP_4
VSA [26] 6 Alcatel(6527)
PRIMARY DNS [9] 4 10.43.186.43
"
Finally the UE is in DSM state with unrestricted access.
Conclusion
The 7750 SR WLAN-GW, with Open SSID, can support WiFi Offload users as DSM subscribers instantiated on MS-ISA cards. This allows the support of a greater number of UEs on a single system when a full ESM feature set is not required. DSM UEs, just as ESM UEs, can have their traffic intercepted using LI.