IPoE Sessions
This chapter describes IPoE Sessions.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 13.0.R7.
IPoE sessions require a Routed CO environment with Enhanced Subscriber Management (ESM) enabled.
Overview
Definitions
Grouping a number of subscriber hosts with different IP stacks belonging to the same end user device in a single IPoE session simplifies operations; see IPoE Session.
In this way, IPoE sessions provide behavior similar to PPPoE sessions for authentication, mid-session changes, and accounting.
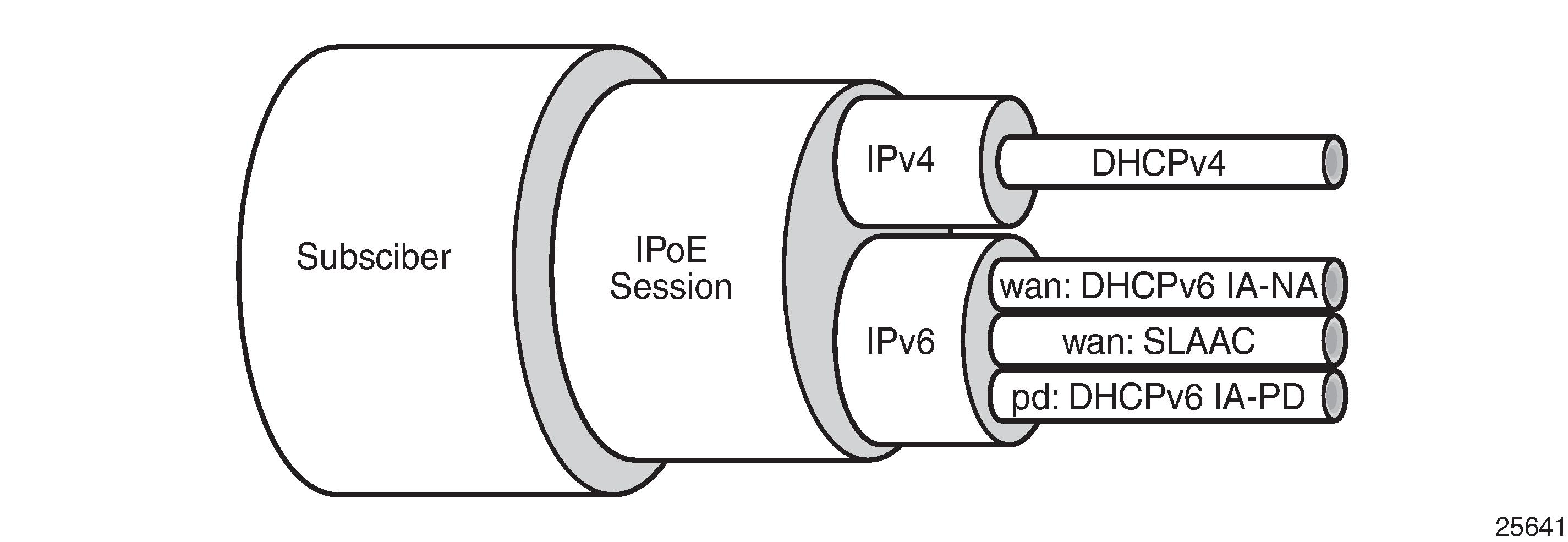
The hosts (IP stacks) associated with a single IPoE session share ESM data, such as the subscriber ID, the sub-profile, the SLA profile, and so on. The shared ESM data is fetched and cached when the first host for that session connects: only a single authentication is needed. This requires ESM to be enabled; see the ESM basics chapter for more information.
An IPoE session can have one IPoEv4 host, up to two IPoEv6 wan hosts (one DHCPv6 host and a SLAAC host), and one IPoEv6 pd host. Hosts with the same SAP, MAC address, and optionally the same circuit ID (CID) or remote ID (RID), are grouped in a single IPoE session, using that combination as a key to the IPoE session data.
Authentication occurs when the first host for that IPoE session is created. Subsequent hosts belonging to the same IPoE session do not require additional authentication. For instantiating these subsequent hosts, SR OS uses the cached ESM data that was fetched while authenticating and instantiating the first host.
Mid-session changes are typically triggered by RADIUS CoA or Diameter Gx RAR messages, and automatically apply to all hosts associated with the IPoE session. A re-authentication could also lead to policy changes, but the changes are triggered through host renewal messages.
As well as queue instance and host accounting, RADIUS session accounting can be enabled for IPoE sessions. An accounting session identity (ASID) is created when an IPoE session is started.
An IPoE session is created when the first host is created, and the IPoE session is deleted when the last host is deleted. IPoE session creation is always protocol triggered. IPoE session deletion is triggered through protocol (DHCPv4, DHCPv6 release, or expiration of a lease) or through policy (idle-timeout, session-timeout, clear command, and so on).
IPoE sessions require the Routed CO model, and are supported on regular as well as on capture and managed SAPs.
Trigger Packets
Unlike PPP, where PPP sessions have clear and unique triggers that start (PADS) and stop (PADT) a PPP session, IPoE does not have unique triggers that start and stop an IPoE session.
IPoE sessions are created when the following trigger packets on ESM-enabled SAPs are received:
DHCPv4 discover/request
DHCPv6 solicit/request (native)
DHCPv6 solicit/request (single relay)
DHCPv6 solicit/request (double relay)
Router Solicitation
No IPoE sessions are created on reception of ARP requests or CoA messages.
IPoE Session Key
The key to the IPoE session data is a combination of the SAP ID, the MAC address, and optionally the CID or the RID, as defined by the ipoe-session-policy:
configure
subscriber-mgmt
ipoe-session-policy <pol-name>
session-key sap mac [cid] [rid]
The ipoe-session-policy name default is reserved for future use.
The CID and RID are mutually exclusive; see IPoE Session Key:
The CID corresponds to DHCPv4 option 82, sub-option 1 (Circuit-ID) and to DHCPv6 option 18 (Interface-ID).
The RID corresponds to DHCPv4 option 82, sub-option 2 (Remote-ID) and to DHCPv6 option 37 (the remote-id field of the Relay Agent Remote-ID, excluding the enterprise-number field).
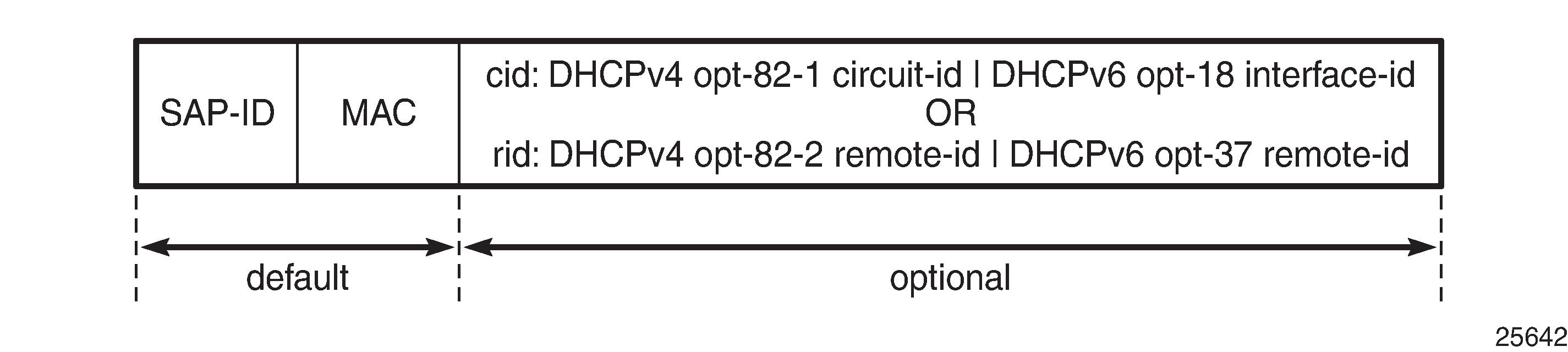
When an IPoE session trigger packet is received, the IPoE session key is validated, ensuring that no field is missing. For example, if the key requires the CID or RID, and a device connects without CID or RID, the IPoE session setup and the host setup fail. Therefore, the CID or RID should only be part of the key when all devices include this parameter in the trigger packets.
If no IPoE session exists for a session key derived from a trigger packet, an IPoE session is created. If an IPoE session exists, a new host is created and added to the existing IPoE session, on condition that the host type is compatible with the already associated host types.
IPoE Session Authentication
Authenticating IPoE sessions requires generic identification parameters, which must be supported in both IPv4 and IPv6, so some restrictions apply.
LUDB Authentication
When using an LUDB for IPoE session authentication, all of the host-identification criteria can be used, except for the following:
Option 60 - DHCPv4 only
LUDB entries containing option 60 are ignored while scanning the LUDB for a matching entry.
AAA/RADIUS Authentication
When using AAA/RADIUS for IPoE session authentication, all username formats can be used, except for the following:
dhcp-client-vendor-opts - DHCPv4 only
mac-giaddr - DHCPv4 only
ppp-user-name - PPP only
IPoE Session Creation
To ensure successful creation of an IPoE session, the following conditions must be met:
the IPoE session key must be valid
the session limits should not be exceeded
an Accounting Session Identity (ASID) must be allocated
the first ESM host must be successfully authenticated
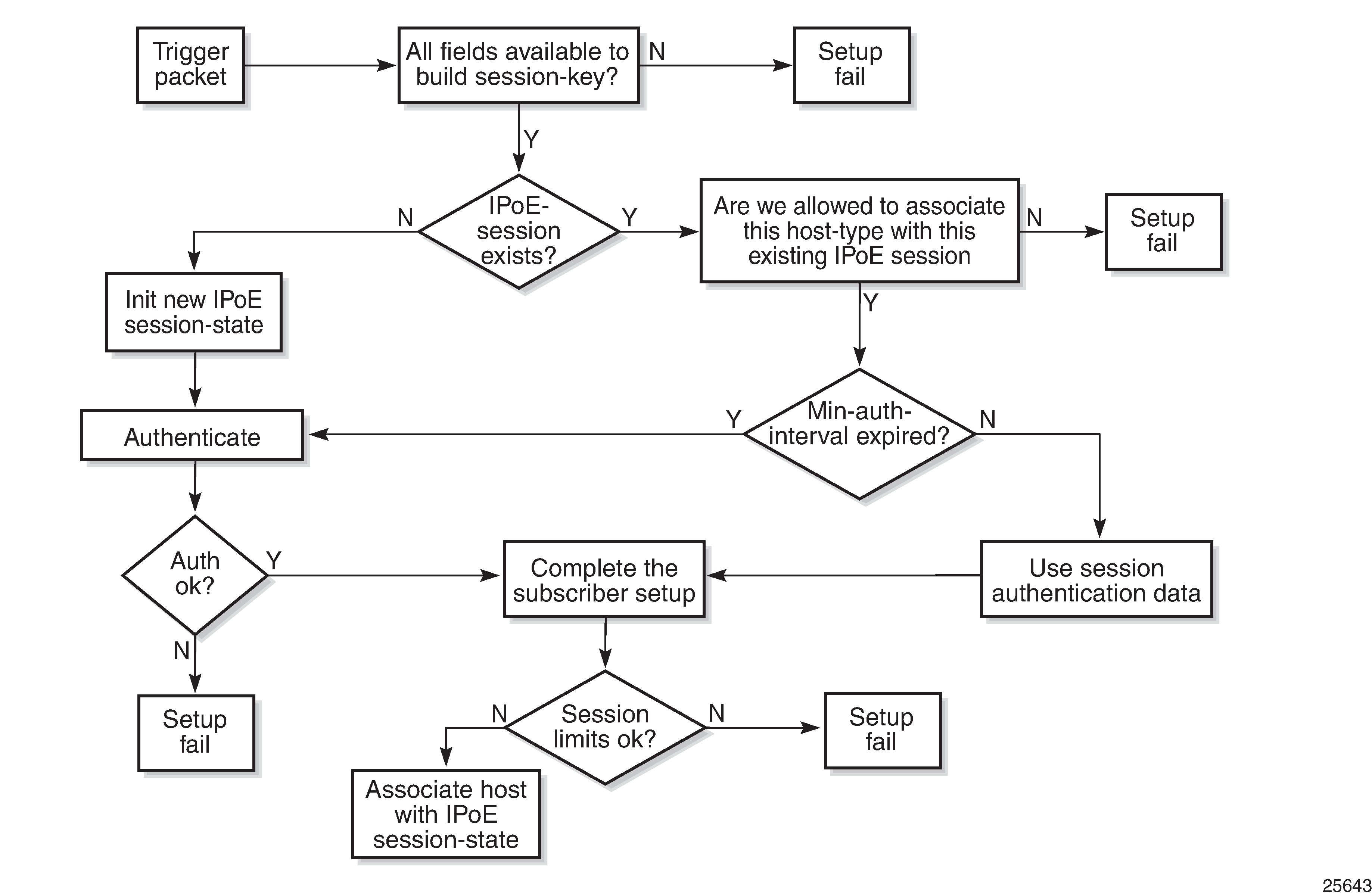
IPoE Session Creation Flow shows the high-level flow of the IPoE session creation process. When a new trigger is received for an existing IPoE session, a new host is created and added to the session, on condition that the new host is compatible with the already associated hosts.
IPoE Session Creation via AAA/RADIUS shows an example where a device initiates DHCPv6 first. The data fetched while authenticating this device through AAA/RADIUS is cached. When the same device (leading to the same key) later initiates DHCPv4, the cached IPoE session data can be used, so no further AAA/RADIUS access is needed. The sequence could also first initiate DHCPv4, then DHCPv6. The result would be the same.
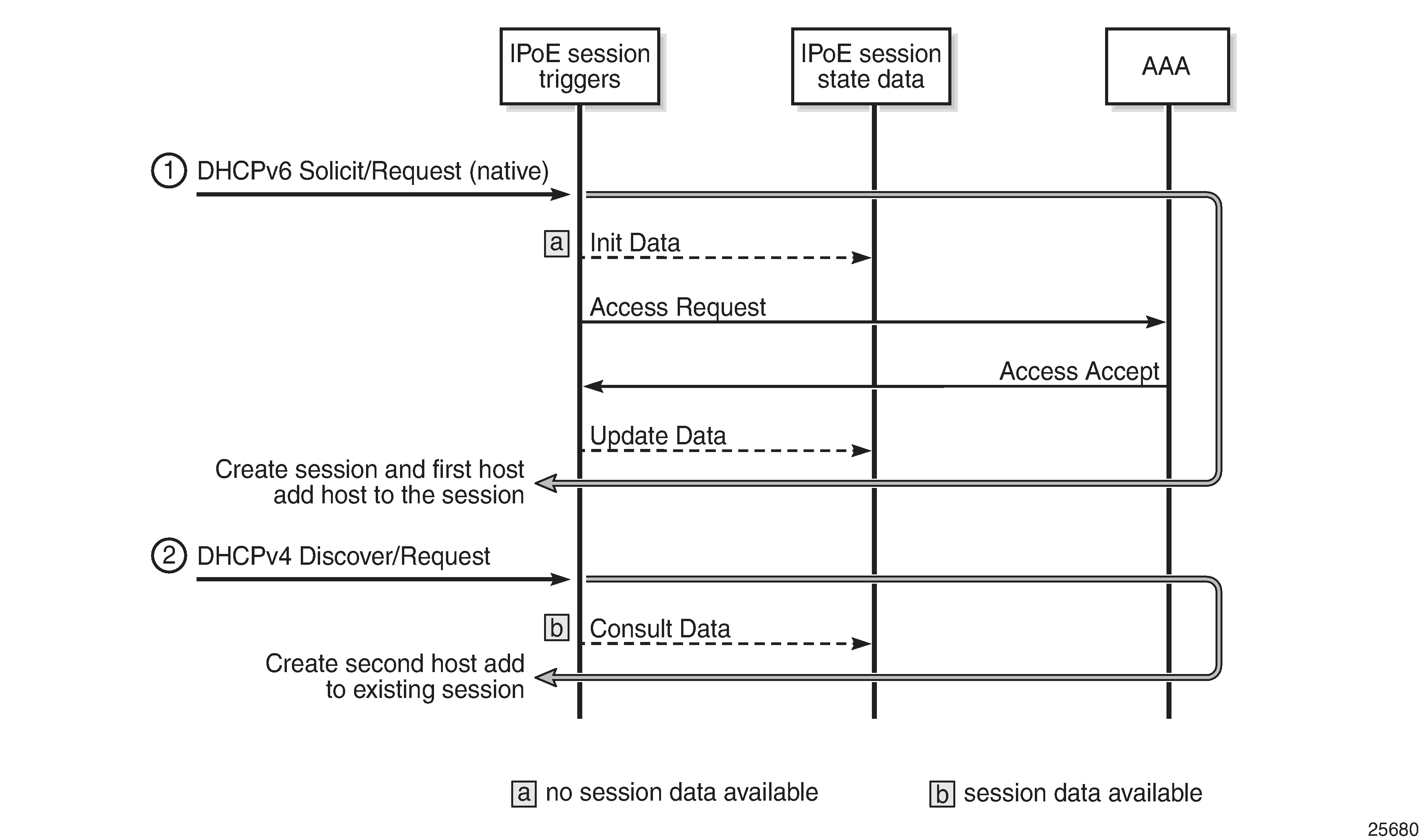
An Access-Request message is sent to the AAA/RADIUS server for authentication. On successful authentication, the AAA/RADIUS returns the ESM data (subscriber ID, sub-profile, SLA profile, and so on) in an Access-Accept message.
The Access-Request message optionally includes the host ID or ASID.
The behavior when authenticating through LUDB is similar.
IPoE Session Re-Authentication
IPoE sessions can be re-authenticated, meaning that the ESM data is fetched again from the ESM data source (LUDB, RADIUS, and so on), and controlled through the min-auth-interval timer.
If a host renewal packet is received while the min-auth-interval timer is running for the corresponding IPoE session, the cached ESM data is used (with one exception: see forced authentication). If a host renewal packet is received when this timer has expired, re-authentication is performed. If re-authentication fails, the host renewal packet is dropped; see IPoE Session Creation Flow.
IPoE session re-authentication is configured in the ipoe-session context using following command:
min-auth-interval ?
- min-auth-interval [days <days>] [hrs <hours>] [min <minutes>] [sec <seconds>]
- min-auth-interval infinite
- no min-auth-interval
<days> : [0..365]
<hours> : [0..23]
<minutes> : [0..59]
<seconds> : [0..59]
<infinite> : keyword
By default, re-authentication is disabled by having the min-auth-interval set to infinite. Setting the min-auth-interval to zero will lead to every single message (DORA, SARR) triggering re-authentication, but that is not recommended.
IPoE session re-authentication can be used to implement dynamic policy changes. For alternatives also implementing dynamic changes, see the Mid-Session Changes section.
For IPoE sessions, the re-authentication option in the RADIUS authentication-policy context is ignored.
IPoE Session Forced Authentication
Forced authentication means that the ESM data is fetched again from the ESM data source, regardless of the value of the re-authentication timer.
By default, forced authentication occurs when the CID or RID in the trigger packet has changed value, but this behavior can be disabled.
An absent or empty CID or RID is not considered as a change.
Forced authentication is configured in the ipoe-session context using following command:
force-auth ?
- force-auth [cid-change] [rid-change]
- force-auth disabled
- no force-auth
<cid-change> : keyword - ignore min-auth-interval when cid changed
<rid_change> : keyword - ignore min-auth-interval when rid changed
<disabled> : keyword - never ignore min-auth-interval
IPoE Session Deletion
When the last host associated with an IPoE session is deleted, the IPoE session is deleted.
IPoE sessions are forcibly deleted in following situations:
group-interface ipoe-session shutdown
clear service <id> ipoe-session
session timeout
RADIUS disconnect or Diameter Gx RAR
Credit Control (out-of-credit)
In all these cases, all hosts belonging to that session are deleted, with one exception. When the SLAAC inactivity-timer expires, only the corresponding SLAAC host is deleted, not the remaining hosts. When this SLAAC host is the last host of the IPoE session, the IPoE session is deleted.
The IPoE session-timeout is configured in the ipoe-session-policy:
configure
subscriber-mgmt
ipoe-session-policy <pol-name>
session-timeout <timeout>
The timeout value ranges from 1 to 31104000 seconds (360 days). By default, no session-timeout is specified.
When RADIUS or Diameter Gx returns the Session-Timeout [27] or the Alc-Relative-Session-Timeout [26-6527-160] attributes, these values are used and the behavior is the same as for PPP sessions.
When no Session-Timeout or Alc-Relative-Session-Timeout attribute is returned by RADIUS, the session-timeout as configured in the ipoe-session-policy is used.
A RADIUS disconnect message, even when targeted at a single host, will also lead to the deletion of the entire IPoE session including all associated hosts.
A shutdown in the ipoe-session context of the group interface results in the deletion of all its IPoE sessions and associated hosts.
Session and Host limits
The number of IPoE sessions on a group interface and on a SAP can be limited:
configure service ies|vprn <service-id>
subscriber-interface <ip-int-name>
group-interface <ip-int-name>
ipoe-session
session-limit [1..max*]
sap-session-limit [1..max*]
The default values for the session-limit and the sap-session-limit are unlimited (no session-limit) and 1, respectively.
For retail services, the IPoE session-limit is configured at the linked subscriber interface level:
configure service vprn <retail-service-id>
subscriber-interface <RT-ip-int-name> fwd-service <WS-service-id>
fwd-subscriber-interface <WS-ip-int-name>
session-limit [1..max*]
The default session-limit is unlimited.
Additionally, host limits can be imposed through the SLA profile:
configure subscriber-mgmt
sla-profile <subscriber-profile-name>
host-limits
ipv4-arp - Maximum number of IPv4 ARP hosts
ipv4-dhcp - Maximum number of IPv4 DHCP hosts
ipv4-overall - Maximum number of IPv4 hosts
ipv4-ppp - Maximum number of IPv4 PPP hosts
ipv6-overall - Maximum number of IPv6 hosts
ipv6-pd-ipoe-dhcp - Maximum number of IPv6-PD IPOE DHCP hosts
ipv6-pd-overall - Maximum number of IPv6-PD hosts
ipv6-pd-ppp-dhcp - Maximum number of IPv6-PD PPP DHCP hosts
ipv6-wan-ipoe-dhcp - Maximum number of IPv6-Wan IPOE DHCP hosts
ipv6-wan-ipoe-slaac - Maximum number of IPv6-Wan IPOE SLAAC hosts
ipv6-wan-overall - Maximum number of IPv6-Wan hosts
ipv6-wan-ppp-dhcp - Maximum number of IPv6-Wan PPP DHCP hosts
ipv6-wan-ppp-slaac - Maximum number of IPv6-Wan PPP SLAAC hosts
lac-overall - Maximum number of L2TP LAC hosts
overall - Maximum number of hosts
remove-oldest - Remove oldest
exit
See the Wholesale/Retail section for more information about limits in a wholesale/retail configuration.
RADIUS Session Accounting
As well as queue instance and host accounting, RADIUS session accounting can be enabled for IPoE sessions.
Usually, a RADIUS Accounting-Start message is sent when the first host is associated with an IPoE session. Regular and triggered accounting Interim-Update messages are sent during the IPoE session. An Accounting-Stop message is sent when the last host is deleted from the session.
Session accounting is configured in the RADIUS accounting policy, and can be set to the following values:
session-accounting
session-accounting interim-update
session-accounting host-update
session-accounting interim-update host-update
Plain session accounting sends start and stop messages. The RADIUS accounting server is informed about the start and the stop time of the session, but no counters are maintained. This implements time-based accounting.
The interim-update option additionally sends interim-update messages, so that the RADIUS accounting server maintains counters. This implements volume accounting.
The host-update option additionally sends host up/down event messages, so that the RADIUS accounting server keeps track of host creation and deletion events.
The combination of the interim-update and host-update options allows the RADIUS accounting server to track all changes.
Mid-Session Changes
Mid-session changes, such as those initiated via RADIUS CoA or Diameter Gx RAR messages, are applied to all hosts associated with the IPoE session. There is no way to update a single host of an IPoE session.
A RADIUS CoA message targeting any host of an IPoE session has the same effect as a RADIUS CoA message targeting the IPoE session using the IPoE session Acct-Session-Id as key. All hosts of the session are targeted and the session state data is updated.
Mid-session changes also can be applied manually, using the following command:
# tools perform subscriber-mgmt edit-ipoe-session sap <sap-id> mac <mac-address> [subscriber <sub-ident-string>] [sub-profile-string <sub-profile-string>] [sla-profile-string <sla-profile-string>] [inter-dest-id <intermediate-destination-id>] [ancp-string <ancp-string>] [app-profile-string <app-profile-string>] [circuit-id <circuit-id>] [remote-id <remote-id>]
# tools perform subscriber-mgmt eval-ipoe-session [svc-id <service-id>] [sap <sap-id>] [mac <mac-address>] [circuit-id <circuit-id>] [remote-id <remote-id>] [subscriber <sub-ident-string>]
The tools commands eval-lease-state and eval-slaac-host are blocked when the host is part of a session.
IPoE session re-authentication can also lead to dynamic policy changes.
Subscriber Host Connectivity Verification
Subscriber host connectivity verification (SHCV) can be enabled for hosts associated with an IPoE session.
When a single host fails and stops responding to the SHCV messages, that host is deleted without affecting the other hosts that are part of the session. When the last host fails, the session is deleted.
IA-PD managed routes are not subject to SHCV, and cannot be removed because of SHCV.
Dual Homing
IPoE sessions are supported in a dual-homed environment, where Multichassis Synchronization (MCS) and Subscriber Routed Redundancy Protocol (SRRP) are active.
MCS ensures that the IPoE session data is synchronized between the BNG pair.
Wholesale/Retail
IPoE sessions are supported in single-homed and dual-homed wholesale/retail environments.
The wholesale IPoE session limit is configured at the group interface level, and the retail IPoE session limit is configured at the linked subscriber interface level:
configure service vprn <retail-service-id>
subscriber-interface <RT-ip-int-name> fwd-service <WS-service-id>
fwd-subscriber-interface <WS-ip-int-name>
ipoe-session
session-limit [1..max*] #default unlimited
In IPoE, private-retail-subnets only apply to IPoEv6 in single-homed scenarios (no MCS). Therefore, the use cases for private-retail-subnets in combination with IPoE sessions are limited.
Practical Considerations
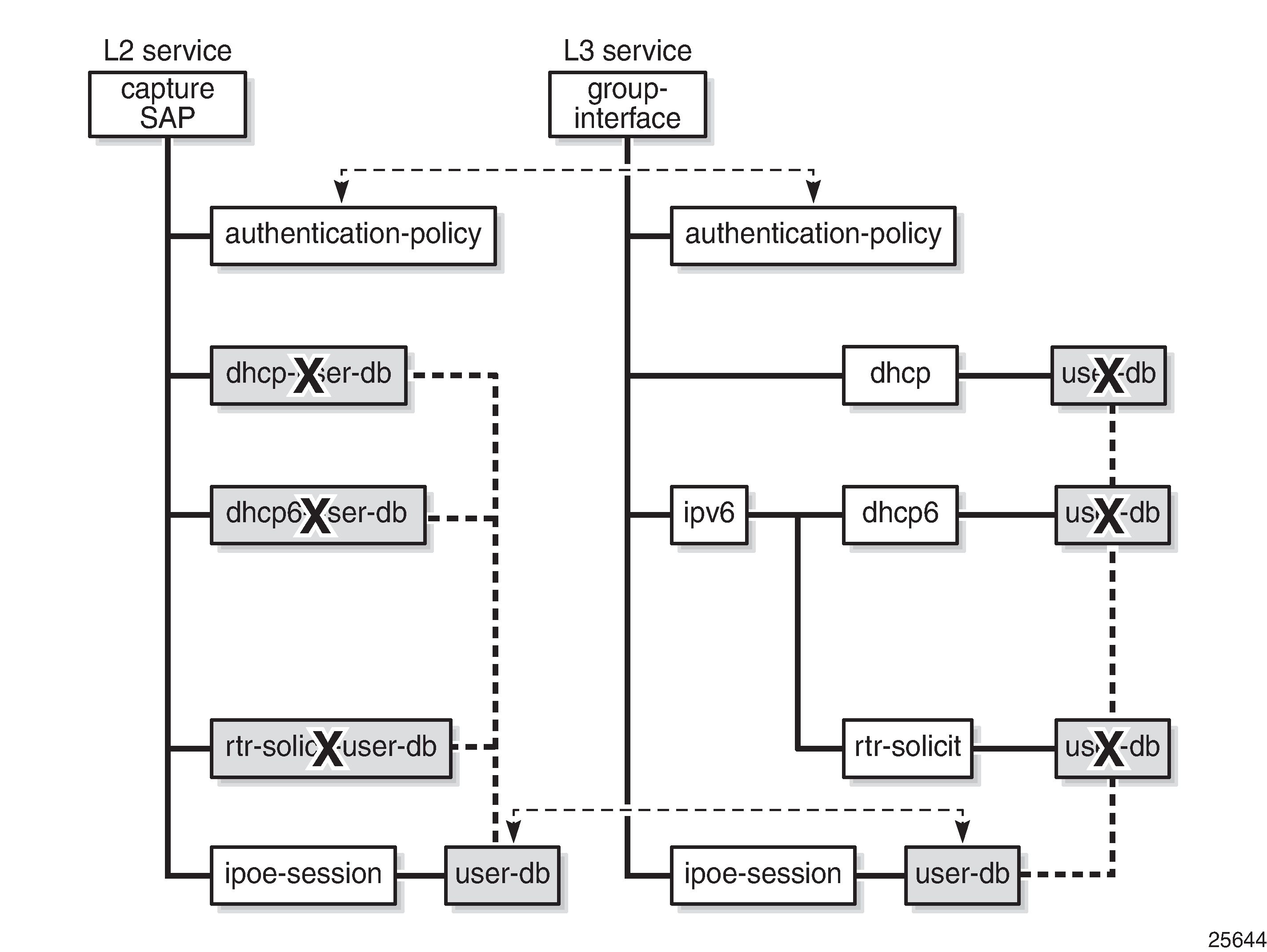
The rules for configuring authentication for regular, capture, and managed SAPs, also apply to IPoE sessions; see Configuring IPoE session authentication:
If an authentication policy is applied at capture-SAP or group-interface level, this policy has priority, regardless of whether, or in which other sub-contexts, an LUDB is assigned. Therefore, for an LUDB to provide ESM data, no authentication policy may be applied at capture-SAP or group interface level.
If an LUDB is applied in the ipoe-session context of a group interface or capture SAP, the LUDBs assigned in the dhcp, dhcp6, and router-solicit related contexts of the same group interface or capture SAP are ignored.
When the AAA/RADIUS server referenced from the authentication policy is not available, SR OS can rely on a fallback LUDB, if configured; see the LUDB for ESM chapter for more information.
Be aware of the following:
Static hosts can be configured on a group interface with IPoE sessions enabled. A static host will not be associated with an IPoE session.
ARP hosts are not supported in an IPoE session and cannot be instantiated on a group interface with IPoE sessions enabled.
Up to sixteen framed-routes and sixteen framed-IPv6-routes can be associated with an IPoE session.
Python-based subscriber identification based on the DHCPv4 Ack message is ignored when IPoE sessions are enabled.
Configuration
Baseline configuration
Baseline configuration shows the baseline configuration used for the examples in this chapter, excluding the ipoe-session configurations. These will be added later in this chapter.
The first example uses LUDB authentication, and the second example uses AAA/RADIUS authentication. As alternatives, AAA/NASREQ authentication or AAA/Gx authentication can be used.
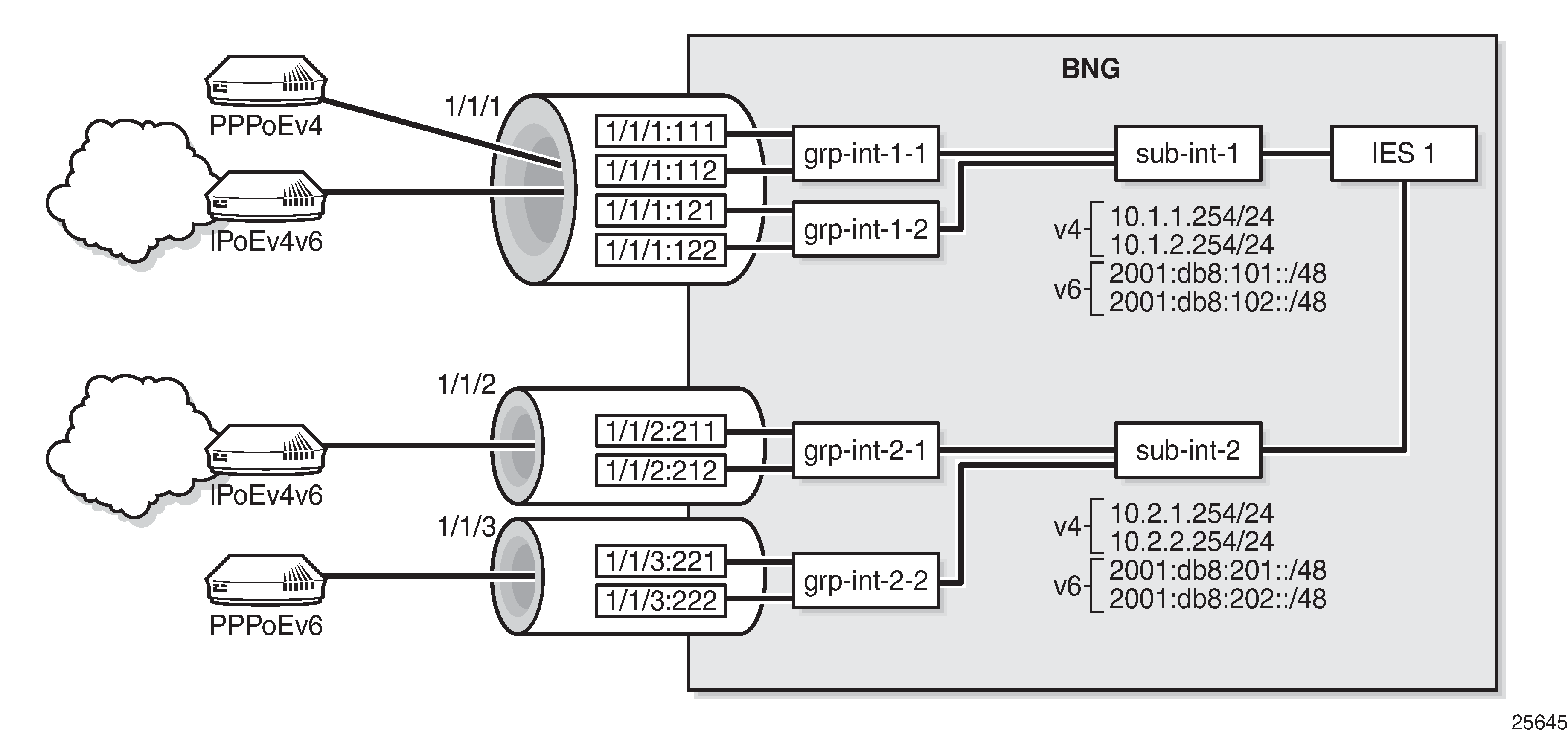
The following partial configuration applies to IES-1. This service is provisioned with ESM on all of its SAPs, and supports proxy and relay scenarios on all group interfaces for both IPv4 and IPv6. Only the part relevant to subscriber interface sub-int-1 and group interface grp-int-1-1 is shown. The configurations for the other subscriber and group interfaces are similar. See the ESM Basics and Routed CO chapters for more information.
configure
service
ies 1 customer 1 create
subscriber-interface "sub-int-1" create
address 10.1.1.254/24
---snip---
ipv6
delegated-prefix-len 56
link-local-address fe80::ea:4b:ff
subscriber-prefixes
prefix 2001:db8:101::/48 wan-host
prefix 2001:db8:f101::/48 pd
---snip---
exit
exit
group-interface grp-int-1-1
ipv6
router-advertisements
prefix-options
autonomous
exit
no shutdown
exit
dhcp6
proxy-server
client-applications dhcp ppp
no shutdown
exit
relay
link-address 2001:db8:101::1
server 2001:db8::11
client-applications dhcp ppp
no shutdown
exit
exit
router-solicit
no shutdown
exit
exit
local-address-assignment
ipv6
client-application ipoe-slaac
server "dhcp6-srv"
exit
no shutdown
exit
arp-populate
dhcp
proxy-server
emulated-server 10.1.1.254
no shutdown
exit
server 10.11.11.1
trusted
lease-populate 1000
client-applications dhcp ppp
gi-address 10.1.1.254
no shutdown
exit
---snip---
sap 1/1/1:111 create
sub-sla-mgmt
def-sub-profile "sub-prof-1"
def-sla-profile "sla-prof-1"
sub-ident-policy "sub-id-pol-1"
multi-sub-sap
no shutdown
exit
exit
---snip---
No DHCPv4 or DHCPv6 relay options are defined.
Troubleshooting
The syntax to show the active IPoE sessions is as follows:
show service id <service-id> ipoe session ?
- session [sap <sap-id>] [mac <ieee-address>] [circuit-id <circuit-id>] [remote-id <remote-id>] [interface <ip-int-name|ip-address>] [inter-dest-id <intermediate-destination-id>] [no-inter-dest-id] [ip-address <ip-prefix[/prefix-length]>] [port <port-id>] [subscriber <sub-ident-string>] [sap-session-id <sap-session-index>] [wholesaler <service-id>]
- session [sap <sap-id>] [mac <ieee-address>] [circuit-id <circuit-id>] [remote-id <remote-id>] [interface <ip-int-name|ip-address>] [inter-dest-id <intermediate-destination-id>] [no-inter-dest-id] [ip-address <ip-prefix[/prefix-length]>] [port <port-id>] [subscriber <sub-ident-string>] [sap-session-id <sap-session-index>] detail [wholesaler <service-id>]
The following show commands have been extended, so that session filtering is available:
show service id <svc-id> dhcp lease-state ?
- lease-state [wholesaler <service-id>] [sap <sap-id>|sdp <sdp-id:vc-id>|interface <interface-name>|ip-address <ip-address[/mask]>|chaddr <ieee-address>|mac <ieee-address>|{[port <port-id>] [no-inter-dest-id | inter-dest-id <inter-dest-id>]}] [session {none|ipoe}] [detail]
show service id <svc-id> dhcp6 lease-state ?
- lease-state [detail] [wholesaler <service-id>] [session {none|ipoe|ppp}]
- lease-state [detail] interface <interface-name> [wholesaler <service-id>] [session {none|ipoe|ppp}]
- lease-state [detail] ipv6-address <ipv6-prefix[/prefix-length]> [wholesaler <service-id>] [session {none|ipoe|ppp}]
- lease-state [detail] mac <ieee-address> [wholesaler <service-id>] [session {none|ipoe|ppp}]
show service id <svc-id> slaac host ?
- host [detail] [wholesaler <service-id>] [session {none|ipoe|ppp}]
- host interface <interface-name> [detail] [wholesaler <service-id>] [session {none|ipoe|ppp}]
- host mac <ieee-address> [detail] [wholesaler <service-id>] [session {none|ipoe|ppp}]
- host ipv6-address <ipv6-prefix> [detail] [wholesaler <service-id>] [session {none|ipoe|ppp}]
- host sap <sap-id> [detail] [wholesaler <service-id>] [session {none|ipoe|ppp}]
The following debug configuration is used for demonstration and troubleshooting purposes:
debug
router "Base"
ip
dhcp
detail-level medium
mode egr-ingr-and-dropped
exit
dhcp6
mode egr-ingr-and-dropped
detail-level medium
exit
exit
radius
packet-type authentication accounting coa
detail-level medium
exit
exit
subscriber-mgmt
local-user-db "ludb-1"
detail all
exit
exit
exit
IPoE session failure events are also issued to log-id 99:
*A:BNG-1# show log event-control "svcmgr"
=======================================================================
Log Events
=======================================================================
Application
ID# Event Name P g/s Logged Dropped
-----------------------------------------------------------------------
2011 svcTlsMacPinningViolation WA thr 0 0
---snip---
2554 tmnxSubIpoeInvalidSessionKey WA thr 30 0
2555 tmnxSubIpoeInvalidCidRidChange WA thr 0 0
2556 tmnxSubIpoeSessionLimitReached WA thr 0 0
2557 tmnxSubIpoePersistenceRecovery WA thr 0 0
2559 tmnxSubIpoeMigrHostDeleted WA thr 0 0
=======================================================================
*A:BNG-1#
IPoE Session Authentication through LUDB
The LUDB ludb-1 uses the MAC address for host matching, and is defined as follows:
configure
subscriber-mgmt
local-user-db "ludb-1" create
description "example user-db"
ipoe
match-list mac
host "entry-01" create
host-identification
mac 00:00:00:00:00:01
exit
address pool "pool4-1"
identification-strings 254 create
subscriber-id "sub-11"
sla-profile-string "sla-profile-1"
sub-profile-string "sub-profile-1"
exit
ipv6-slaac-prefix-pool "pool6-1"
ipv6-wan-address-pool "pool6-1"
no shutdown
exit
---snip---
This LUDB is then applied to the group interface in the ipoe-session context:
configure
service
ies 1 customer 1 create
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
ipoe-session
description "ipoe-sessions with LUDB"
ipoe-session-policy "sespol-sap-mac"
sap-session-limit 100
session-limit 500
user-db "ludb-1"
no shutdown
exit
The LUDB applied in the ipoe-session context takes priority over LUDBs applied in the dhcp router-solicit, ipv6 dhcpv6 router-solicit, and ipv6 router-solicit contexts for a Layer 3 service.
The IPoE session policy sespol-sap-mac used in this example is defined as follows:
configure
subscriber-mgmt
ipoe-session-policy "sespol-sap-mac" create
description "plain ipoe session policy, sap-mac key"
session-key sap mac
no session-timeout
exit
Debug
The following debug trace appears when the user with MAC address 00:00:00:00:00:01 first connects using DHCPv4 and subsequently connects using SLAAC and DHCPv6 (IANA), without disconnecting DHCPv4.
Messages 1 through 9 show the message sequence for DHCPv4 (DORA). Messages 11 through 22 show the message sequence for DHCPv6 (SARR). Message 10 and 23 are the router solicitation and advertisement messages. Therefore, three hosts are created.
The LUDB is accessed just once; immediately after the DHCPv4 Discover message:
1 2016/02/03 13:51:28.15 CET MINOR: DEBUG #2001 Base PIP
"PIP: DHCP
instance 1 (Base), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:111) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:00:00:00:00:01 xid: 0x1
DHCP options:
[53] Message type: Discover
[255] End
"
2 2016/02/03 13:51:28.15 CET MINOR: DEBUG #2001 Base LUDB
"LUDB: User lookup success - host found
mac: 00:00:00:00:00:01
Host entry-01 found in user data base ludb-1"
3 2016/02/03 13:51:28.15 CET MINOR: DEBUG #2001 Base PIP
"PIP: DHCP
instance 1 (Base),
transmitted DHCP Boot Request to 10.11.11.1 Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 10.1.1.254
chaddr: 00:00:00:00:00:01 xid: 0x1
DHCP options:
[53] Message type: Discover
[255] End
"
---snip---
9 2016/02/03 13:51:28.16 CET MINOR: DEBUG #2001 Base PIP
"PIP: DHCP
instance 1 (Base), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:111) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 10.1.1.60
siaddr: 10.11.11.1 giaddr: 10.1.1.254
chaddr: 00:00:00:00:00:01 xid: 0x1
DHCP options:
[53] Message type: Ack
[54] DHCP server addr: 10.11.11.1
[51] Lease time: 900
[1] Subnet mask: 255.255.255.0
[3] Router: 10.1.1.254
[255] End
"
10 2016/02/03 13:51:40.77 CET MINOR: DEBUG #2001 Base TIP
"TIP: ICMP6_PKT
ICMP6 ingressing on grp-int-1-1 (Base):
fe80::200:ff:fe00:1 -> ff02::2
Type: Router Solicitation (133)
Code: No Code (0)
Option : Src Link Layer Addr 00:00:00:00:00:01
"
11 2016/02/03 13:51:40.78 CET MINOR: DEBUG #2001 Base TIP
"TIP: DHCP6_PKT
Incoming DHCP6 Msg : SOLICIT (1)
on itf grp-int-1-1
Trans Id : 0x411fc8
Option : CLIENTID (1), Length : 14
LLT : HwTyp=0001,T=507311564,LL=000000000001
000100011e3cf5cc000000000001
Option : IA_NA (3), Length : 12
IAID : 2
Time1: 0 seconds
Time2: 0 seconds
Option : ORO (6), Length : 2
Requested Option : DNS_NAME_SRVR (23)
"
---snip---
22 2016/02/03 13:51:40.92 CET MINOR: DEBUG #2001 Base TIP
"TIP: DHCP6_PKT
Outgoing DHCP6 Msg : REPLY (7)
to itf grp-int-1-1
Trans Id : 0xe15ddf
Option : SERVERID (2), Length : 10
LL : HwTyp=0001,LL=ea4bff000000
00030001ea4bff000000
Option : CLIENTID (1), Length : 14
LLT : HwTyp=0001,T=507311564,LL=000000000001
000100011e3cf5cc000000000001
Option : IA_NA (3), Length : 40
IAID : 2
Time1: 1800 seconds
Time2: 2880 seconds
Option : IAADDR (5), Length : 24
Address : 2001:db8:101:c::1
Preferred Lifetime : 3600 seconds
Valid Lifetime : 86400 seconds
Option : DNS_NAME_SRVR (23), Length : 16
Server : 2001:db8::1:1:1:1
"
23 2016/02/03 13:51:41.91 CET MINOR: DEBUG #2001 Base TIP
"TIP: ICMP6_PKT
ICMP6 egressing on grp-int-1-1 (Base):
fe80::ea:4b:ff -> fe80::200:ff:fe00:1
Type: Router Advertisement (134)
Code: No Code (0)
Hop Limit : 64
Flags :
Retrans Time : 0
Def Life Time : 4500
Reachable Time: 0
Option : Src Link Layer Addr 00:00:5e:00:01:01
Option : Prefix : 2001:db8:101:d::/64
Flags : On Link Autoconfig
Valid Life Time: 86400
Pref Life Time: 3600
"
Verification
The following shows the IPoE session for MAC address 00:00:00:00:00:01:
*A:BNG-1# show service id 1 ipoe session mac 00:00:00:00:00:01
===============================================================================
IPoE sessions for svc-id 1
===============================================================================
Sap Id Mac Address Up Time MC-Stdby
Subscriber-Id
[CircuitID] | [RemoteID]
-------------------------------------------------------------------------------
1/1/1:111 00:00:00:00:00:01 0d 00:10:18
sub-11
-------------------------------------------------------------------------------
CID | RID displayed when included in session-key
Number of sessions : 1
===============================================================================
*A:BNG-1#
The IPoE session details for MAC address 00:00:00:00:00:01 are shown using the following command. The session time left is undefined (N/A), because no IPoE session-timeout is defined in the IPoE session policy. Re-authentication does not apply, so the minimum authentication interval is infinite (N/A).
*A:BNG-1# show service id 1 ipoe session mac 00:00:00:00:00:01 detail
===============================================================================
IPoE sessions for service 1
===============================================================================
SAP : 1/1/1:111
Mac Address : 00:00:00:00:00:01
Circuit-Id :
Remote-Id :
Session Key : sap-mac
MC-Standby : No
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-1
Termination Type : local
Up Time : 0d 00:09:42
Session Time Left : N/A
Last Auth Time : 02/03/2016 13:51:29
Min Auth Intvl (left) : infinite (N/A)
Persistence Key : N/A
Subscriber : "sub-11"
Sub-Profile-String : "sub-profile-1"
SLA-Profile-String : "sla-profile-1"
ANCP-String : ""
Int-Dest-Id : ""
App-Profile-String : ""
Category-Map-Name : ""
Acct-Session-Id : "EA4BFF000001A656B1F7D0"
Sap-Session-Index : 1
IP Address : 10.1.1.60/24
IP Origin : DHCP
Primary DNS : N/A
Secondary DNS : N/A
Primary NBNS : N/A
Secondary NBNS : N/A
Address-Pool : pool4-1
IPv6 Prefix : 2001:db8:101:d::/64
IPv6 Prefix Origin : LclPool
IPv6 Prefix Pool : "pool6-1"
IPv6 Del.Pfx. : N/A
IPv6 Del.Pfx. Origin : None
IPv6 Del.Pfx. Pool : ""
IPv6 Address : 2001:db8:101:c::1
IPv6 Address Origin : DHCP
IPv6 Address Pool : "pool6-1"
Primary IPv6 DNS : 2001:db8::1:1:1:1
Secondary IPv6 DNS : N/A
Radius Session-TO : N/A
Radius Class :
Radius User-Name :
-------------------------------------------------------------------------------
Number of sessions : 1
===============================================================================
*A:BNG-1#
The following command shows the subscriber hosts for this MAC address:
*A:BNG-1# show service id 1 subscriber-hosts mac 00:00:00:00:00:01
=============================================================
Subscriber Host table
=============================================================
Sap Subscriber
IP Address
MAC Address PPPoE-SID Origin Fwding State
-------------------------------------------------------------
1/1/1:111 sub-11
10.1.1.60
00:00:00:00:00:01 N/A DHCP Fwding
1/1/1:111 sub-11
2001:db8:101:c::1/128
00:00:00:00:00:01 N/A IPoE-DHCP6 Fwding
1/1/1:111 sub-11
2001:db8:101:d::/64
00:00:00:00:00:01 N/A IPoE-SLAAC Fwding
-------------------------------------------------------------
Number of subscriber hosts : 3
=============================================================
*A:BNG-1#
The following commands show the corresponding dhcp and dhcp6 lease-states:
*A:BNG-1# show service id 1 dhcp lease-state session ipoe
===============================================================================
DHCP lease state table, service 1
===============================================================================
IP Address Mac Address Sap/Sdp Id Remaining Lease MC
LeaseTime Origin Stdby
-------------------------------------------------------------------------------
10.1.1.60 00:00:00:00:00:01 1/1/1:111 00h13m17s DHCP
-------------------------------------------------------------------------------
Number of lease states : 1
===============================================================================
*A:BNG-1#
*A:BNG-1# show service id 1 dhcp6 lease-state session ipoe
===============================================================================
DHCP lease state table, service 1
===============================================================================
IP Address Mac Address Sap/Sdp Id Remaining Lease MC
LeaseTime Origin Stdby
-------------------------------------------------------------------------------
2001:db8:101:c::1/128
00:00:00:00:00:01 1/1/1:111 23h59m02s DHCP
-------------------------------------------------------------------------------
Number of lease states : 1
===============================================================================
*A:BNG-1#
IPoE Session Authentication through AAA/RADIUS
The FreeRADIUS server users file contains following data for the connecting device:
00:00:00:00:00:01 Cleartext-Password := "spasswd"
Alc-Subsc-ID-Str = "ipoe-%{User-name}",
Alc-Subsc-Prof-Str = "sub-prof-1",
Alc-SLA-Prof-Str = "sla-prof-1",
Framed-Pool = "pool4-1",
Framed-Ipv6-Pool = "pool6-1",
Alc-Delegated-IPv6-Pool = "pool6-1",
Alc-Relative-Session-Timeout = "300"
The authentication policy radius-pol used in this example is defined as follows:
configure
subscriber-mgmt
authentication-policy "radius-pol"
password letmein
include-radius-attribute
acct-session-id
circuit-id
sap-session-index
exit
radius-server-policy "rsp-1"
exit
The IPoE session policy used in this example is defined as follows. The key now also includes the circuit ID.
configure
subscriber-mgmt
ipoe-session-policy "sespol-sap-mac-cid" create
description "key also including cid now"
session-key sap mac cid
no session-timeout
exit
The authentication and IPoE session policies are then applied to the group interface grp-int-1-1:
configure
service
ies 1 customer 1 create
subscriber-interface "sub-int-1"
group-interface "grp-int-1-1"
authentication-policy "radius-pol"
ipoe-session
ipoe-session-policy "sespol-sap-mac-cid"
sap-session-limit 100
session-limit 100
no shutdown
exit
The authentication policy takes precedence over any LUDB applied in one of the subcontexts of that group interface.
Debug
The following debug trace appears when the user with MAC address 00:00:00:00:00:01 first connects using DHCPv6 (IA_NA and IA_PD) and subsequently connects using DHCPv4.
The ESM data source is accessed just once, immediately after the DHCPv6 Solicit message. Because LDRA is active, the Solicit message is embedded in the Relay Forward message. The RADIUS server is sent an Access-Request message including the circuit ID, and returns an Access-Accept message including the Alc-Relative-Session-Timeout attribute (message 3). Message 14 is the final IPv6 Reply message containing both the IA_NA address and the IA_PD prefix used by the CPE. Messages 15 through 22 are the DHCPv4 DORA messages.
The initial DHCPv6 Solicit message and the initial DHCPv4 Discover message contain the same interface ID/CID (11), which is why no re-authentication is triggered. The IPoE session is deleted when the RADIUS-provided session timer expires, so the BNG releases both the IPv4 and the IPv6 address (messages 23 through 31).
1 2016/02/03 14:51:27.54 CET MINOR: DEBUG #2001 Base TIP
"TIP: DHCP6_PKT
Incoming DHCP6 Msg : RELAY_FORW (12)
on itf grp-int-1-1
Hop Count : 0
Link Addr : ::
Peer Addr : fe80::200:ff:fe00:1
Option : RELAY_MSG (9), Length : 60
Msg Type : SOLICIT (1)
Trans Id : 0x89ade3
Option : CLIENTID (1), Length : 14
LLT : HwTyp=0001,T=507311564,LL=000000000001
000100011e3cf5cc000000000001
Option : IA_PD (25), Length : 12
IAID : 1
Time1: 0 seconds
Time2: 0 seconds
Option : IA_NA (3), Length : 12
IAID : 2
Time1: 0 seconds
Time2: 0 seconds
Option : ORO (6), Length : 2
Requested Option : DNS_NAME_SRVR (23)
Option : INTERFACE_ID (18), Length : 2
Interface Id : 3131 (11)
"
2 2016/02/03 14:51:27.54 CET MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 172.16.1.1:1812 id 165 len 109 vrid 1 pol rsp-1
USER NAME [1] 17 00:00:00:00:00:01
PASSWORD [2] 16 8DF.2ZKk.XRvmblEXcKEOk
NAS IP ADDRESS [4] 4 192.0.2.1
VSA [26] 4 DSL(3561)
AGENT CIRCUIT ID [1] 2 11
SESSION ID [44] 22 EA4BFF000001C356B205DF
VSA [26] 6 Alcatel(6527)
SAP SESSION INDEX [180] 4 1
"
3 2016/02/03 14:51:27.54 CET MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 165 len 131 from 172.16.1.1:1812 vrid 1 pol rsp-1
VSA [26] 24 Alcatel(6527)
SUBSC ID STR [11] 22 ipoe-00:00:00:00:00:01
VSA [26] 12 Alcatel(6527)
SUBSC PROF STR [12] 10 sub-prof-1
VSA [26] 12 Alcatel(6527)
SLA PROF STR [13] 10 sla-prof-1
FRAMED POOL [88] 7 pool4-1
FRAMED IPV6 POOL [100] 7 pool6-1
VSA [26] 9 Alcatel(6527)
DELEGATED IPV6 POOL [131] 7 pool6-1
VSA [26] 6 Alcatel(6527)
RELATIVE SESSION TIMEOUT [160] 4 300
"
4 2016/02/03 14:51:27.55 CET MINOR: DEBUG #2001 Base TIP
"TIP: DHCP6_PKT
Outgoing DHCP6 Msg : RELAY_FORW (12)
to itf int-DHCP
Hop Count : 1
Link Addr : 2001:db8:101::1
Peer Addr : fe80::200:ff:fe00:1
Option : RELAY_MSG (9), Length : 104
Msg Type : RELAY_FORW (12)
Hop Count : 0
Link Addr : ::
Peer Addr : fe80::200:ff:fe00:1
Option : RELAY_MSG (9), Length : 60
Msg Type : SOLICIT (1)
Trans Id : 0x89ade3
---snip---
Option : VENDOR_OPTS (17), Length : 36
Enterprise : 0000197f
Option : WAN_POOL (1), Length : 7
pool6-1
Option : PFX_POOL (2), Length : 7
pool6-1
Option : PFX_LEN (3), Length : 1
56
Option : RESERVED_NA_LEN (4), Length : 1
64
"
---snip---
14 2016/02/03 14:51:27.67 CET MINOR: DEBUG #2001 Base TIP
"TIP: DHCP6_PKT
Outgoing DHCP6 Msg : RELAY_REPLY (13)
to itf grp-int-1-1
Hop Count : 0
Link Addr : ::
Peer Addr : fe80::200:ff:fe00:1
Option : RELAY_MSG (9), Length : 145
Msg Type : REPLY (7)
Trans Id : 0x4c546f
---snip---
Option : IA_PD (25), Length : 41
IAID : 1
Time1: 1800 seconds
Time2: 2880 seconds
Option : IAPREFIX (26), Length : 25
Prefix : 2001:db8:f101:700::/56
Preferred Lifetime : 3600 seconds
Valid Lifetime : 86400 seconds
Option : IA_NA (3), Length : 40
IAID : 2
Time1: 1800 seconds
Time2: 2880 seconds
Option : IAADDR (5), Length : 24
Address : 2001:db8:101:c::1
Preferred Lifetime : 3600 seconds
Valid Lifetime : 86400 seconds
Option : DNS_NAME_SRVR (23), Length : 16
Server : 2001:db8::1:1:1:1
Option : INTERFACE_ID (18), Length : 2
Interface Id : 3131 (11)
"
15 2016/02/03 14:51:34.59 CET MINOR: DEBUG #2001 Base PIP
"PIP: DHCP
instance 1 (Base), interface index 6 (grp-int-1-1),
received DHCP Boot Request on Interface grp-int-1-1 (1/1/1:111) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:00:00:00:00:01 xid: 0x1
DHCP options:
[82] Relay agent information: len = 4
[1] Circuit-id: 11
[53] Message type: Discover
[255] End
"
---snip---
22 2016/02/03 14:51:34.73 CET MINOR: DEBUG #2001 Base PIP
"PIP: DHCP
instance 1 (Base), interface index 6 (grp-int-1-1),
transmitted DHCP Boot Reply to Interface grp-int-1-1 (1/1/1:111) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 10.1.1.64
siaddr: 10.11.11.1 giaddr: 10.1.1.254
chaddr: 00:00:00:00:00:01 xid: 0x1
DHCP options:
[82] Relay agent information: len = 4
[1] Circuit-id: 11
[53] Message type: Ack
[54] DHCP server addr: 10.11.11.1
[51] Lease time: 900
[1] Subnet mask: 255.255.255.0
[3] Router: 10.1.1.254
[255] End
"
23 2016/02/03 14:56:26.55 CET MINOR: DEBUG #2001 Base TIP
"TIP: DHCP6_PKT
Outgoing DHCP6 Msg : RELAY_FORW (12)
to itf int-DHCP
Hop Count : 0
Link Addr : 2001:db8:101::1
Peer Addr : fe80::200:ff:fe00:1
Option : RELAY_MSG (9), Length : 80
Msg Type : RELEASE (8)
Trans Id : 0x000000
---snip---
Option : INTERFACE_ID (18), Length : 22
Interface Id : 5f746d6e785f696e7465726e616c5f636c65616e7570 ( snipped )
"
---snip---
26 2016/02/03 14:56:26.55 CET MINOR: DEBUG #2001 Base PIP
"PIP: DHCP
instance 1 (Base),
transmitted DHCP Boot Request to 10.11.11.1 Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 10.1.1.64 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 00:00:00:00:00:01 xid: 0x0
DHCP options:
[53] Message type: Release
[54] DHCP server addr: 10.11.11.1
[255] End
"
---snip---
31 2016/02/03 14:56:26.56 CET MINOR: DEBUG #2001 Base TIP
"TIP: DHCP6_PKT
Incoming DHCP6 Msg : RELAY_REPLY (13)
on itf int-DHCP
Hop Count : 0
Link Addr : 2001:db8:101::1
Peer Addr : fe80::200:ff:fe00:1
Option : RELAY_MSG (9), Length : 89
Msg Type : REPLY (7)
---snip---
Option : IA_PD (25), Length : 49
IAID : 1
Time1: 0 seconds
Time2: 0 seconds
Option : STATUS_CODE (13), Length : 33
Status : SUCCESS (0)
All prefixes have been released
Option : INTERFACE_ID (18), Length : 22
Interface Id : 5f746d6e785f696e7465726e616c5f636c65616e7570 ( snipped )
"
Verification
The following command shows the session details for MAC address 00:00:00:00:00:01. The key now includes the circuit ID (11), and the session timer is running. The RADIUS-provided session timeout is 5 minutes.
*A:BNG-1# show service id 1 ipoe session mac 00:00:00:00:00:01 detail
===============================================================================
IPoE sessions for service 1
===============================================================================
SAP : 1/1/1:111
Mac Address : 00:00:00:00:00:01
Circuit-Id : 11
Remote-Id :
Session Key : sap-mac-cid
MC-Standby : No
Subscriber-interface : sub-int-1
Group-interface : grp-int-1-1
Termination Type : local
Up Time : 0d 00:03:13
Session Time Left : 0d 00:01:47
Last Auth Time : 02/03/2016 14:51:28
Min Auth Intvl (left) : infinite (N/A)
Persistence Key : N/A
Subscriber : "ipoe-00:00:00:00:00:01"
Sub-Profile-String : "sub-prof-1"
SLA-Profile-String : "sla-prof-1"
ANCP-String : ""
Int-Dest-Id : ""
App-Profile-String : ""
Category-Map-Name : ""
Acct-Session-Id : "EA4BFF000001C256B205DF"
Sap-Session-Index : 1
IP Address : 10.1.1.64/24
IP Origin : DHCP
Primary DNS : N/A
Secondary DNS : N/A
Primary NBNS : N/A
Secondary NBNS : N/A
Address-Pool : pool4-1
IPv6 Prefix : N/A
IPv6 Prefix Origin : None
IPv6 Prefix Pool : ""
IPv6 Del.Pfx. : 2001:db8:f101:700::/56
IPv6 Del.Pfx. Origin : DHCP
IPv6 Del.Pfx. Pool : "pool6-1"
IPv6 Address : 2001:db8:101:c::1
IPv6 Address Origin : DHCP
IPv6 Address Pool : "pool6-1"
Primary IPv6 DNS : N/A
Secondary IPv6 DNS : N/A
Radius Session-TO : 0d 00:05:00
Radius Class :
Radius User-Name : 00:00:00:00:00:01
-------------------------------------------------------------------------------
Number of sessions : 1
===============================================================================
*A:BNG-1#
Three hosts are created, as the following command shows:
*A:BNG-1# show service id 1 subscriber-hosts mac 00:00:00:00:00:01
=============================================================
Subscriber Host table
=============================================================
Sap Subscriber
IP Address
MAC Address PPPoE-SID Origin Fwding State
-------------------------------------------------------------
1/1/1:111 ipoe-00:00:00:00:00:01
10.1.1.64
00:00:00:00:00:01 N/A DHCP Fwding
1/1/1:111 ipoe-00:00:00:00:00:01
2001:db8:101:c::1/128
00:00:00:00:00:01 N/A IPoE-DHCP6 Fwding
1/1/1:111 ipoe-00:00:00:00:00:01
2001:db8:f101:700::/56
00:00:00:00:00:01 N/A IPoE-DHCP6 Fwding
-------------------------------------------------------------
Number of subscriber hosts : 3
=============================================================
*A:BNG-1#
After 300 seconds, the session is deleted:
*A:BNG-1# show service id 1 ipoe session detail
No entries found.
*A:BNG-1#
Conclusion
IPoE sessions offer ISPs a simplified way to manage dual-stack IPoE devices. IPoE sessions have features similar to PPP sessions, in terms of authentication, mid-session changes, and accounting. IPoE sessions can be used on regular, capture, and managed SAPs, and are supported in single- and dual-homed scenarios, including wholesale and retail configurations.