WiFi Aggregation and Offload — Basic Open SSID
This chapter provides information about WiFi Aggregation and Offload — Basic Open SSID.
Topics in this chapter include:
Applicability
The information and configuration in this chapter are based on SR OS Release 12.0.R5.
Overview
WiFi Aggregation and Offload functionality for the 7750 SR is supported on SR OS 10.0.R3 or later. The functionality includes a RADIUS proxy server with a RADIUS proxy cache and support for soft-GRE tunnels.
WLAN-GW subscribers are implemented using Enhanced Subscriber Management (ESM) on the Control Processing Module (CPM), to benefit from the extensive ESM features available on the 7750 SR platform. Many different WiFi Offload configurations are possible, with the two most versatile configurations being open and secure Service Set Identifier (SSID).
This configuration should be used as a starting point for operators who need to offer an open SSID, where any client can connect to an Access Point (AP) and obtain an IP address without authentication. In most cases, operators want users to go through an authentication process before allowing full Internet access using the open SSID; therefore, this configuration also includes a web portal.
IP address assignment and Internet connectivity can be achieved using various methods in SR OS. In this configuration, a local DHCP server provides IP addresses to the User Equipment (UE) and routing to the Internet is performed using Global Routing Table (GRT) leaking.
Several considerations typically affect the choice of a WiFi Offload solution:
Access can be free or paid.
Equipment can be preconfigured or users can bring their own WiFi device.
When there is no pre-existing subscription, an open SSID is the most obvious solution. To provide a paywall or to have the user acknowledge certain terms of use due to legal reasons, a web portal may also be required.
When a web portal is implemented, users who connect to the open SSID which are not yet authenticated have all their web traffic redirected to the web portal landing page. This is performed using an http-redirect filter applied to the initial (limited) Service Level Agreement (SLA) profile assigned to the UE. Typically, the operating system of the UE will detect the presence of the web portal and automatically open the login page for the user. When the user logs in, the web portal sends a RADIUS Change of Authorization (CoA) request to the WLAN-GW, changing the SLA profile to one that does not contain an http-redirect filter.
Besides authentication, a major consideration is the method used to achieve Internet connectivity. Will the users require public addresses or are private addresses sufficient? In case few public IP addresses are available, private IP addresses can be assigned to UEs and the WLAN-GW can perform a Network Address Translation (NAT) function. If public routable IP addresses can be made available to all UEs, traffic from the UEs can be routed by the WLAN-GW to the Internet.
When a UE connects to an open SSID (as shown in Call Flow for Open SSID), typically the UE attempts to obtain an IP address using Dynamic Host Configuration Protocol (DHCP). The WLAN-GW can serve as a DHCP relay or proxy and may obtain the IP address from an external source, or use a local DHCP server function. A DHCP Discover or Request packet from a UE will trigger a form of authentication where the WLAN-GW requests information about the UE, such as SLA profile or DHCP local pool name. This authentication is separate from the web portal authentication and occurs immediately when a UE connects.
In summary:
DHCP Discover triggering RADIUS authentication
DHCP completes and UE has SLA profile with limited access
UE logs into a web portal
Successful login causes the portal to send a RADIUS CoA which assigns an SLA profile with full access
Figure 1. Call Flow for Open SSID 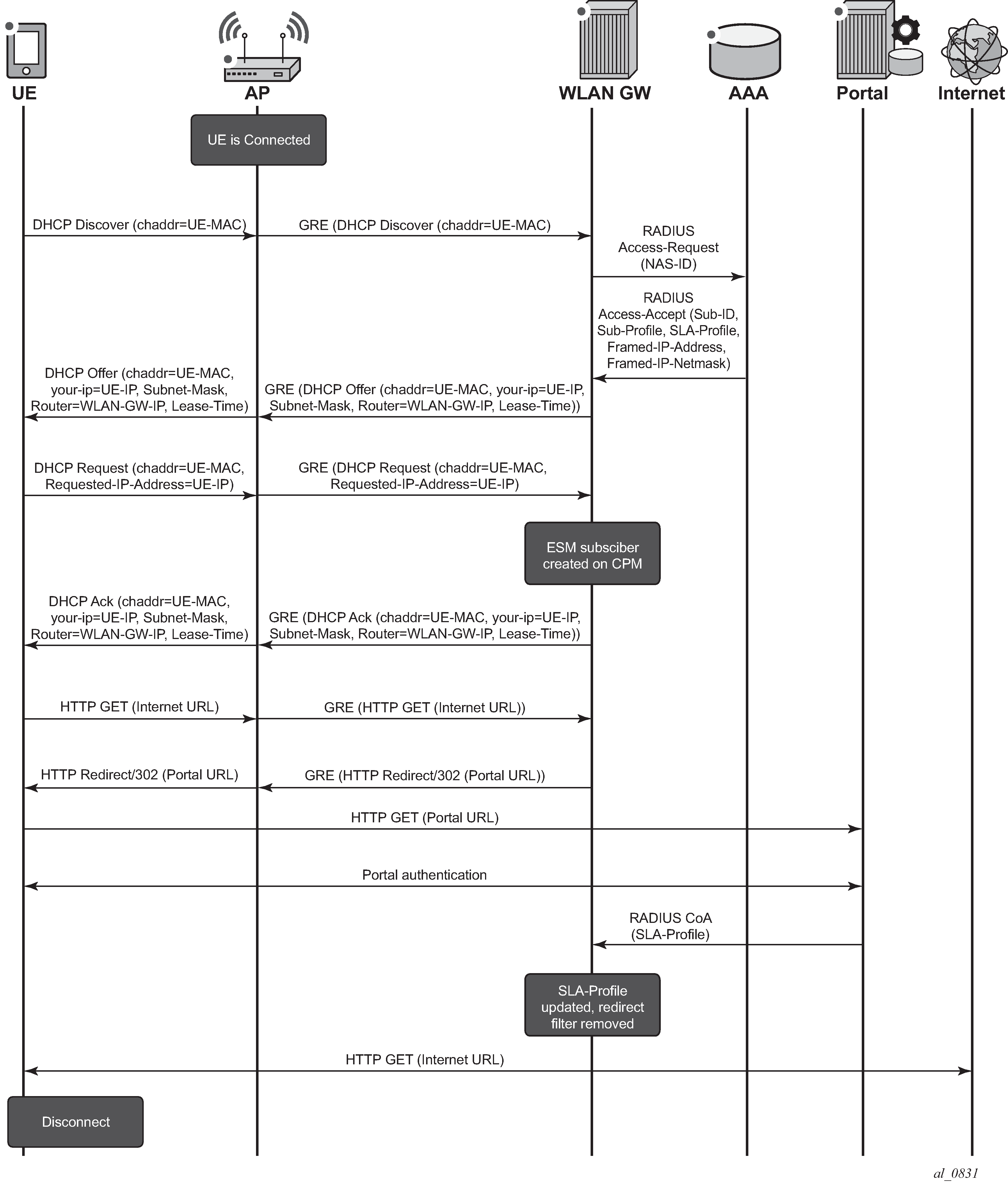
The SR OS is flexible in allowing the operator to separate the various WiFi Offload functions between different routing instances. All functions can be configured in the same routing instance, or as shown in WiFi Offload Scenario with Open SSID and Local DHCP Server, the connectivity to the APs (and soft-GRE tunnels) can be provided in one Virtual Private Routed Network (VPRN), the users can be instantiated in another VPRN, and Authentication, Authorization and Accounting (AAA) access can be provided in yet another routing instance (in this case, the Base router). This clear separation of functions can enhance security; for example, by separating user traffic from authentication traffic.
Configuration
The WiFi offload scenario shown in WiFi Offload Scenario with Open SSID and Local DHCP Server has following characteristics:
Open SSID with web portal authentication
Local breakout to Internet using GRT leaking, routing through Base routing instance
Same private IP address assigned to all UEs, with L2-aware NAT
AP access in VPRN 1000
UEs terminated in VPRN 2005
Local DHCP server assigning public IP addresses
Figure 2. WiFi Offload Scenario with Open SSID and Local DHCP Server 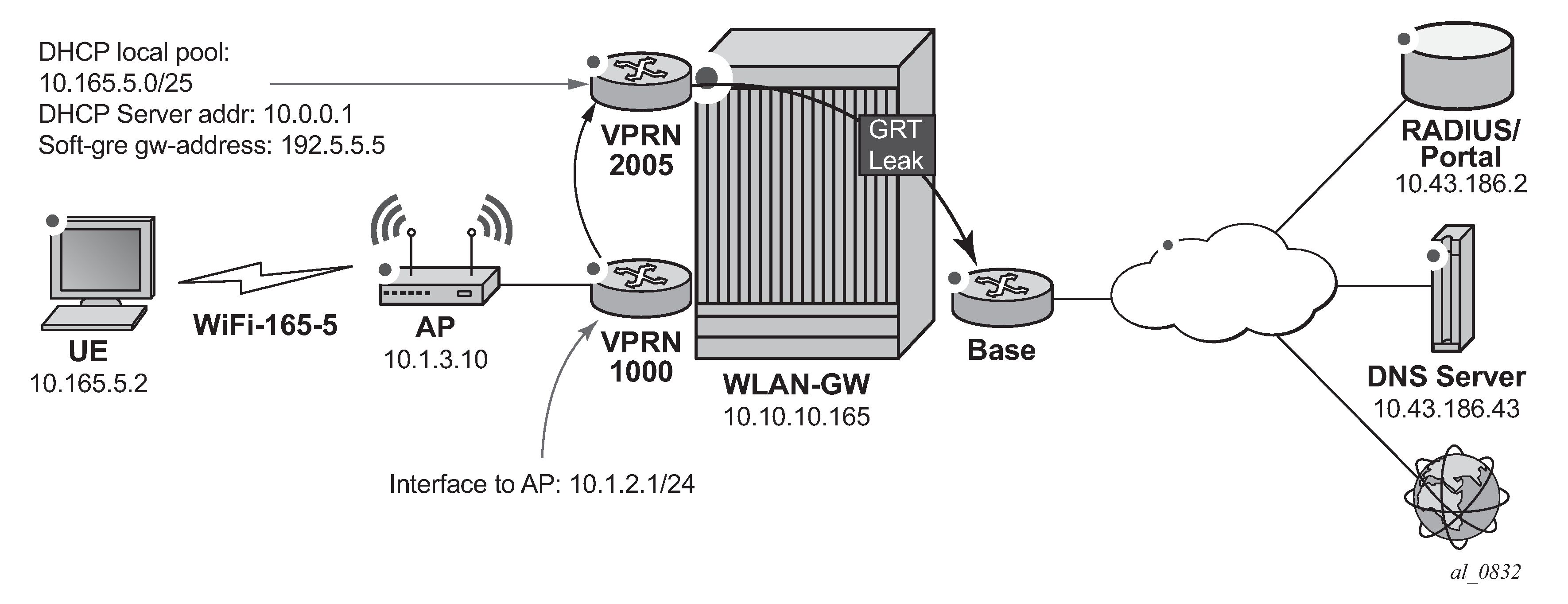
WLAN-GW
Note that the uplink interface, Interior Gateway Protocol (IGP), and system configuration is outside the scope of this document.
The following card and Media Dependent Adapter (MDA) configuration shows only the WLAN-Input/Output Module (IOM). An IOM card containing two Multi-Service Integrated Service Adapter (MS-ISA) cards provides the WLAN-GW functionality. The MDA type for the ISA cards is isa-bb, the same type that is used for NAT.
*A:WLAN-GW# /configure card 2
*A:WLAN-GW>config>card# info
----------------------------------------------
card-type iom3-xp-b
mda 1
mda-type isa-bb
no shutdown
exit
mda 2
mda-type isa-bb
no shutdown
exit
no shutdown
----------------------------------------------
The following ISA configuration defines a wlan-gw-group referencing the IOM in slot two which hosts the two MS-ISA cards and providing the WLAN-GW functions.
A:WLAN-GW# /configure isa
A:WLAN-GW>config>isa# info
----------------------------------------------
wlan-gw-group 1 create
active-iom-limit 1
iom 2
no shutdown
exit
----------------------------------------------
The following is a RADIUS server configuration, where the secret must match the secret configured on the external RADIUS server. The accept-coa option must be configured to allow the change of SLA profile by the web portal using a CoA request.
*A:WLAN-GW# /configure router radius-server
*A:WLAN-GW>config>router>radius-server# info
----------------------------------------------
server "Server2" address 10.43.186.2 secret "zmLYVgt8UOLypJamceNSSHDWbZproq7Y" hash2 create
accept-coa
exit
----------------------------------------------
The following AAA configuration contains a RADIUS server policy used in the authentication policy. The source address must match the IP address configured for this client on the RADIUS server.
*A:WLAN-GW# /configure aaa
*A:WLAN-GW>config>aaa# info
----------------------------------------------
radius-server-policy "RS_5" create
servers
router "Base"
source-address 10.10.10.165
server 1 name "Server2"
exit
exit
----------------------------------------------
The following policy configuration is used for exporting routes so that they are reachable by the public network. These policies are used for exporting UE routes in subsequent configuration sections.
*A:WLAN-GW# /configure router policy-options
*A:WLAN-GW>config>router>policy-options# info
----------------------------------------------
prefix-list "WiFi-clients"
prefix 10.165.0.0/16 longer
exit
policy-statement "WiFi-clients"
entry 10
from
prefix-list "WiFi-clients"
exit
action accept
exit
exit
exit
----------------------------------------------
The uplink network configuration is outside the scope of this document. However, note that the IGP (here ISIS) must be aware of the UE addresses so that they are accessible from the Internet.
*A:WLAN-GW# /configure router isis
*A:WLAN-GW>config>router>isis# info
----------------------------------------------
export "WiFi-clients"
----------------------------------------------
The following IP filter redirects all HTTP traffic to the web portal. The filter should also allow DNS and potentially other traffic, so the entry that allows TCP port 80 traffic to the web portal address must be placed before the entry that redirects all traffic to that portal; otherwise, there will be a redirect loop.
The HTTP redirect URL also includes a parameter that provides the MAC address of the UE to the web portal. In this configuration, either $MAC or $SUB can be used since both variables contain the MAC address of the UE. The web portal can reply with a CoA request specifying this particular UE MAC as the Subscriber ID after successful login. The URL also returns the IP address of the WLAN-GW to the web portal, so that the portal knows which WLAN-GW to send the CoA request to.
*A:WLAN-GW# /configure filter
*A:WLAN-GW>config>filter# info
----------------------------------------------
ip-filter 2005 create
default-action forward
entry 70 create
match protocol udp
dst-port eq 53
exit
action forward
exit
entry 80 create
match protocol icmp
exit
action forward
exit
entry 90 create
match protocol tcp
dst-ip 10.43.186.2/32
dst-port eq 80
exit
action forward
exit
entry 100 create
match protocol tcp
dst-port eq 80
exit
action http-redirect "http://portal2.3ls.net/portal-no-login.php?gw=10.10.10.165&mac=$SUB"
exit
exit
The following is a subscriber management configuration, with the RADIUS authentication policy used to authenticate DHCP requests, including the accept-authorization-change option to allow for SLA profile change after portal authentication. This DHCP authentication request also sends the NAS ID attribute that allows the RADIUS server to match on the configuration for this particular SSID. All UEs will be authenticated with their MAC address as user name, and alcatel as their password (any DHCP request will result in a successful authentication).
Two SLA profiles are required: profile SLAP_5_portal is initially used for each UE and refers to the portal redirect filter, while profile SLAP is applied using a CoA request after the user successfully authenticates on the web portal. A subscriber identity policy is also required.
configure subscriber-mgmt
authentication-policy "WiFi-165-5-auth-policy" create
password alcatel
accept-authorization-change
include-radius-attribute
nas-identifier
exit
radius-server-policy "RS_5"
exit
sla-profile "SLAP" create
exit
sla-profile "SLAP_5_portal" create
ingress
ip-filter 2005
exit
exit
sub-profile "SUBP" create
exit
sub-ident-policy "SIP" create
sub-profile-map
use-direct-map-as-default
exit
sla-profile-map
use-direct-map-as-default
exit
exit
The following VPRN 1000 configuration contains the interface to the AP, and has GRT lookup with export-grt configured to allow APs to be managed from the Base routing instance.
*A:WLAN-GW# /configure service vprn 1000
*A:WLAN-GW>config>service>vprn# info
----------------------------------------------
route-distinguisher 65400:1000
interface "toAP3" create
address 10.1.3.1/24
sap 1/1/10 create
exit
exit
grt-lookup
enable-grt
static-route 0.0.0.0/0 grt
exit
export-grt "WiFi-APs"
exit
no shutdown
----------------------------------------------
VPRN 2005 is used for UE termination and contains:
A local DHCP server with a single pool of addresses that are assigned to UEs.
A loopback interface used by the DHCP server.
A subscriber interface and group interface of type wlangw (called softgre prior to Release 12.0).
Subscriber parameters.
The authentication policy, which will run each time a UE requests a DHCP address.
The host-connectivity-verify function, which periodically checks the presence of UEs and quickly removes disconnected UEs even before their DHCP lease expires; the WLAN-GW has no other way of knowing when a UE has disconnected from the AP.
The wlan-gw CLI-node (called soft-gre prior to Release 12.0), including the wlan-gw GRE tunnel end-point address,and the routing instance where AP traffic is terminated, the ISA WLAN-GW group, and mobility parameters, which allow the UE state to be kept if the UE moves between two APs broadcasting the same SSID.
GRT lookup with export-grt configured to allow UE traffic to be routed to the Internet.
*A:WLAN-GW# /configure service vprn 2005 *A:WLAN-GW>config>service>vprn# info ---------------------------------------------- description "WiFi-165-5 Open SSID" dhcp local-dhcp-server "local_dhcp_2005" create use-pool-from-client pool "pool1" create max-lease-time hrs 1 options dns-server 10.43.186.43 exit subnet 10.165.5.0/25 create options subnet-mask 255.255.255.128 default-router 10.165.5.1 exit address-range 10.165.5.2 10.165.5.99 exit exit no shutdown exit exit route-distinguisher 65400:2005 interface "dhcp-server" create address 10.0.0.1/24 local-dhcp-server "local_dhcp_2005" loopback exit subscriber-interface "SI5" create address 10.165.5.1/24 group-interface "GI5" wlangw create sap-parameters sub-sla-mgmt def-sla-profile "SLAP_5_portal" def-sub-profile "SUBP" sub-ident-policy "SIP" exit exit dhcp option action replace circuit-id no remote-id vendor-specific-option pool-name exit exit server 10.0.0.1 trusted lease-populate 10000 gi-address 10.165.5.1 no shutdown exit authentication-policy "WiFi-165-5-auth-policy" host-connectivity-verify interval 5 action remove wlan-gw gw-address 192.5.5.5 mobility trigger data iapp exit router 1000 wlan-gw-group 1 no shutdown exit exit exit grt-lookup enable-grt exit export-grt "WiFi-clients" exit no shutdown
Freeradius
This simple default configuration section matches on any host. During the DHCP authentication phase, RADIUS returns the DHCP pool name pool1 informing the WLAN-GW DHCP server which pool to assign the UE IP address from:
/etc/freeradius/users
DEFAULT Auth-Type := Local, User-Password := "alcatel", user-name=~""
Alc-Subsc-ID-Str = "%{User-Name}",
Framed-Pool = "pool1",
In /etc/freeradius/clients.conf, the secret must match the secret configured in the WLAN-GW RADIUS server configuration.
client 10.10.10.165 {
secret = alcatel
shortname = WLAN-GW
}
The RADIUS CoA sent during successful portal login allows this UE full access, by applying SLA profile SLAP which does not have an http-redirect filter.
echo "ALC-Subsc-Id-Str='68:7f:74:8b:3d:d7',ALC-Subsc-Prof-Str='SUBP_5',ALC-SLA-Prof-Str='.SLAP',Alc-Primary-Dns = '10.43.186.43'" | /usr/bin/radclient -x -r 1 -t 2 '10.10.10.165' coa 'alcatel'
Access Points
At a minimum, the following must be configured on the Access Point:
IP address 10.1.3.10/24
Default route to 10.1.3.1
Open SSID WiFi-165-5 mapped to VLAN 50
Soft-GRE tunnel with destination 192.5.5.5, with VLAN 50 mapped to this tunnel
Show Commands
The following show commands reflect the status of the router after the UE has connected and obtained an IP address using DHCP.
The following output displays the UEs presently connected.
*A:WLAN-GW# show subscriber-mgmt wlan-gw ue
===============================================================================
User Equipments
===============================================================================
MAC address : 68:7f:74:8b:3d:d7
-------------------------------------------------------------------------------
VLAN Q-tag : 50
MPLS label : (Not Specified)
Tunnel router : 1000
Tunnel remote IP address : 10.1.3.10
Tunnel local IP address : 192.5.5.5
Retail service : N/A
SSID : (Not Specified)
Previous Access Point IP : (Not Specified)
IMSI : (Not Specified)
Last move time : 2014/09/22 10:47:58
-------------------------------------------------------------------------------
No. of UE: 1
===============================================================================
The DHCP lease information indicates that the address was assigned by the local DHCP server.
*A:WLAN-GW# show service id 2005 dhcp lease-state
===============================================================================
DHCP lease state table, service 2005
===============================================================================
IP Address Mac Address Sap/Sdp Id Remaining Lease MC
LeaseTime Origin Stdby
-------------------------------------------------------------------------------
10.165.5.2 68:7f:74:8b:3d:d7 [2/1/nat-out-ip:20* 00h59m27s DHCP
-------------------------------------------------------------------------------
Number of lease states : 1
===============================================================================
* indicates that the corresponding row element may have been truncated.
DHCP statistics can be displayed using following command.
*A:WLAN-GW# show service id 2005 dhcp statistics
====================================================================
DHCP Global Statistics, service 2005
====================================================================
Rx Packets : 2
Tx Packets : 2
Rx Malformed Packets : 0
Rx Untrusted Packets : 0
Client Packets Discarded : 0
Client Packets Relayed : 2
Client Packets Snooped : 0
Client Packets Proxied (RADIUS) : 0
Client Packets Proxied (User-Db) : 0
Client Packets Proxied (Lease-Split) : 0
Server Packets Discarded : 0
Server Packets Relayed : 2
Server Packets Snooped : 0
DHCP RELEASEs Spoofed : 0
DHCP FORCERENEWs Spoofed : 0
====================================================================
The route table for the routing instance where UEs are terminated shows an entry for the UE.
*A:WLAN-GW# show router 2005 route-table
===============================================================================
Route Table (Service: 2005)
===============================================================================
Dest Prefix[Flags] Type Proto Age Pref
Next Hop[Interface Name] Metric
-------------------------------------------------------------------------------
10.0.0.0/24 Local Local 00h32m12s 0
dhcp-server 0
10.165.5.0/24 Local Local 00h27m20s 0
SI5 0
10.165.5.2/32 Remote Sub Mgmt 00h00m33s 0
[GI5] 0
-------------------------------------------------------------------------------
No. of Routes: 3
Flags: n = Number of times nexthop is repeated
B = BGP backup route available
L = LFA nexthop available
S = Sticky ECMP requested
===============================================================================
The active subscribers view shows the initial limited SLA profile SLAP_5_portal before the user has logged in to the portal.
*A:WLAN-GW>config>service>vprn# show service active-subscribers
===============================================================================
Active Subscribers
===============================================================================
-------------------------------------------------------------------------------
Subscriber 68:7f:74:8b:3d:d7 (SUBP)
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
(1) SLA Profile Instance sap:[2/1/nat-out-ip:2049.3] - sla:SLAP_5_portal
-------------------------------------------------------------------------------
IP Address
MAC Address PPPoE-SID Origin
--------------------------------------------------------
10.165.5.2
68:7f:74:8b:3d:d7 N/A DHCP
-------------------------------------------------------------------------------
Number of active subscribers : 1
-------------------------------------------------------------------------------
The following output shows the active subscribers view after the user has logged in and the SLA profile has been updated with the unrestricted SLA profile SLAP.
*A:WLAN-GW# show service active-subscribers
===============================================================================
Active Subscribers
===============================================================================
-------------------------------------------------------------------------------
Subscriber 68:7f:74:8b:3d:d7 (SUBP_5)
-------------------------------------------------------------------------------
-------------------------------------------------------------------------------
(1) SLA Profile Instance sap:[2/1/nat-out-ip:2049.3] - sla:SLAP
-------------------------------------------------------------------------------
IP Address
MAC Address PPPoE-SID Origin
--------------------------------------------------------
10.165.5.2
68:7f:74:8b:3d:d7 N/A DHCP
-------------------------------------------------------------------------------
Number of active subscribers : 1
-------------------------------------------------------------------------------
The following output shows the RADIUS statistics for the DHCP authentication.
*A:WLAN-GW# show aaa radius-server-policy "RS_5" statistics
===============================================================================
RADIUS server policy "RS_5" statistics
===============================================================================
Tx transaction requests : 1
Rx transaction responses : 1
Transaction requests timed out : 0
Transaction requests send failed : 0
Packet retries : 0
Transaction requests send rejected : 0
Authentication requests failed : 0
Accounting requests failed : 0
Ratio of access-reject over auth responses : 0%
Transaction success ratio : 100%
Transaction failure ratio : 0%
Statistics last reset at : n/a
Server 1 "Server2" address 10.43.186.2 auth-port 1812 acct-port 1813
-------------------------------------------------------------------------------
Tx request packets : 1
Rx response packets : 1
Request packets timed out : 0
Request packets send failed : 0
Request packets send failed (overload) : 0
Request packets waiting for reply : 0
Response packets with invalid authenticator : 0
Response packets with invalid msg authenticator : 0
Authentication packets failed : 0
Accounting packets failed : 0
Avg auth response delay (10 100 1K 10K) in ms : 7.24 7.24 7.24 7.24
Avg acct response delay (10 100 1K 10K) in ms : n/a
Statistics last reset at : n/a
===============================================================================
The following output shows the CoA statistics after portal authentication.
*A:WLAN-GW# show subscriber-mgmt authentication coa-statistics
===============================================================================
Radius Notify Statistics Change-Of-Authorization Disconnect-Messages
===============================================================================
Requests Received 1 0
Requests Accepted 1 0
Requests Rejected 0 0
Requests Dropped 0 0
No Auth Policy found 0 0
Invalid message 0 0
Out of resources 0 0
Authentication failure 0 0
===============================================================================
Debug
The following is a complete debug of a UE connecting and logging in to the portal. Shortly after logging in, the UE disconnects from the SSID and the subscriber is removed by host-connectivity-verify.
The following debug configuration applies:
debug
router "Base"
radius
packet-type authentication accounting coa
detail-level medium
exit
exit
router "2005"
ip
dhcp
detail-level medium
mode egr-ingr-and-dropped
exit
exit
local-dhcp-server "local_dhcp_2005"
detail-level medium
mode dropped-only
exit
exit
service
id 2005
host-connectivity-verify
mac 68:7f:74:8b:3d:d7
exit
exit
exit
exit
The WLAN-GW is notified of the UE after receiving the first DHCP packet.
1 2014/09/22 10:47:58.46 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005), interface index 3 (GI5),
received DHCP Boot Request on Interface GI5 (2/1/nat-out-ip:2049.3) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[53] Message type: Discover
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[50] Requested IP addr: 10.165.5.2
[12] Host name: W81VM
[60] Class id: MSFT 5.0
[55] Param request list: len = 13
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
252 Unknown option
43 Vendor specific
[255] End
"
DHCP triggers sending the RADIUS Access-Request.
2 2014/09/22 10:47:58.48 EDT MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Access-Request(1) 10.43.186.2:1812 id 1 len 79 vrid 1 pol RS_5
USER NAME [1] 17 68:7f:74:8b:3d:d7
PASSWORD [2] 16 IyDg9t17sGTbfR/6h0Bs1U
NAS IP ADDRESS [4] 4 10.10.10.165
NAS IDENTIFIER [32] 14 WLAN-GW
"
The UE authentication request is always accepted and the Access-Accept message contains the required subscriber management and IP parameters, in this case, at least the subscriber ID string as well as the pool name to be used by the local DHCP server.
3 2014/09/22 10:47:58.50 EDT MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Access-Accept(2) id 1 len 52 from 10.43.186.2:1812 vrid 1 pol RS_5
VSA [26] 19 Alcatel(6527)
SUBSC ID STR [11] 17 68:7f:74:8b:3d:d7
FRAMED POOL [88] 5 pool1
"
The DHCP request is transmitted to the local DHCP server, which assigns the IP address to the UE.
4 2014/09/22 10:47:58.50 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005),
transmitted DHCP Boot Request to 10.0.0.1 Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 10.165.5.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[82] Relay agent information: len = 54
[1] Circuit-id: WLAN-GW|2005|GI5|2/1/nat-out-ip:2049.3
[9] Vendor-Specific info: len = 12
Enterprise [6527] : len = 7
[13] dhcpPool: pool1
[53] Message type: Discover
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[50] Requested IP addr: 10.165.5.2
[12] Host name: W81VM
[60] Class id: MSFT 5.0
[55] Param request list: len = 13
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
252 Unknown option
43 Vendor specific
[255] End
"
5 2014/09/22 10:47:58.50 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005),
received DHCP Boot Reply on 10.0.0.1 Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 10.165.5.2
siaddr: 10.0.0.1 giaddr: 10.165.5.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[82] Relay agent information: len = 54
[1] Circuit-id: WLAN-GW|2005|GI5|2/1/nat-out-ip:2049.3
[9] Vendor-Specific info: len = 12
Enterprise [6527] : len = 7
[13] dhcpPool: pool1
[53] Message type: Offer
[54] DHCP server addr: 10.0.0.1
[51] Lease time: 3600
[1] Subnet mask: 255.255.255.128
[3] Router: 10.165.5.1
[6] Domain name server: 10.43.186.43
[12] Host name: W81VM
[60] Class id: MSFT 5.0
[255] End
"
6 2014/09/22 10:47:58.52 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005), interface index 3 (GI5),
transmitted DHCP Boot Reply to Interface GI5 (2/1/nat-out-ip:2049.3) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 10.165.5.2
siaddr: 10.0.0.1 giaddr: 10.165.5.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[53] Message type: Offer
[54] DHCP server addr: 10.0.0.1
[51] Lease time: 3600
[1] Subnet mask: 255.255.255.128
[3] Router: 10.165.5.1
[6] Domain name server: 10.43.186.43
[12] Host name: W81VM
[60] Class id: MSFT 5.0
[255] End
"
7 2014/09/22 10:47:58.69 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005), interface index 3 (GI5),
received DHCP Boot Request on Interface GI5 (2/1/nat-out-ip:2049.3) Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[53] Message type: Request
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[50] Requested IP addr: 10.165.5.2
[54] DHCP server addr: 10.0.0.1
[12] Host name: W81VM
[81] client FQDN: rcode1: 0, rcode2: 0, domain name = (hex) 00 57 38 31 56
4d
[60] Class id: MSFT 5.0
[55] Param request list: len = 13
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
252 Unknown option
43 Vendor specific
[255] End
"
8 2014/09/22 10:47:58.69 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005),
transmitted DHCP Boot Request to 10.0.0.1 Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 10.165.5.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[82] Relay agent information: len = 54
[1] Circuit-id: WLAN-GW|2005|GI5|2/1/nat-out-ip:2049.3
[9] Vendor-Specific info: len = 12
Enterprise [6527] : len = 7
[13] dhcpPool: pool1
[53] Message type: Request
[61] Client id: (hex) 01 68 7f 74 8b 3d d7
[50] Requested IP addr: 10.165.5.2
[54] DHCP server addr: 10.0.0.1
[12] Host name: W81VM
[81] client FQDN: rcode1: 0, rcode2: 0, domain name = (hex) 00 57 38 31 56
4d
[60] Class id: MSFT 5.0
[55] Param request list: len = 13
1 Subnet mask
15 Domain name
3 Router
6 Domain name server
44 NETBIOS name server
46 NETBIOS type
47 NETBIOS scope
31 Router discovery
33 Static route
121 Unknown option
249 Unknown option
252 Unknown option
43 Vendor specific
[255] End
"
9 2014/09/22 10:47:58.69 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005),
received DHCP Boot Reply on 10.0.0.1 Port 67
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 10.165.5.2
siaddr: 10.0.0.1 giaddr: 10.165.5.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[82] Relay agent information: len = 54
[1] Circuit-id: WLAN-GW|2005|GI5|2/1/nat-out-ip:2049.3
[9] Vendor-Specific info: len = 12
Enterprise [6527] : len = 7
[13] dhcpPool: pool1
[53] Message type: Ack
[54] DHCP server addr: 10.0.0.1
[51] Lease time: 3600
[1] Subnet mask: 255.255.255.128
[3] Router: 10.165.5.1
[6] Domain name server: 10.43.186.43
[12] Host name: W81VM
[81] client FQDN: rcode1: 0, rcode2: 0, domain name = (hex) 00 57 38 31 56
4d
[60] Class id: MSFT 5.0
[255] End
"
10 2014/09/22 10:47:58.69 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005), interface index 3 (GI5),
transmitted DHCP Boot Reply to Interface GI5 (2/1/nat-out-ip:2049.3) Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 0.0.0.0 yiaddr: 10.165.5.2
siaddr: 10.0.0.1 giaddr: 10.165.5.1
chaddr: 68:7f:74:8b:3d:d7 xid: 0x8c0fc642
DHCP options:
[53] Message type: Ack
[54] DHCP server addr: 10.0.0.1
[51] Lease time: 3600
[1] Subnet mask: 255.255.255.128
[3] Router: 10.165.5.1
[6] Domain name server: 10.43.186.43
[12] Host name: W81VM
[81] client FQDN: rcode1: 0, rcode2: 0, domain name = (hex) 00 57 38 31 56
4d
[60] Class id: MSFT 5.0
[255] End
"
At this point in the configuration, the UE has network connectivity but all HTTP traffic is redirected to the web portal, as configured in the IP filter included in the initial SLA profile.
After web portal authentication, the WLAN-GW receives a RADIUS CoA for this subscriber, which includes the new unrestricted SLA profile SLAP.
11 2014/09/22 10:48:12.54 EDT MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Receive
Change of Authorization(43) id 162 len 71 from 10.43.186.2:55255 vrid 1
VSA [26] 19 Alcatel(6527)
SUBSC ID STR [11] 17 68:7f:74:8b:3d:d7
VSA [26] 8 Alcatel(6527)
SUBSC PROF STR [12] 6 SUBP_5
VSA [26] 6 Alcatel(6527)
SLA PROF STR [13] 4 SLAP
"
12 2014/09/22 10:48:12.54 EDT MINOR: DEBUG #2001 Base RADIUS
"RADIUS: Transmit
Change of Authorization Ack(44) 10.43.186.2:55255 id 162 len 20 vrid 1
"
The host has accessed a few web sites, then disconnected from the SSID, which is not known by the WLAN-GW. After 5 minutes of inactivity, host-connectivity-verify removes the subscriber and the DHCP lease is cleared.
13 2014/09/22 10:48:58.90 EDT MINOR: DEBUG #2001 vprn2005 SHCV
"SHCV: Periodic Check
2/1/nat-out-ip:2049.3
DHCP lease state 10.165.5.2 68:7f:74:8b:3d:d7"
14 2014/09/22 10:49:08.90 EDT MINOR: DEBUG #2001 vprn2005 SHCV
"SHCV: Periodic Check
2/1/nat-out-ip:2049.3
DHCP lease state 10.165.5.2 68:7f:74:8b:3d:d7"
15 2014/09/22 10:49:18.90 EDT MINOR: DEBUG #2001 vprn2005 SHCV
"SHCV: Periodic Check
2/1/nat-out-ip:2049.3
DHCP lease state 10.165.5.2 68:7f:74:8b:3d:d7"
16 2014/09/22 10:49:28.90 EDT MINOR: DEBUG #2001 vprn2005 SHCV
"SHCV: Connectivity Lost
2/1/nat-out-ip:2049.3
DHCP lease state 10.165.5.2 68:7f:74:8b:3d:d7"
17 2014/09/22 10:49:30.00 EDT MINOR: DEBUG #2001 vprn2005 PIP
"PIP: DHCP
instance 5 (2005),
transmitted DHCP Boot Request to 10.0.0.1 Port 68
H/W Type: Ethernet(10Mb) H/W Address Length: 6
ciaddr: 10.165.5.2 yiaddr: 0.0.0.0
siaddr: 0.0.0.0 giaddr: 0.0.0.0
chaddr: 68:7f:74:8b:3d:d7 xid: 0x0
DHCP options:
[53] Message type: Release
[54] DHCP server addr: 10.0.0.1
[255] End
"
Conclusion
The 7750 SR WLAN-GW can support many WiFi Offload architectures, including open SSID with portal authentication. WiFi Offload functions such as terminating GRE tunnels or subscribers can be performed in separate routing instances, if required. IP addresses can be assigned from an external or local source and routing can be performed using NAT, by connecting the UE routing instance directly to the Internet, or by leaking routes to other routing instances. Using http-redirect, a web portal can be used to allow users to log in to a paid service or to accept the terms of service for a free WiFi service. Several show commands and debug options are available to help the operator monitor and troubleshoot the solution.